Vulnerabilities such as leakage of personal information have been discovered in more than 18,000 smartphone apps, and cloud service settings are incomplete.

According to a survey by mobile security service provider
Unsecured Cloud Configurations Exposing Information in Thousands of Mobile Apps
https://blog.zimperium.com/unsecured-cloud-configurations-exposing-information-in-thousands-of-mobile-apps/
Thousands of Android and iOS Apps Leak Data From the Cloud | WIRED
https://www.wired.com/story/ios-android-leaky-apps-cloud/
Saving information such as the usage status of the app and the ability for the app to access the server and inquire information in real time are one of the important designs in the development of mobile apps. According to Zimperium, a significant number of apps rely on external services such as Amazon S3 and Microsoft Azure for the cloud services needed for these features.
Cloud services have the convenience of easily saving data and accessing it from the app, but due to that convenience, there is a risk that anyone can access the data depending on the settings. Cloud service providers have published very detailed guidelines on how to protect access, but app developers may not follow them, leaving them at their default settings or misusing them. Is high, Zimperium points out.

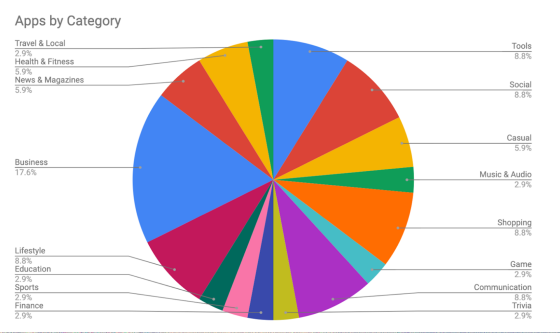
As a result of Zimperium's survey of more than 1.3 million apps, about 131,000 apps use cloud services instead of their own servers, of which about 14%, or 18,485 apps, are misconfigured. It has been confirmed that the user's personal information, password, and medical information can be easily accessed. The graph below shows the types of apps that allowed access to personal information via cloud services. There are a wide variety of apps such as music apps, game apps, and business apps, some of which have millions of users.
Zimperium also announced that it has identified cases where the developer's server infrastructure, scripts, servers, etc. are all exposed, in addition to the user's personal information. In this case, a malicious person could confirm the SSH key and was able to access the application developer's server.
Zimperium does not individually check whether the damage actually occurred, and is urging app developers to review the cloud service settings to prevent unauthorized access and information leakage.
Related Posts: