It was discovered that a driver certified by the Windows Hardware Developer Program was being exploited for malware signatures

A driver certified by Microsoft's
ADV220005 - Security Update Guide - Microsoft - Guidance for Exploitation of Microsoft Signed Drivers
https://msrc.microsoft.com/update-guide/vulnerability/ADV220005
Signed driver malware moves up the software trust chain – Sophos News
https://news.sophos.com/en-us/2022/12/13/signed-driver-malware-moves-up-the-software-trust-chain/
I Solemnly Swear My Driver Is Up to No Good: Hunting for Attestation Signed Malware | Mandiant
https://www.mandiant.com/resources/blog/hunting-attestation-signed-malware
Driving Through Defenses | Targeted Attacks Leverage Signed Malicious Microsoft Drivers - SentinelOne
https://www.sentinelone.com/labs/driving-through-defenses-targeted-attacks-leverage-signed-malicious-microsoft-drivers/
Microsoft digital certificates have once again been abused to sign malware | Ars Technica
https://arstechnica.com/information-technology/2022/12/microsoft-digital-certificates-have-once-again-been-abused-to-sign-malware/
Microsoft-signed malicious Windows drivers used in ransomware attacks
https://www.bleepingcomputer.com/news/microsoft/microsoft-signed-malicious-windows-drivers-used-in-ransomware-attacks/
Microsoft reportedly received reports from companies such as SentinelOne, Mandiant, and Sophos on October 20, 2022 about attacks that exploit drivers certified by the Windows Hardware Developer Program. Investigation into this activity revealed that multiple developer accounts in Microsoft's Partner Center were involved in submitting malicious drivers to be signed by Microsoft. Microsoft said it suspended the account that did this in early October after it found an attempt to submit a malicious driver to get it signed on September 30, 2022.
According to the Microsoft Threat Intelligence Center investigating this incident, drivers certified by the Windows Hardware Developer Program to facilitate intrusion activities such as ransomware deployment after exploiting vulnerabilities. is likely to have been exploited to sign malware.
Microsoft released a Windows security update to revoke the certificate of the affected files and suspended the partner's seller account. In addition, Microsoft has also revealed that it has implemented a blocking detection feature in Microsoft Defender since version 1.377.987.0 to protect users from activities that exploit the vulnerability.

In this reported incident, it was reported that the attacker already had administrative privileges prior to using the driver. Technology media BleepingComputer points out that obtaining elevated privileges may allow drivers to perform various malicious tasks that are not normally permitted. This 'various malicious tasks' specifically include 'terminating security software' and 'deleting protected files'.
Starting with Windows 10, Microsoft requires
Specifically, the attacker seems to have used a toolkit consisting of two components, the loader 'STONESTOP' and the kernel mode driver 'POORTRY', to carry out the BYOVD attack . According to Mandiant and SentinelOne, STONESTOP is a user-mode application that attempts to terminate endpoint security software processes on a device, and some variants of STONESTOP include the ability to overwrite or delete files. About. Normally, security software processes are protected from tampering by applications, but STONESTOP seems to be able to terminate Windows services and security software processes by loading POORTRY signed by Microsoft. .
SentinelLabs, SentinelOne's security research center, points out that ``STONESTOP not only acts as a POORTRY loader or installer, but also as an orchestrator that indicates to the driver what action to take.'' Below is an image of the POORTRY driver that abuses Microsoft's signature.
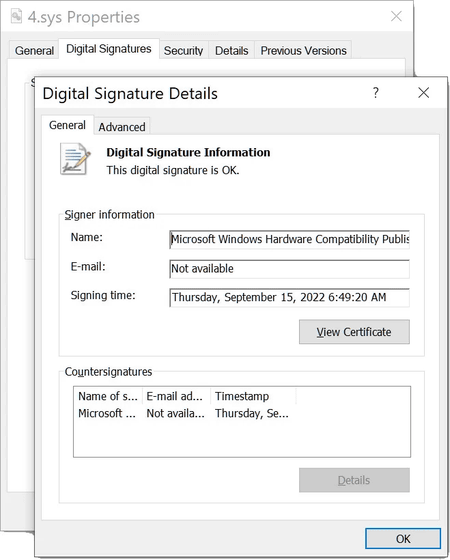
For attackers using the toolkit, Sophos' security team announced that they were successful in terminating the attack in incident response operations before delivering the final payload. Sophos said that the series of attacks was 'highly likely to be a Cuban-derived ransomware attack' and explained that 'a variant of this malware was used by Cuban hackers.'
SentinelOne has seen toolkits containing STONESTOP and POORTRY used in attacks against telecoms, BPOs, MSSPs, and financial services businesses. This toolkit was found used in the Hive ransomware campaign against companies in the healthcare industry.
Mandiant has confirmed that a threat actor identified as UNC3944 in August 2022 utilizes a toolkit containing STONESTOP and POORTRY. This threat actor is known to carry out SIM swap attacks.
It is unclear how these threat actors gained access to Microsoft's signed toolkit, but Mandiant claims it was successful in extracting the name of the organization used to sign the drivers submitted to Microsoft. organization names.
・Qi Lijun
・Luck Bigger Technology Co., Ltd.
・XinSing Network Service Co., Ltd.
・Hangzhou Shunwang Technology Co., Ltd.
・Fuzhou Superman
・Beijing Hongdao Changxing International Trade Co., Ltd.
・Fujian Altron Interactive Entertainment Technology Co., Ltd.
・Xiamen Hengxin Excellence Network Technology Co., Ltd.
・Dalian Zongmeng Network Technology Co., Ltd.
In addition, Microsoft reported that ``Microsoft's services are not affected by this issue.In our investigation, we have not confirmed any cases where our services were affected by malicious drivers.'' In addition, we recommend installing the latest Windows Updates and keeping your antivirus and endpoint detection products up to date with the latest signatures to help prevent attacks.
Related Posts: