'TCC, which is a user data protection function of macOS, can be easily avoided.'

Apple's Transparency, Consent and Control (TCC) is a security framework built into macOS that protects user data from access by related applications. However, security researcher Phil Stokes reports that there is a loophole around this TCC with the 'automation' feature added from macOS Mojave.
Bypassing macOS TCC User Privacy Protections By Accident and Design --Sentinel Labs
Apple has been active in protecting user data from an early stage, implementing management features based on TCC from OS X Mountain Lion announced in 2012. The scope of this TCC has expanded with each version upgrade, and applications can hardly access user data without the permission of the user.
This TCC exists at two levels, the user level and the system level. At the user level, security settings apply only to individual users. For example, Mr. A is the access to their desktop or download folder terminal if you allow in, even if the log in even if Mr. B is the same device as the A's, you can not access the desktop or download folder of B's from the terminal.
However, if Mr. A is an administrator user and allows 'full disk access' to the terminal, Mr. A can easily access Mr. B's desktop and download folder regardless of how Mr. B sets TCC. You will be able to do it. Full disk access can be set by a user with administrator privileges, but it is very powerful because it means 'allow data access to all users of the entire system'. Note that this full disk access permission management can now be set from macOS Mojave.
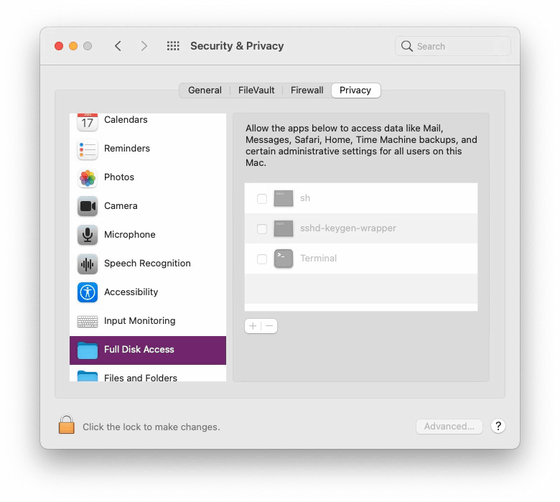
And if Mr. A grants full disk access to the terminal, Mr. B, who does not have administrator privileges, also has a local snapshot of the two command line systems '/ usr / bin / tmutil' and '/ sbin / mount'. By creating and mounting the, you will have access to the data for all users. According to Stokes, this is a full disk access specification and will not be fixed in the future.
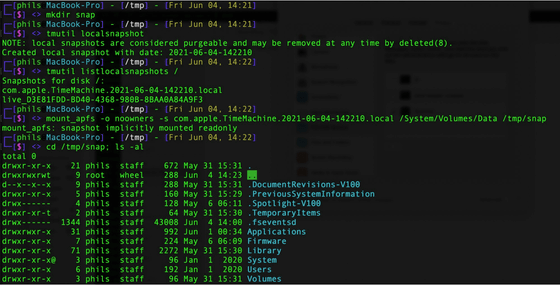
Full disk access for applications is basically managed in the system settings. And on macOS, there is only one 'application that is always allowed full disk access but is not displayed in the application list in System Preferences'.
In fact, it is an 'automation' function that allows an application to control other applications, and by letting the application control the Finder, it is possible to automatically allow full disk access.
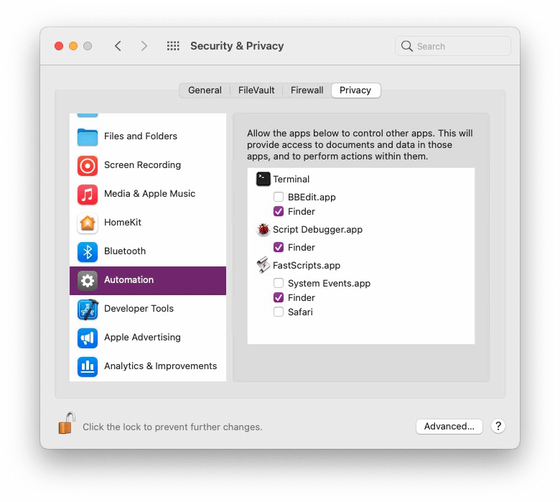
For example, a terminal normally doesn't allow full disk access, but if automation allows the terminal to control the Finder, it would allow access to data through the terminal, bypassing the TCC. I will. There are two points to avoid this TCC: 'In many cases, an app like a terminal is allowed to work with the Finder by automation' and 'A password is not required to let the app control the Finder by automation'. There is a problem, Stokes points out.
Multiple vulnerabilities related to TCC have been reported so far. For example, the malware 'XCSSET' that appeared in August 2020 exploited a method of bypassing TCC via SSH. The XCSSET vulnerability has been fixed in macOS Big Sur 11.4 released on May 24, 2021.
Mac malware 'XCSSET' that spreads via Xcode project is now available --GIGAZINE

In addition, it was found that an attacker-modified app could easily access user data due to a vulnerability caused by the TCC app verification flow. The engineer who discovered it has already been reported to Apple, but he is disappointed that he has been left unattended for half a year since he reported it.
The vulnerability sent to Apple's Bug Bounty Program turned out to be unfixed for half a year, and the discoverer published a zero-day vulnerability as 'disappointed'-GIGAZINE
Stokes said, 'Why doesn't the Finder appear on the full disk access screen? Why isn't it clear that the Finder's automation controls betray full disk access management? And why password authentication is real Is it downgraded to just asking for a simple consent to the same authority? ', And the data that macOS users think is protected by the lack of transparency of the TCC itself. It is pointed out that there is a risk of unknowingly disclosing. He also said that there was already malware that evaded TCC and that there were various other bugs, and that you should not overconfide that TCC protects your data from unauthorized access. Is urging.
Related Posts: