What is the workaround for an attack that reveals a vulnerability that allows you to obtain administrator privileges from the Windows installer?

It turned out that the installer for installing software on Windows is vulnerable to gaining administrator privileges. According to the discoverer, there is no fundamental solution other than waiting for Microsoft's patch. At the time of writing the article, attacks using the discovered vulnerabilities have already been confirmed, and sufficient caution is required.
GitHub --klinix5 / InstallerFileTakeOver
Malware now trying to exploit new Windows Installer zero-day
https://www.bleepingcomputer.com/news/security/malware-now-trying-to-exploit-new-windows-installer-zero-day/
Cisco Talos Intelligence Group --Comprehensive Threat Intelligence: Attackers exploiting zero-day vulnerability in Windows Installer — Here's what you need to know and Talos' coverage
http://blog.talosintelligence.com/2021/11/attackers-exploiting-zero-day.html
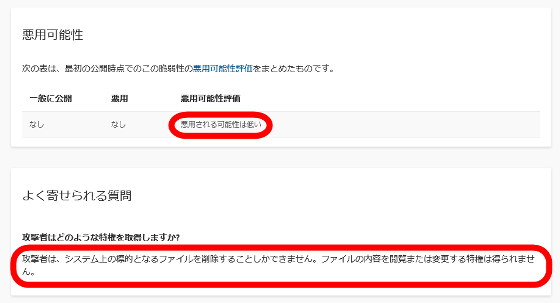
Security researcher Abdelhamid Naceri discovered a vulnerability that could allow Windows administrator privileges. Naceri discovered a vulnerability related to the installer and reported it to Microsoft, which registered the vulnerability as 'Windows Installer Privilege Elevation Vulnerability (CVE-2021-41379)' on November 9, 2021. Did. Microsoft wrote about the threat of CVE-2021-41379, 'Attackers can only delete targeted files on the system. They do not have the privilege to view or modify the contents of the files.' It is unlikely that it will happen. ' CVE-2021-41379 should have been fixed in the security update released on November 10, 2021.
However, Naceri analyzed the fix by Microsoft and found that it wasn't fixed correctly. In addition, the threat of the vulnerability was more serious than Microsoft expected, revealing that an attacker could gain administrative privileges on Windows. Mr. Naceri has released a proof-of-concept code that enables acquisition of administrator privileges on GitHub, and in the
If you execute the proof-of-concept code 'InstallerFileTakeOver.exe' with only normal user privileges ...
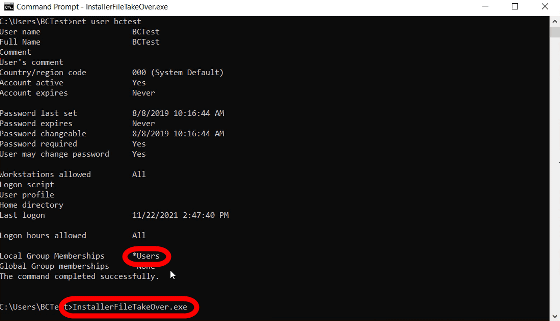
I have acquired administrator privileges.
Naceri reports on Twitter that he tried to take action by changing Group Policy but failed. 'The best workaround at the time of writing this post is to wait for Microsoft to release a patch,' Naceri said in a post that published the proof-of-concept code.
It's really unfortunate how the issue cannot be mitigated without a patch from Microsoft.
— Abdelhamid Naceri (@ KLINIX5) November 24, 2021
I have attempted to mitigate the issue by prohibiting rollback in group policy.
However, the result was just worse. The installer ignored the flag and made the bug easier to exploit. Https://t.co/Tz1HHs5eS7 pic.twitter.com/iWXKTNslOA
'This vulnerability affects all versions of Microsoft Windows, including fully patched Windows 11 and Windows Server 2022,' Naceri said in an official blog from security company Cisco. It emphasizes the breadth of the impact of the vulnerabilities found. In addition, 'We have already detected malware that is trying to exploit this vulnerability,' revealing that the vulnerability in question has already been used in the attack.
Related Posts:







