Cloudflare, Apple and others collaborate to develop a new protocol 'Oblivious DNS over HTTPS (ODoH)'
Cloudflare and Apple have collaborated to announce a new DNS protocol, Oblivious DNS over HTTPS (ODoH) . By using ODoH, it is possible to conceal the source IP address of the client that has been confirmed from the DNS resolver so far, and improve privacy.
Improving DNS Privacy with Oblivious DoH in 1.1.1.1
Cloudflare, Apple and Fastly Create Improved, Private DNS
https://www.webpronews.com/cloudflare-apple-and-fastly-create-improved-private-dns/
Oblivious DNS-over-HTTPS --Schneier on Security
https://www.schneier.com/blog/archives/2020/12/oblivious-dns-over-https.html
DNS is an indispensable protocol for the Internet that converts domain names such as 'google.com' to IP addresses such as '8.8.8.8'. However, since ordinary DNS is not encrypted, there is a risk of spoofing and interception of communications. From the viewpoint of enhancing the security of DNS, ' DNS over TLS (DoT) ' and ' DNS over HTTPS (DoH) ', which perform DNS on TLS or HTTPS, have been attracting attention in recent years. The DNS itself is not equipped with an encryption function, but the DNS data is placed on TLS or HTTPS, which originally has an encryption function, and communication is performed to indirectly encrypt the DNS. It is beginning to spread on the Internet.
Finally Firefox announces that it will enable 'DNS over HTTPS', which encrypts communication with DNS, by default --GIGAZINE

However, even if you use DoT or DoH, the IP part, which is a lower layer protocol than TLS or HTTPS, cannot be encrypted, so there was a problem that the source IP address of the user who sent the DNS query can be confirmed from the resolver. .. To solve this problem, a new protocol jointly developed by Cloudflare, Apple, and
The specific mechanism of ODoH is as follows. DNS queries and answers are sent using HTTPS, which is similar to normal DoH, but ODoH uses a public key cryptosystem called ' Hybrid Public Key Encryption (HPKE) ' to encrypt DNS queries on the client. Send to the proxy. The proxy sends a DNS query from the client to the target, which decrypts the encrypted DNS query. The decrypted DNS query is sent to the resolver, and the resolver sends the DNS answer to the client in the reverse order of sending the DNS query.
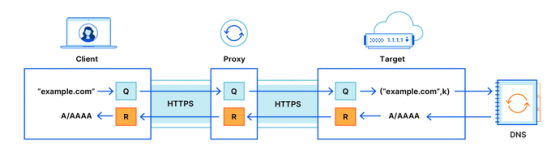
Placing a proxy between the client and the target prevents the target from knowing the client's IP address. Also, since the DNS query is encrypted between the client and the target, it is impossible for the proxy to know the contents of the DNS query. As long as both the proxy and the target do not collude, your privacy is protected. Cloudflare also explains that ODoH has the advantage of allowing clients to choose between proxies and targets.
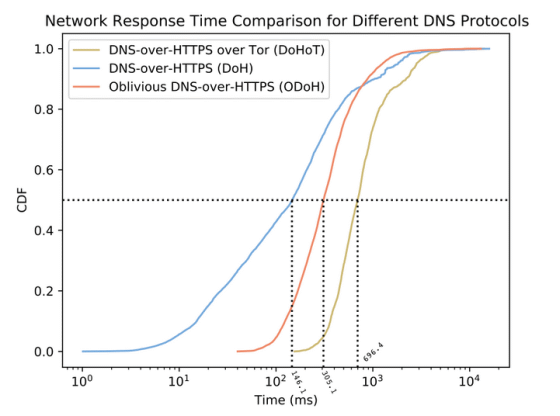
Below is a graph published by Cloudflare to show ODoH performance. The comparison targets are yellow 'DoH using Tor', blue 'normal DoH', and red 'ODoH'. The horizontal axis is the response time, and the vertical axis is the cumulative frequency to access 10,000 domains. The result is plotted. Looking at the graph, we can see that ODoH is able to respond to 50% of domains in 305.1 milliseconds, which is inferior to normal DoH but has higher performance than Tor-based DoH.
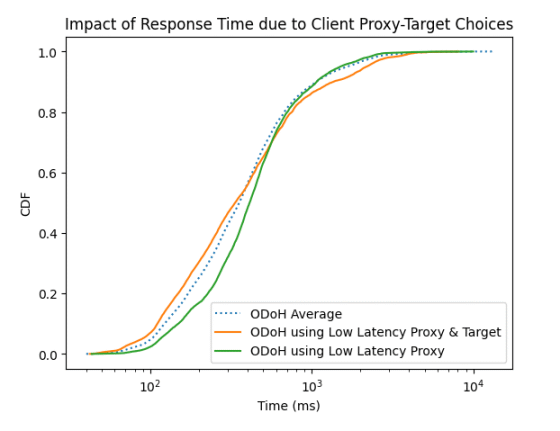
Looking at the graph that records the ODoH using 'low latency proxy and target' in orange, the ODoH using only 'low latency proxy' in green, and the average value of ODoH in blue dotted line, especially In the top 50% of responsive domains, the performance degradation is noticeable when low latency targets are not used.
In addition, Cloudflare has already released ODoH clients such as ' odoh-client-rs ' and ' odoh-client-go ', and it is possible to actually perform name resolution by ODoH. 'We hope that more operators will operate infrastructure such as proxies and targets to support ODoH, and that the client side will also support ODoH as the infrastructure is improved.'
Related Posts:






