Security company reports multiple Tesla car hacking methods and wins 66 million yen prize

With the advent of electric vehicles (EVs) and self-driving cars, cars with the ability to connect to the Internet are becoming more popular. At an event aimed at improving automobile cybersecurity held in Tokyo, Japan, multiple methods of cyberattacking Tesla cars were reported, and a security company won a large prize.
Tesla hackers win big at first Pwn2Own automotive hack fest • The Register
Pwn2Own Automotive Day 1: 3 vulnerability chain attacks against Tesla, remote attack demo, and other highlights - VicOne
https://vicone.com/jp/blog/pwn2own-automotive-day-1-a-3-bug-chain-against-a-tesla-a-remote-attack-demo-and-other-highlights
Pwn2Own Automotive Day 2: Multiple vulnerability chain attacks, second attempt on Tesla cars, and other highlights - VicOne
https://vicone.com/jp/blog/pwn2own-automotive-day-2-multiple-multi-bug-chains-a-second-tesla-attack-and-other-highlights
Pwn2Own Automotive Day 3: EV chargers take center stage and the contest's first Master of Pwn is born - VicOne
https://vicone.com/jp/blog/pwn2own-automotive-day-3-ev-chargers-take-the-front-seat-and-the-contest-crowns-its-first-master-of-pwn
With the evolution of connected cars , which have the ability to constantly connect to the Internet, cyberattacks targeting these cars are increasing. The world's first event ' Pwn2Own Automotive ' to strengthen automobile cybersecurity was held in Tokyo for three days from January 24th to 26th, 2024. The event is hosted by VicOne, a subsidiary of security software developer Trend Micro, which specializes in connected car security services.
Researchers from Synacktiv , a French security company, also participated in the event, and successfully conducted a chain attack using multiple vulnerabilities, raising $300,000 (approximately 44 million yen) on the first day, and on the second day. He won a prize of $100,000 (about 15 million yen) on the first day, and $20,000 (about 3 million yen) on the third day. Furthermore, because Synacktiv won all four categories of Pwn2Own Automotive (Tesla, in-vehicle information entertainment, electric vehicle charger, and operating system), it won the 'Master of Pwn' award given to the winner of the hacking competition. As a result, the total prize money at the event was 450,000 dollars (about 66 million yen).
Below is the Master of Pwn ranking, and you can clearly see that Synacktiv was the winner with a large difference in both earned points and prize money from 2nd place and below.

Among the chain attacks demonstrated by Synacktiv, the one that won the most prizes was `

In another chain attack, two vulnerabilities were used to successfully cyber-attack the Ubiquiti charging station
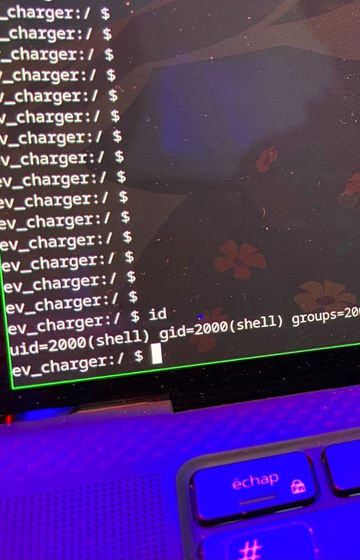
Since most of the vulnerabilities reported on Pwn2Own Automotive are newly reported zero-day vulnerabilities, few details of the chain attack have been revealed.
In addition, Pwn2Own Automotive reported 49 automobile-related zero-day vulnerabilities, and a total of more than 1.3 million dollars (approximately 190 million yen) was awarded to the discoverer.
Related Posts:







