A security company explains how to steal information from a PC protected by 'TPM' which is essential for Windows 11

A security chip called the
From Stolen Laptop to Inside the Company Network — Dolos Group
https://dolosgroup.io/blog/2021/7/9/from-stolen-laptop-to-inside-the-company-network
One day, Dolos Group received a request from a business partner to 'attack a PC with information leakage countermeasures and check the effectiveness of the countermeasures.' The PC received by Dolos Group from the business partner ' encrypts the disk with BitLocker ' 'protects the BIOS with a password to make it impossible to change settings' ' enables Intel VT-d ' 'enables secure boot' Measures close to the ideal were taken to prevent information leakage, such as 'to make it.' Thinking that it would be difficult to extract information from this PC using software, the Dolos Group decided to use the hardware vulnerability of the TPM to attempt to break into the PC.

TPM is a security chip mounted on the motherboard and CPU, which plays a role in improving the security of the PC in terms of hardware, such as encrypting the disk with BitLocker and preventing dictionary attacks on passwords. Installation of TPM 2.0 has become a mandatory requirement. The actual TPM is summarized in detail in the following article.
What is the 'TPM' that Microsoft requires in Windows 11? Why is it essential? --GIGAZINE

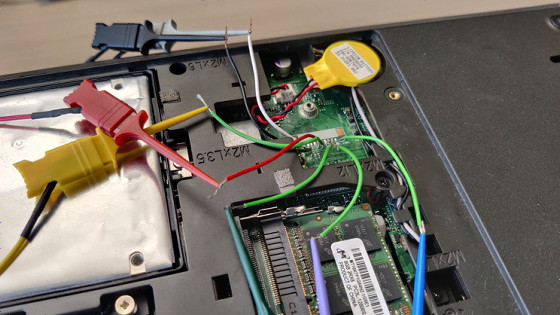
According to the Dolos Group, it is difficult to attack the TPM itself, but there is still room for attack in the part where the TPM communicates with other chips. Upon investigating the TPM of the attacked PC, it was found that the TPM and CPU were connected by a serial peripheral interface (SPI). Since the communication via this SPI is not encrypted, the Dolos Group thought it might be possible to intercept the communication between the TPM and the CPU.
To intercept the communication between the TPM and the CPU, it is necessary to connect the TPM pin and the protocol analyzer , but the TPM pin is small in size and difficult to connect. Therefore, the Dolos Group decided to connect the protocol analyzer using a large CMOS pin that shares the SPI bus with the TPM.

It looks like this when the target PC and the protocol analyzer are actually connected.
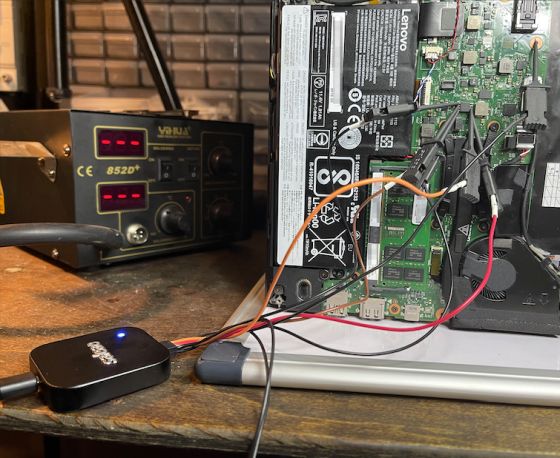
The Dolos Group extracted the BitLocker volume master key (VMK) using dedicated software based on the communication information read by the protocol analyzer.
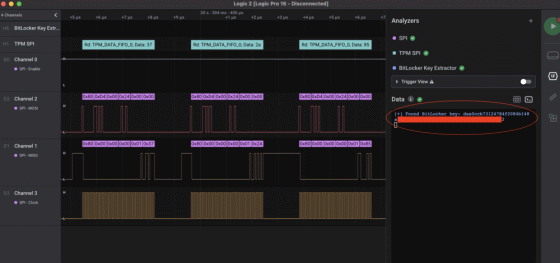
Next, Dolos Group took out the SSD from the target PC, connected it to the PC on hand, and decrypted the SSD using the VMK extracted earlier. As a result, Dolos Group succeeded in stealing all the data stored on the target PC.

In addition, Dolos Group succeeded in accessing the file server of the business partner from the target PC and browsing the contents of the file.
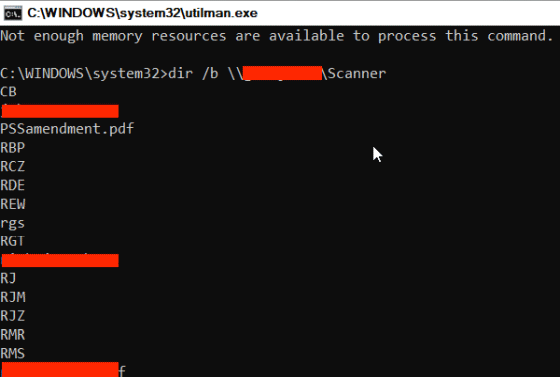
Furthermore, it succeeded in writing arbitrary data to the file server. This reveals that the Dolos Group can not only steal the data stored on the target PC, but also attack the file server to which the PC was connected.
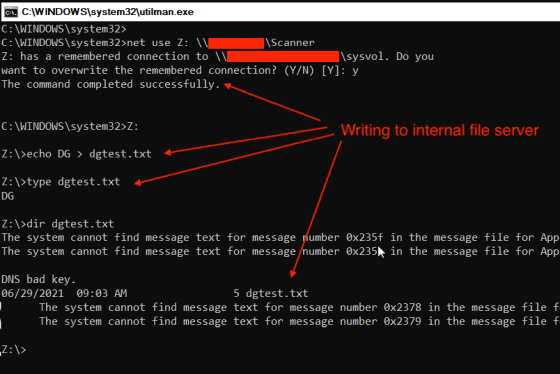
According to the Dolos Group, the most time-consuming task for extracting data this time was 'copying data from the SSD installed in the target PC to your own PC.' This attempt by the Dolos Group has shown that even a PC with the TPM required for Windows 11 can be physically stolen and the data extracted in a short amount of time.
Related Posts: