Hacker adds malicious node to anonymous communication 'Tor' and intercepts communication
It has been discovered that malicious hackers have added thousands of servers to the nodes used by the anonymous communication system
Tracking One Year of Malicious Tor Exit Relay Activities (Part II) | by nusenu | May, 2021 | Medium
https://nusenu.medium.com/tracking-one-year-of-malicious-tor-exit-relay-activities-part-ii-85c80875c5df
Tor security advisory: exit relays running sslstrip in May and June 2020 | Tor Blog
Thousands of Tor exit nodes attacked cryptocurrency users over the past year | The Record by Recorded Future
https://therecord.media/thousands-of-tor-exit-nodes-attacked-cryptocurrency-users-over-the-past-year/
``Tor'', a system that allows communication by anonymizing information such as IP addresses, was developed in 2003 as open software. Tor is a system that adds a relay point (relay agent) such as another computer to the communication route and encrypts everything except the exit of the access route to maintain the anonymity of the source. You can find out how Tor enables anonymous communication by reading the article below.
Easy-to-understand explanation of how anonymous communication 'Tor' works - GIGAZINE
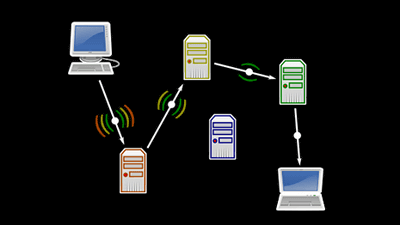
The key to anonymous communication with Tor: ``Relays'' are volunteer computers around the world running Tor software, and ordinary users can access websites through some of these relays. It has become. According to nusenu, around January 2020, hackers started adding thousands of servers as 'exit relays', one type of relay, and by February 2021, they accounted for more than 27% of exit relays. He said. Hackers are said to be identifying traffic to websites that handle virtual currency, downgrading HTTPS to HTTP and intercepting user communications using a method called SSL stripping attack.
The hacker's efforts continued for more than a year, but were thwarted several times by Tor administrators. Although the Tor team shut down servers in August 2020 and November 2020, hackers continue to be active, accounting for 27% of exit relays in February 2021. Although there were subsequent shutdowns, it was also recorded that at the beginning of May 2021, more than 1000 servers were suddenly added as exit relays. According to nusenu, as of May 5, 2021, this hacker controls 4% to 6% of exit relays, and SSL stripping attacks continue.
The Tor team says it will continue working to make the network more robust following a series of attacks.
Related Posts:
in Web Service, Security, Posted by log1p_kr