Benchmark test shows how fast 10 types of ransomware can encrypt files.

Gone in 52 Seconds… and 42 Minutes: A Comparative Analysis of Ransomware Encryption Speed | Splunk
https://www.splunk.com/en_us/blog/security/gone-in-52-seconds-and-42-minutes-a-comparative-analysis-of-ransomware-encryption-speed.html
Ten notorious ransomware strains put to the encryption speed test
https://www.bleepingcomputer.com/news/security/ten-notorious-ransomware-strains-put-to-the-encryption-speed-test/
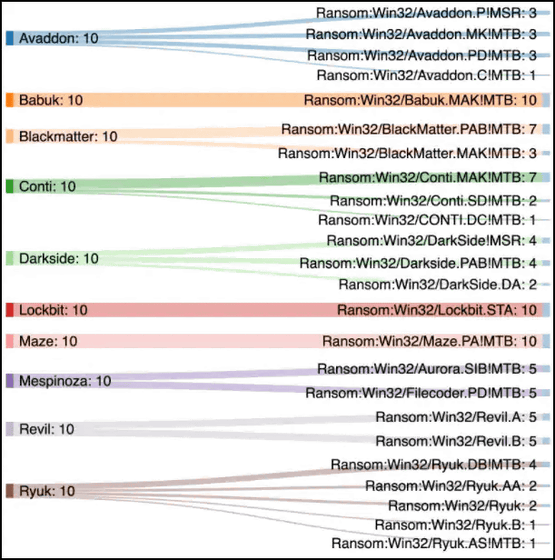
Splunk researchers have prepared 10 samples of each of the 10 types of ransomware,LockBit , Babuk , Avaddon , Ryuk, REvil, BlackMatter , Darkside , Conti , Maze , and Mespinoza . Cryptographic tests were performed on four target profiles.
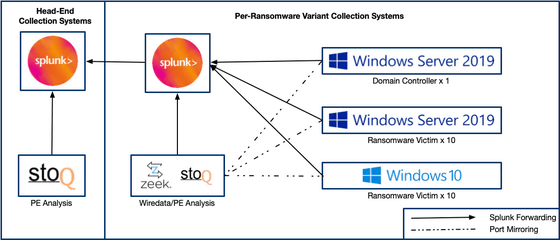
The OS of the machine used for the test is Windows 10 and Windows Server 2019, and the hardware configuration is supposed to be actually used in the enterprise. In addition, it seems that 98,561 files with a total of 53GB were prepared for encryption.
Below is a table summarizing the results of the encryption test. In testing with 100 ransomware samples, the median time it took to encrypt 98,561 files was 42 minutes and 52 seconds.
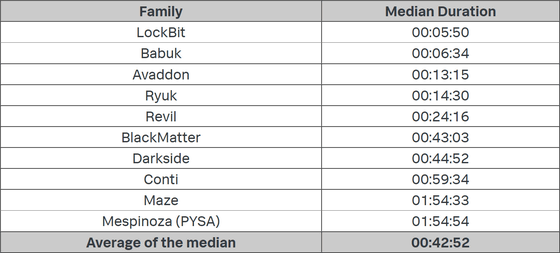
LockBit was the fastest to encrypt, with an average of 5 minutes and 50 seconds for 10 samples. LockBit was also the fastest encryption of all 100 samples, and completed encryption in just 4 minutes and 9 seconds in tests under Windows Server 2019.
In addition, Mespinoza took the longest time on average for 10 samples, with a record of 1 hour 54 minutes 54 seconds. Also, the one that took the longest time in the whole sample was the Babuk sample, which recorded a time of 3 hours 35 minutes 8 seconds in the test under Windows 10.
According to Splunk, it takes an average of three days after infection to detect ransomware activity. Since most ransomware was successfully encrypted within an hour of infection in the results of this experiment, Splunk claims that 'it is unrealistic to detect ransomware and deal with it before it is encrypted.' However, companies should focus on preventing ransomware infections rather than responding to incidents.
Related Posts:
in Security, Posted by log1i_yk