Microsoft withdrew without notifying users of the 'disable macros in Office files such as Excel and Word' specification

In February 2022, Microsoft announced that it would change to a specification that blocks macros created with
Helping users stay safe: Blocking internet macros by default in Office --Page 2 --Microsoft Tech Community
https://techcommunity.microsoft.com/t5/microsoft-365-blog/helping-users-stay-safe-blocking-internet-macros-by-default-in/
Microsoft rolls back decision to block Office macros by default
https://www.bleepingcomputer.com/news/microsoft/microsoft-rolls-back-decision-to-block-office-macros-by-default/
Microsoft rollback has begun on blocking Office macros --Protocol
https://www.protocol.com/bulletins/microsoft-office-macros-rollback-security
Microsoft Office, a business software developed and sold by Microsoft, can execute macros created in a programming language called VBA to automate various tasks performed by software such as Excel and Access. However, if a malicious VBA macro is loaded in an Office file downloaded from the Internet, there is a security concern that malware will be installed on the terminal when the macro is executed.
So in February 2022, Microsoft announced that Access, Excel, PowerPoint, Visio, and Word would block VBA macros in Office files downloaded from the Internet by default. This change was rolled out on the latest channel from version 2203 released in April 2022.
Microsoft announces that macros in Office files such as Excel and Word will be disabled by default-GIGAZINE

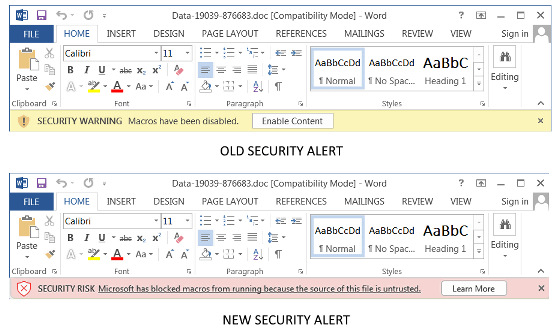
The image below compares the warning (top) that was once displayed when opening an Office file containing downloaded VBA macros with the warning (bottom) that is now displayed. In older versions, just clicking Enable Content enables macros, but in newer versions, clicking Learn More opens a page that explains the dangers of macros and how to enable them. You only need to follow the steps to enable it if you want to enable it.
Security experts also had high expectations that Microsoft's changes would significantly improve user security. However, on July 6, 2022, a Windows user said, 'Instead of the pink or red message that the macro is completely blocked, I get the old'security warning ...'message.' 'Recently, it feels like something has reverted this new default behavior ... is Microsoft Defender blocking the block?' I
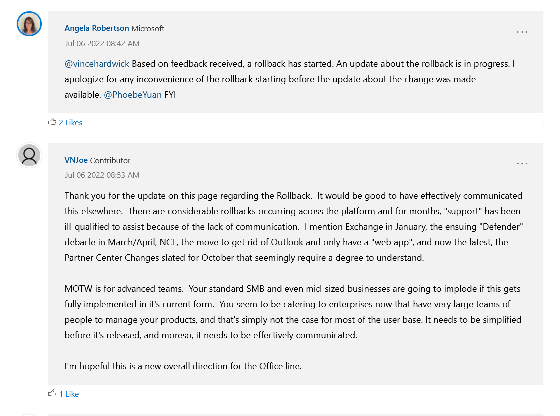
Users suspected the impact of Microsoft Defender, but Microsoft's Angela Robertson said, 'The rollback has started based on the feedback we received. Rollback updates are in progress. Changes We apologize for the inconvenience caused by the rollback being started before the update . ' It is clear that Microsoft itself has restored the specifications.
Users have complained about Microsoft's lack of communication about unannounced rollbacks, and some have commented asking them to share more information about rollbacks elsewhere.
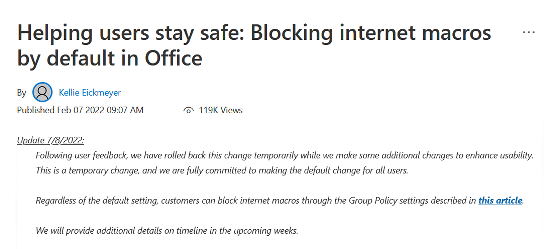
In an update on July 8th, Microsoft said, 'We received user feedback to temporarily roll back this specification and make some additional changes to improve usability. This is a temporary change and we are doing our best to make the default change for all users. '' Regardless of the default setting, customers use the group policy settings described in
Security experts have negatively commented on this rollback. Security expert Marcus Hutchins commented, 'It seems that Microsoft is protecting the work of us security experts (by doing rollbacks that weaken security).'
Looks like Microsoft has blessed us all with more job security https://t.co/1kklKv5cOS
— Marcus Hutchins (@MalwareTechBlog) July 8, 2022
Related Posts: