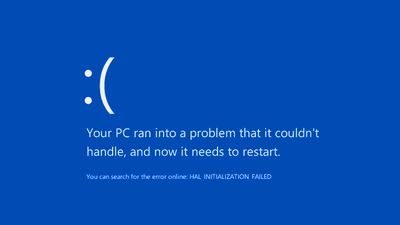
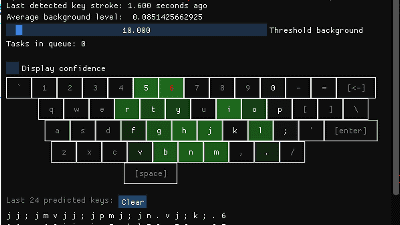
Research results that it is possible to guess the input content with 93% accuracy from the keyboard sound picked up by the microphone during Zoom, and 95% for smartphones

A British research team announced that it was possible to steal input content with 95% accuracy from the sound of the MacBook Pro keyboard recorded with the microphone built into the smartphone. Since the data could be reproduced at a rate of 93% even from the contents of the video conference recording, the technology to steal passwords and important data using sound due to the progress of machine learning 'Acoustic
[2308.01074] A Practical Deep Learning-Based Acoustic Side Channel Attack on Keyboards
https://arxiv.org/abs/2308.01074
New acoustic attack steals data from keystrokes with 95% accuracy
https://www.bleepingcomputer.com/news/security/new-acoustic-attack-steals-data-from-keystrokes-with-95-percent-accuracy/
In a paper published on the preprint server arXiv on August 3, 2023, a research team led by Joshua Harrison of the University of Durham, England, used keyboard keystroke data as training data for a deep learning model. We have also developed a technology to infer input content from the sound of keystrokes.
For data collection, the latest 13-inch MacBook Pro was used at the time of writing the article, and the sound of pressing 36 keys 25 times each was recorded with an iPhone 13 mini placed 17 cm away. Below is a picture of the recording environment where the sampling took place.

The research team then converted the collected data into
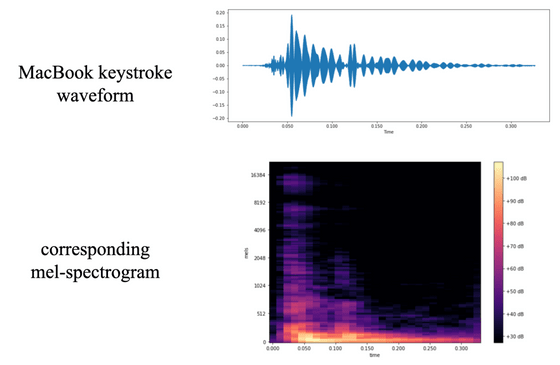
The images obtained in this way were subjected to data processing to reinforce the signal, and then used to train the image recognition model 'CoAtNet'.
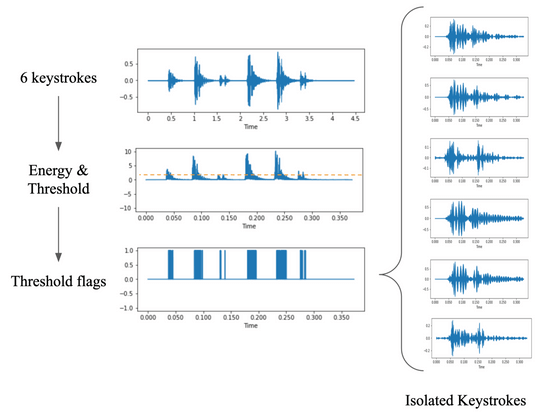
And as a result of measuring the accuracy of the deep learning model after training, it was confirmed that CoAtNet was able to determine the entered key with 95% accuracy. Also, when we conducted a similar experiment with sounds collected by the video conferencing tool Zoom, we also achieved a high accuracy of 93%.
Techniques for guessing key inputs from keystroke sounds are progressing, and another
In their paper, the researchers suggested that users wary of acoustic side-channel attacks (ASCA) should change their typing practices and use passwords made up of random strings instead of words. bottom.

Also, as a fundamental defense measure, it is proposed not to type important information during a video conference and to mute the microphone while typing if unavoidable. Furthermore, it is also effective to avoid password input itself by using biometric authentication such as fingerprints and using a password manager.
BleepingComputer, an IT news site that covered the findings of this study, said, ``It's important to remember that this attack model has been proven to be very effective even against very quiet keyboards, so it's not suitable for mechanical keyboards. It is difficult to think that even if you cover it with a soundproof sheet or change to a membrane keyboard, it will be effective.'
Related Posts:
in Security, Posted by log1l_ks