An incident occurred in which Google displayed a fake official site of the browser 'Brave' equipped with an ad blocking function at the top of the search results

A malicious attacker
With help from Google, impersonated Brave.com website pushes malware | Ars Technica
https://arstechnica.com/gadgets/2021/07/with-help-from-google-impersonated-brave-com-website-pushes-malware/
Brave is a Chromium- based web browser that comes standard with the ability to automatically block ads on your pages. Brave's ad blocking feature automatically hides high-load ads that slow down performance, which also speeds up web page loading.
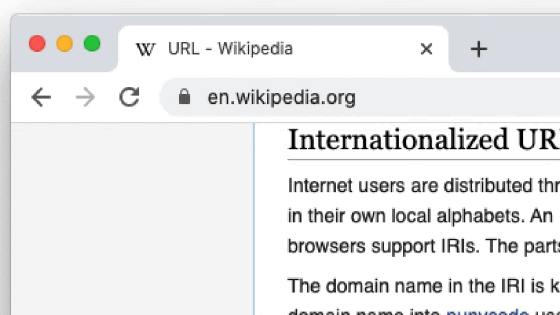
An incident occurred in which a 'fake official website' that imitated Brave's official website came to the top of Google search. This fake official site uses a character encoding for domain names called Punycode to make the URL look like the real 'brave.com' 'bravė.com (e is the Lithuanian alphabet ė ). I was disguised as '' and deceived the user. Below is a screenshot of the fake official website.
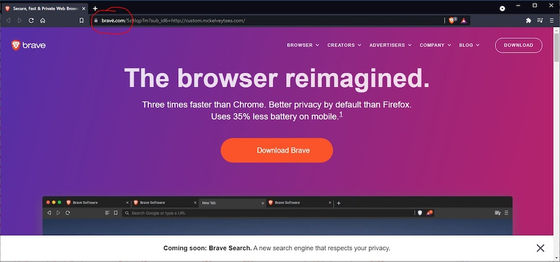
This fake official site almost completely mimicked the real official site, but when you click the 'Download Brave' button to download the Brave client, an ISO with malware called 'Arech Client' and 'Sectop Rat' It was a mechanism to download the file. These two types of malware
The reason why Google displayed this fake official site at the top of the search results is that the fake official site used 'Google Ads'. The following is the actual evidence.

In this example, the distributor of the fake official website is 'mckelveytees.com', which is the domain of apparel brands centered on work clothes.
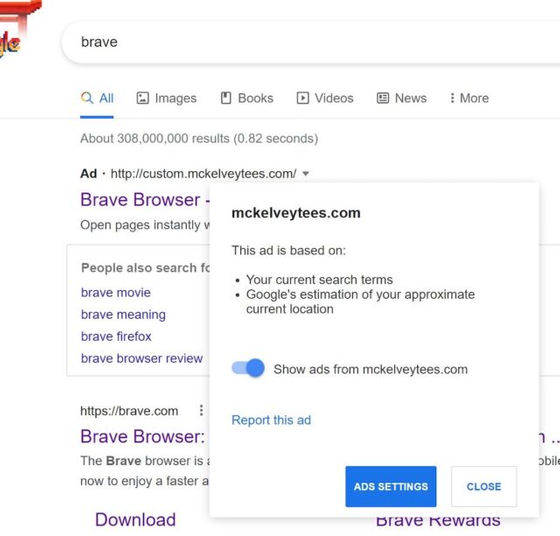
When actually clicking the fake official site from Google search, it was said that it was finally reached to 'bravė.com' via multiple intermediate domains. According to the survey, other fake official websites using similar techniques are 'screēncast.com', 'flīghtsimulator.com', 'ēxodus.com', 'tradingvīew.com', 'torbrōwser.com', 'tēlegram.com' and 'sīgnal'. '.com' etc. have been confirmed, and it has become clear that a fake official website was also created for privacy-specific messenger software Telegram and Signal.
Regarding this attack method, IT news site Ars Technica said, 'A domain using Punycode can also issue a valid TLS certificate, so there is a risk that even people with high security awareness will be fooled. 'Unfortunately, there is no clear way to avoid this attack, and you need to scrutinize the URL displayed in the address bar.'
In addition, the fake official site 'bravė.com' in question has already been excluded from Google ads, and it seems that it will not come to the top of the search results.
Related Posts:
in Web Service, Security, Posted by darkhorse_log