What is the 'very sophisticated cyber attack' method discovered by Google's vulnerability countermeasure team?

Google's vulnerability research team '
Project Zero: Introducing the In-the-Wild Series
https://googleprojectzero.blogspot.com/2021/01/introducing-in-wild-series.html
Project Zero conducts daily security research with the goal of 'making zero-day attacks difficult.' One way to make a zero-day attack difficult is to analyze the already known zero-day attacks, but that alone does not prevent an unknown zero-day attack. Therefore, Project Zero collaborates with Google's threat analysis group ' Threat Analytis Group (TAG) ' to search for unknown zero-day attacks. As a result, we discovered a 'very sophisticated cyberattack' in the first quarter of 2020.
According to Project Zero, a 'very sophisticated cyberattack' invades a target device using a watering hole attack that infects the target device with malware by tampering with the website visited by the attack target. , It will execute various codes. Furthermore, it is said that different attack methods ( exploits ) will be executed depending on the OS installed in the attack target device.
The image below outlines the cyberattacks discovered this time. In this attack, multiple websites are first tampered with and loaded with malware, and then it is recognized whether the device infected with the malware is equipped with Windows or Android. Then run the exploits made for each OS.
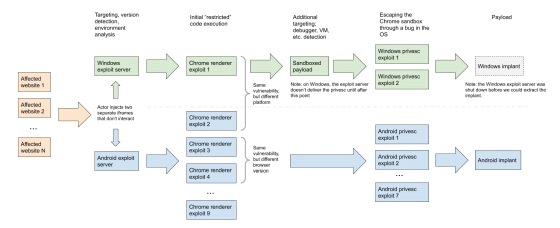
These exploits exploit multiple vulnerabilities, including the Google Chrome zero-day vulnerability, to extract information from potential attack targets in the early stages of an attack. Based on the dozens of types of information acquired, the attacker decides whether to continue or suspend the attack on the candidate attack target, and if the attack continues, three zero-day vulnerabilities including the zero-day vulnerabilities in Windows and multiple Android vulnerabilities Attempts a zero-day attack using this vulnerability.
These exploits were designed separately for each module, and were excellent in efficiency and flexibility. Project Zero also took months to analyze the exploit because the exploit consisted of large and complex code and had a large number of built-in anti-analysis systems.

Project Zero has published a detailed method of the analyzed 'very sophisticated attacks', 'By disclosing this information, many people recognize the existence of a cyber attack group with sufficient resources. I hope that. '
All the vulnerabilities found in this analysis have been fixed.
Related Posts: