Microsoft publishes report on attack by North Korean hacker using Chrome's zero-day vulnerability

On January 25, 2021,
ZINC attacks against security researchers --Microsoft Security
https://www.microsoft.com/security/blog/2021/01/28/zinc-attacks-against-security-researchers/
Microsoft: DPRK hackers'likely' hit researchers with Chrome exploit
https://www.bleepingcomputer.com/news/security/microsoft-dprk-hackers-likely-hit-researchers-with-chrome-exploit/
Lazarus Group behind security researcher attacks --Security --iTnews
https://www.itnews.com.au/news/lazarus-group-behind-security-researcher-attacks-560380
On January 25, 2021, Google announced that new hacks targeting security researchers have been going on for months.
New campaign targeting security researchers
https://blog.google/threat-analysis-group/new-campaign-targeting-security-researchers/
The attack group builds a Twitter account of a fictitious person who has established a position in the field of vulnerability research, and after becoming a follow-follower relationship with a targeted security researcher, a social that steals information by requesting research It is said to have used engineering techniques.
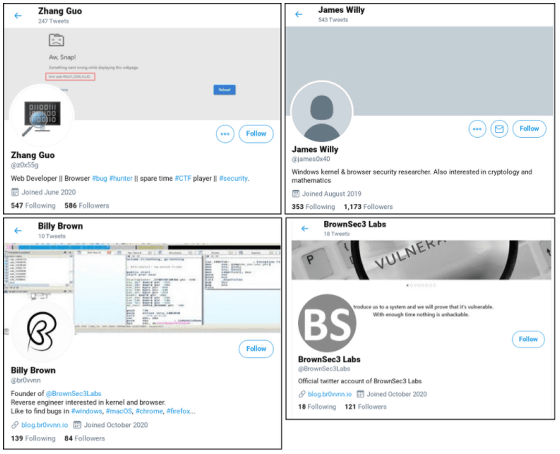
Microsoft has tracked this attack group 'ZINC' and published a report. ZINC, also known as 'Lazarus,' is believed to have been involved in crimes related to ransomware 'WannaCry' and hacking into Sony Pictures with the support of North Korea.
US prosecution for North Korean hacker involved in creating ransomware 'WannaCry' and hacking Sony Pictures-GIGAZINE

In a new hack, ZINC sent a Microsoft Visual Studio project containing a malicious dynamic link library (DLL) to security researchers, according to a Microsoft report. This DLL was executed when a researcher compiled a project, installed backdoor malware, and was configured to allow an attacker to retrieve commands and information executed on a computer.
Microsoft has also confirmed attacks using tools other than Visual Studio. Google has reported that users have been infected with malware on a website prepared by an attacker despite being 'the latest fully patched Chrome', and the attacker exploited the zero-day vulnerability. It was thought that it was done. In this regard, Microsoft states that the website contained 'exploits that exploited zero-day vulnerabilities or patch gaps.'
The attacker shared a blog post titled 'DOS2RCE: A New Technique To Exploit V8 NULL Pointer Dereference Bug' on Twitter between October 14th and 21st, 2020. Even people who have not sent a Visual Studio project from ZINC were infected with malware by clicking the link in Chrome. However, Microsoft says it has not been proven that the infection actually spread this way.
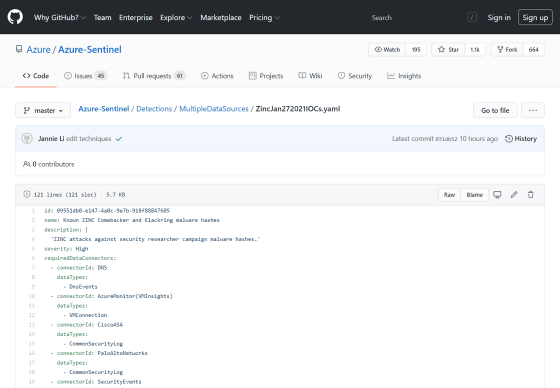
Microsoft warns that people who have visited the blog 'br0vvnn.io' operated by ZINC may have been infected with malware, and immediately scan it with anti-virus software or use a security breach indicator etc. It says it needs to be confirmed.
Azure-Sentinel / ZincJan272021IOCs.yaml at master · Azure / Azure-Sentinel · GitHub
https://github.com/Azure/Azure-Sentinel/blob/master/Detections/MultipleDataSources/ZincJan272021IOCs.yaml
GitHub --microsoft / Microsoft-365-Defender-Hunting-Queries: Sample queries for Advanced hunting in Microsoft 365 Defender
https://github.com/microsoft/Microsoft-365-Defender-Hunting-Queries/
Related Posts:
in Security, Posted by darkhorse_log