What is the attack on SolarWinds' Orion Platform, which Microsoft president says is 'one of the most serious cyberattacks in the last decade?'

The SolarWinds cyberattack: The hack, the victims, and what we know
https://www.bleepingcomputer.com/news/security/the-solarwinds-cyberattack-the-hack-the-victims-and-what-we-know/
Microsoft President Breaks Down Government Systems Hack: NPR
https://www.npr.org/2020/12/19/948316348/microsoft-president-breaks-down-government-systems-hack
How US intervention'trust in untested software opened the door to hackers --POLITICO
https://www.politico.com/news/2020/12/19/how-federal-hack-happened-448602
On December 13, 2020, SolarWinds revealed that 'the Orion Platform software updates distributed in March and June 2020 may have been tampered with by a supply chain attack.' Since the Orion Platform has been adopted by US ministries and major companies, it is estimated that problematic software updates have been distributed to 18,000 companies. As of December 19, 2020, in addition to US Treasury, State Department, National Telecommunications Information Management Agency, National Institutes of Health, Department of Energy, Department of Homeland Security, National Nuclear Security Administration, and other ministries, the United States It is reported that some state governments and large companies such as Microsoft, Cisco, and FireEye were also damaged.
It turns out that a large-scale cyber attack on government agencies was approaching nuclear weapons related organizations and Microsoft-GIGAZINE

The attack in question is to access the Orion Platform build system and inject malware that adds a backdoor to a file called 'SolarWinds.Orion.Core.BusinessLayer.dll', which loads this DLL into 'SolarWinds.BusinessLayerHost'. When you execute '.exe', you can access a server that exists in a subdomain of the domain 'avsvmcloud.com' and force specific actions such as registry operations, file operations, process execution / stop, and system restart. That thing.
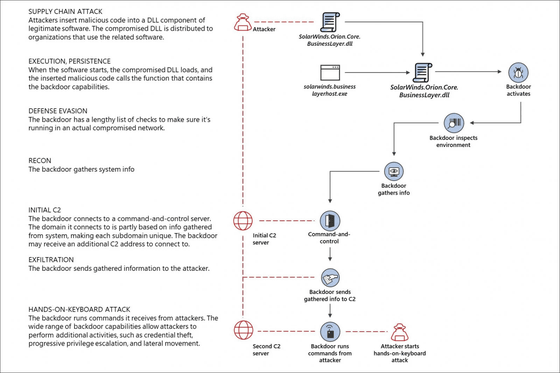
Regarding the name of this backdoor, security companies FireEye and Trendmicro named it 'Sun Burst', while Microsoft named it 'Solorigate', and Microsoft explained the technical details about this case in its blog. doing.
Analyzing Solorigate, the compromised DLL file that started a sophisticated cyberattack, and how Microsoft Defender helps protect customers --Microsoft Security
https://www.microsoft.com/security/blog/2020/12/18/analyzing-solorigate-the-compromised-dll-file-that-started-a-sophisticated-cyberattack-and-how-microsoft-defender- helps-protect /
In this case, it is unknown what kind of attack the affected organization / company was attacked by Solorigate, and experts said, 'Remote access, download and execute another malware, data Maybe it was used to steal it. ' As a countermeasure, Microsoft added a function to Microsoft Defender that 'if a DLL with an added backdoor is loaded, it will be forcibly stopped and quarantined even if the Orion Platform is running'. In addition, we urged server administrators in companies deploying the Orion Platform to perform an investigation.
The scale of the damage is unimaginable, as the Orion Platform has been adopted by many government organizations and large corporations, and it is believed that attacks have been carried out for more than nine months since March 2020. In an interview with the US news agency National Public Radio, Microsoft President Brad Smith said, 'It's considered one of the most serious cyberattacks I've seen in the last decade. The malware in question is 18,000. It is believed that it was distributed to companies, 80% of which are American organizations. The number of affected companies will continue to increase, 'he said, and the identity of the attacker was' non-Russian intelligence. There is no evidence, but it's too early to decide. '
In this case, the US parliament is discussing that 'IT companies have a weak incentive to investigate vulnerabilities in their software', 'Government agencies should invest money by strengthening security' 'Security It is reported that the proposal that 'investment in related software should be doubled' is being made.
Related Posts:
in Security, Posted by darkhorse_log






