It turns out that an Austrian private company has launched an attack using the zero-day vulnerability of Windows and Adobe Reader

by
Microsoft's security arm, the Microsoft Threat Intelligence Center (MSTIC), said an Austria-based private company, DSIRF, used a zero-day attack on Windows and Adobe Reader to hack organizations in Europe and Central America. I reported. At the same time, several media outlets have reported marketing materials and testimony that DSIRF used Trojan horses .
Untangling KNOTWEED: European private-sector offensive actor using 0-day exploits --Microsoft Security Blog
https://www.microsoft.com/security/blog/2022/07/27/untangling-knotweed-european-private-sector-offensive-actor-using-0-day-exploits/
Wirecard: Im Rätsel um Spionage-Software führt die Spur in den Kreml --FOCUS online
https://www.focus.de/politik/vorab-aus-dem-focus-volle-kontrolle-ueber-zielcomputer-das-raetsel-um-die-spionage-app-fuehrt-ueber-wirecard-zu-putin_id_24442733. html
DSIRF: Wir en thüllen den Staatstrojaner 'Subzero' aus Österreich
https://netzpolitik.org/2021/dsirf-wir-enthuellen-den-staatstrojaner-subzero-aus-oesterreich
DSIRF is a company founded in Austria in June 2016, ostensibly pretending to be a trading business, but in reality it is engaged in election intervention, fraudulent hacking operations, information tactics abroad, etc. It was said that it was going as. In addition, DSIRF has said that it can be applied to terrorism, crime, and financial fraud by using the Trojan 'Subzero' that automatically leaks confidential data and identifies and tracks threats. According to the Austrian media Netzpolitik.org, DSIRF had a deal with Russia in the past and was active in the 2016 US presidential election, according to the reference material.
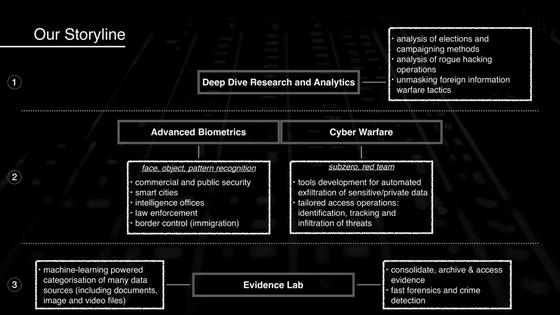
It is said that DSIRF exploited the zero-day vulnerability of Windows and Adobe Acrobat Reader for this Subzero infection. The targets of attacks that have been confirmed so far are law firms, banks, strategic consulting companies, etc. in Austria, the United Kingdom, Panama, etc.
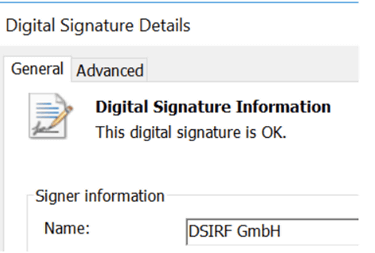
This vulnerability exploits the remote code execution of Adobe Reader and the privilege escalation vulnerability ' CVE-2022-22047 ' in the Windows client / server runtime subsystem , which causes an arbitrary signed DLL file to be loaded. It is possible. This signed DLL file was signed by 'DSIRFGmbH'. In addition, it seems that a method of pretending to be a real estate related file and downloading an Excel file containing malicious macros was also used.
MSTIC was tracking this DSIRF under the name 'KNOTWEED'. MSTIC 'discovered multiple connections between DSIRF and the exploits and malware used in these attacks, which are used in the commands, control infrastructure, and attacks used by malware that links directly to DSIRF. I have a DSIRF-related GitHub account, a certificate issued to DSIRF, which shows that Subzero is due to DSIRF. '
DSIRF has appointed Michael Harms, the managing director of the Eastern European Economic Commission , as a political and trade adviser. 'DSIRF is a member of the Eastern European Economic Commission. The Eastern European Economic Commission is not using DSIRF products and was unaware of Subzero,' said Hames.
MSTIC calls private-sector cyberattackers PSOAs (Private Sector Attackers). According to MSTIC, there are two types of PSOA business models: selling malicious tools to customers and leaving them to use, and PSOA itself performing hacking activities. MSTIC sees DSIRF selling Subzero to its customers while also using its infrastructure to attack, combining the two business models to develop its business.
Related Posts:
in Security, Posted by log1i_yk







