Agricultural machinery manufacturers point out that hacking measures are too vulnerable, and there is a possibility of a food crisis due to cyber attacks

At the developer conference '
Farm equipment security at DEF CON 29 | Kaspersky official blog
https://www.kaspersky.com/blog/hacking-agriculture-defcon29/42402/
Leaky John Deere API's: Serious Food Supply Chain Vulnerabilities Discovered by Sick Codes
https://sick.codes/leaky-john-deere-apis-serious-food-supply-chain-vulnerabilities-discovered-by-sick-codes-kevin-kenney-willie-cade/
Kevin Kenny , a member of the white hacker group Sick.Codes , announced the method of unauthorized access to Deere & Company. Mr. Kenny initially planned to acquire a developer account for the service developed by Deere & Company and verify unauthorized access. However, Kenny forgets the username of the account he created. So, when Mr. Kenny entered multiple user names that came to mind on the account creation screen, complicated authentication was not required and he was able to check 'whether the user name is already used' many times. matter. From this, Kenny thought, 'You can search for an unlimited number of usernames on the Deere & Company account creation page.'
Kenny analyzed Deere & Company's account creation API to test the hypothesis. As a result, we succeeded in creating a script that continuously executes the API that searches for the user name. Using that script, I searched for the company names of 1000 companies that are likely to have a Deere & Company account, and in about 2 minutes, 192 of the 1000 companies were used as user names. I was able to get the result that 'it has been done'.
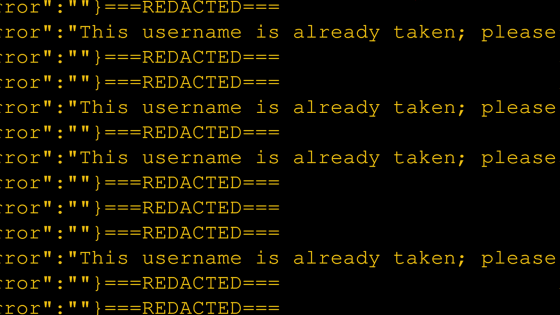
Generally, the account creation system introduces a mechanism to prevent the above-mentioned brute force search. However, there is no such mechanism in Deere & Company. In addition, when Mr. Kenny tried to report the above problem to Deere & Company, the vulnerability reporting process was not clear and he had to interact with the person in charge many times. Mr. Kenny points out that Deere & Company's security measures, including a series of exchanges, are vulnerable.

According to Kaspersky, agricultural equipment developed in recent years is made so that various parts can be remotely controlled. Therefore, if agricultural machinery or systems are hacked, 'set the amount of chemical fertilizer sprayed hundreds of times as much as usual and make the soil unusable for several years.' ' Remotely operate the combine to cut the wire. Attacks such as 'disable equipment and interrupt the harvesting process' are possible. Kaspersky warns that such attacks not only damage agricultural machinery owners, but can also lead to a national food crisis.
Related Posts:
in Security, Posted by log1o_hf