Until you track down the mysterious Raspberry Pi set up by the company and find out the perpetrator
The curious case of the Raspberry Pi in the network closet
https://blog.haschek.at/2019/the-curious-case-of-the-RasPi-in-our-network.html
Christian runs a company called Haskek Solutions that provides security services with his father. One day, my father, who works in the client's office, sends me a photo with the message 'What's this?'

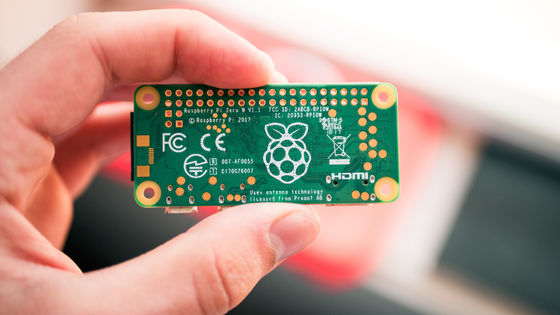
This mysterious Raspberry Pi was discovered in the client's network closet. Christian asks his father to take a picture of the Raspberry Pi and keep it out of the network closet.
The Raspberry Pi installed in the network closet is specifically the 1st generation Raspberry Pi model B. A USB dongle (left) and an SD card with a capacity of 16GB (right) were inserted into this.

At the time of discovery, Christian thought that this Raspberry Pi was 'installed by someone in the company for fun.' Therefore, ask anyone who has access to the network closet where the Raspberry Pi was installed if they have any idea of the mysterious Raspberry Pi. It seems that only four of the manager, office manager, Christian, and a colleague of Christian were able to access the network closet, and all of them answered, 'I have no idea about Raspberry Pi.'
So, Christian asks for insights on

Next, analyze the image saved on the SD card inserted in the Raspberry Pi. There are several filesystem folders on the SD card, most of them
Furthermore, in this, you will find the data written as 'resin'.
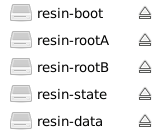
This 'resin' is a paid IoT service (renamed to balena at the time of article creation) that creates an image for an IoT device and deploys the device so that it can be updated and retrieved with the service. something like. Resin can also install a VPN on your device to securely transfer the collected data.
Then I found a file called 'config.json' in the folder labeled 'resin-boot'.
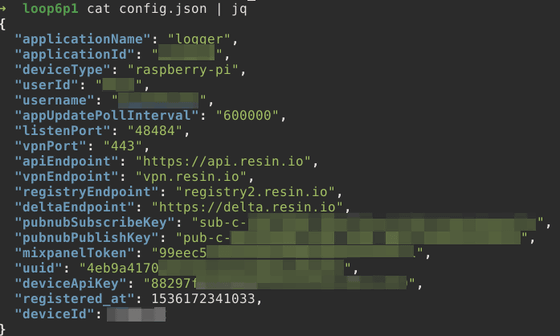
Examining this JSON file reveals that the application deployed to resin is called a 'logger'. In addition, the user ID that seems to be associated with the resin account, that the device is using a VPN via port 443, and that 'registered on May 13, 2018' (specifically what? It is unknown whether it was registered timing).
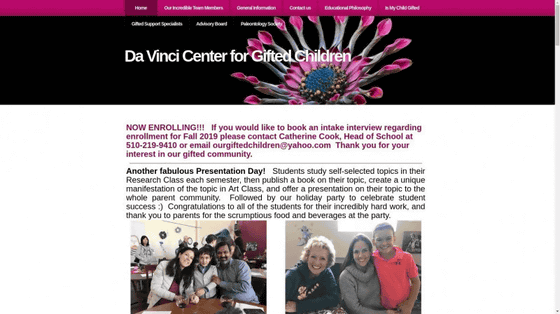
When I searched Google for the user ID found in the JSON file, I found a person with the same name at the same location as the company where Raspberry Pi was found. This person was featured in a feature article entitled 'Talented Children' published in 2001, 'I got the same person's name and address information from this article' and 'Multiple user names.' Keep in mind that the username may have been used by someone other than the person mentioned in the article, as it may be used by people, 'says Christian.
The SD card didn't seem to store any data that would have been collected from the network, but you'll find a very obfuscated Node.js app. However, 'I couldn't know exactly what the app was doing,' Christian said. However, it is clear that the Node.js app seems to be communicating via a serial connection to the USB dongle. In addition, Mr. Christian speculates that 'it was used to collect the movement and profile of Bluetooth and Wi-Fi compatible terminals around the network closet, and Wi-Fi packets.'
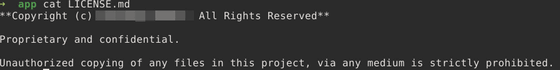
In addition, Christian found the 'LICENSE.md' file for the Node.js app. In the file with this license information, I also found the name of the company that seems to be the developer of the Node.js app.
Another interesting discovery that Christian mentions is a file called 'resin-wifi-01' found in the path '/ root-overlay / etc / NetworkManager / system-connections /'. This file contains the Wi-Fi
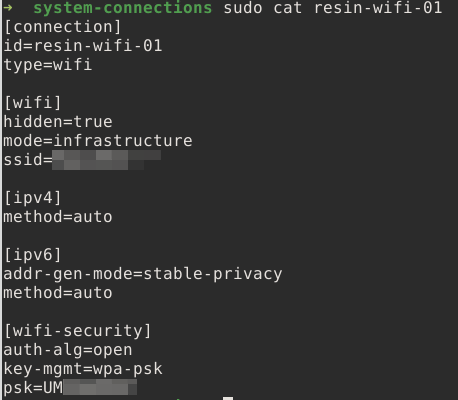
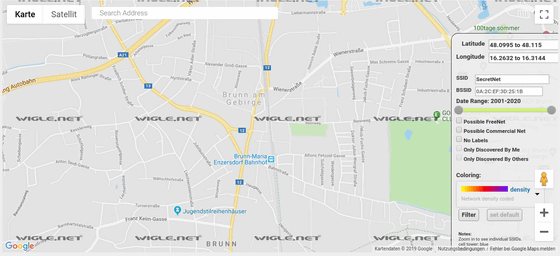
Then, by searching for this Wi-Fi credential with WiGLE , we succeeded in identifying the address of the person who seems to be the owner of the mysterious Raspberry Pi.
In addition, check the DNS logs to determine the exact date and time the Raspberry Pi first connected to your corporate network. Then check the RADIUS log to see which employees were in the company at the time. Then, it becomes clear that the employee account that should have been deactivated in the company at that time was trying to connect to Wi-Fi and got an error message. After investigating this, it was found that the administrator of the corporate account had made a transaction with a former employee and made the deactivated account available.
It seems that he is not directly involved because the processing after this was outside the work of Mr. Christian. However, he wrote, 'The company didn't want to take care of this, so I fired the person and made a move.'
Related Posts:
in Security, Posted by logu_ii