Is the ransomware attack on the QNAP NAS caused by the password hard-coded in the official backup software?

In April 2021,
Massive Qlocker ransomware attack uses 7zip to encrypt QNAP devices
https://www.bleepingcomputer.com/news/security/massive-qlocker-ransomware-attack-uses-7zip-to-encrypt-qnap-devices/
QNAP NAS devices under ransomware attack --Help Net Security
https://www.helpnetsecurity.com/2021/04/26/qnap-nas-ransomware/

A ransomware attack targeting QNAP NAS around the world was discovered on April 19, 2021, and according to computer help site Bleeping Computer , more than hundreds of damages have been reported. That thing. The ransomware used in the attack is called 'Qlocker', and hackers who gain unauthorized access to the NAS use the open source file archiver 7-Zip to archive files on the NAS in a password-protected manner. Migrate to. We know that QNAP's resource monitor shows the 7-zip command line executable '7z' while the file is locked.
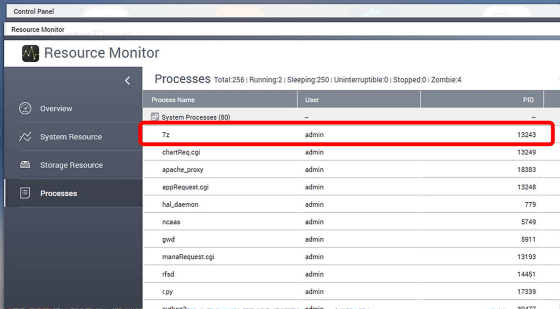
When the files on the NAS are saved in the 7-zip archive, the user will only be left with a ransom note of '!!! READ_ME.txt'. This memo
When the victim pays the specified ransom and enters a valid Bitcoin transaction ID, the ransom website will display a password to open the 7-zip archive. This password is unique to each victim and you cannot open the archive by entering the same password on other victims' devices. Due to the relatively small amount of ransom, many victims are willing to pay 0.01 bitcoins, and hackers are believed to have earned $ 260,000 in five days. I will.
In addition, on April 22, security researcher Jack Cable discovered a method to extract archived files without a password using a bug in the ransom payment site. He called on the victim on Twitter to help rescue the file, and rescued the data of about 50 people by the time the hacker responded.
Update: it looks like this may have been fixed by the ransomware operators, unfortunately. I apologize if I was not able to get to yours before it was fixed. In total decrypted around 50 keys worth $ 27k.
— Jack Cable (@jackhcable) April 22, 2021
QNAP initially believed that Qlocker exploited SQL injection CVE-2020-36195 to access an Internet-connected NAS.
However, after that, it turned out that CVE-2021-28799 , a vulnerability in QNAP software 'Hybrid Backup Sync 3 (HBS 3) ' that provides data backup / restore / synchronization functions, was likely to be exploited by Qlocker. Did. CVE-2021-28799 seems to be a vulnerability of 'inappropriate authentication of HBS 3', and it is presumed that the hacker was accessing the NAS using a backdoor account.
On a series of issues, people who actually have QNAP NAS gather at Internet forums to exchange opinions. Among them, there is an opinion that 'credentials hard-coded in the HBS 3 source code may have been misused by ransomware.'
[RANSOMWARE] 4/20/2021 --QLOCKER --Page 31 --QNAP NAS Community Forum
https://forum.qnap.com/viewtopic.php?f=45&t=160849&start=450#p788325
When the user who pointed out the problem analyzed the HBS 3 source code, they found 1215 lines of code containing the word 'walter'. There is a possibility that this 'walter' is a password that should not be included in the code. It's unclear how this password actually works, but forums suggest that it may have been misused by hackers.
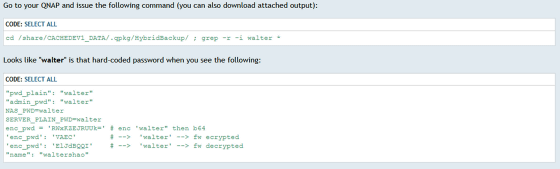
In addition, it seems that the code contained 27 email addresses '[email protected]' or '[email protected]'. QNAP has a person named 'Walter Shao' who has been a technical manager since 2013.
Related Posts:







