What is the 'key' that 'benefits the entire Internet' if Google publishes it?

by
Public-key cryptography , which encrypts and decrypts data with separate keys, is an important technology that supports secure Internet communication. DKIM, which prevents spoofing of the email sender, also uses public key cryptography, and is a technology that has become so popular that it is also used in email services such as Gmail. It is common sense not to disclose the private key of public key cryptography, but Matthew D. Green , a cryptographer at Johns Hopkins University , told Google that 'DKIM's private key should be disclosed for the benefit of the entire Internet.' Claims.
Ok Google: please publish your DKIM secret keys – A Few Thoughts on Cryptographic Engineering
https://blog.cryptographyengineering.com/2020/11/16/ok-google-please-publish-your-dkim-secret-keys/
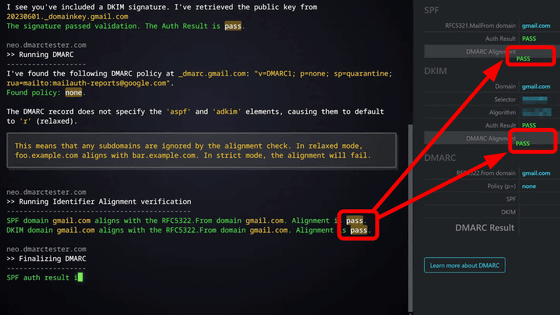
Since the sender of an email can be easily spoofed, DKIM is an authentication technology developed to prevent spoofing of the sender. DKIM is a technology that uses a public key authentication mechanism. The sender mail server registers the public key of the managed key pair in the DNS server, digitally signs the mail with the private key, and sends it. The recipient can confirm the validity of the sender by obtaining the public key from the DNS server and matching it with the electronic signature of the email.
At first glance, DKIM seems to be a perfect technology, but Mr. Green points out that there is a problem with its operation method. DKIM was originally created to 'guarantee the legitimacy of the sender only during transmission and reception in order to prevent spoofing on the mail transmission path.' However, with the current operation method, DKIM is effectively transformed into something that 'guarantees the legitimacy of the mail sender for a long period of time.'
For example, the email of John Podesta, who was in charge of elections for the Democratic nominee Hillary Clinton camp in the 2016 US presidential election, was published on WikiLeaks by hacking and used by DKIM to verify the sender. Has been done. In the 2020 presidential election, DKIM was also used to verify emails related to political suspicions of Joe Biden 's son, Hunter Biden . DKIM has even published a tool that allows you to verify the legitimacy of the email sender. DKIM, which was originally supposed to be used only during sending and receiving, is also used to verify emails received in the past.
The fact that DKIM verifies the validity of not only 'mail being sent and received' but also 'mail in the mailbox' can be said to be a failure in the original operation of DKIM. To improve this situation, Green should use the 'private key rotation function' originally implemented in DKIM. If you exchange private keys on your DNS server on a regular basis, DKIM cannot guarantee the authenticity of old mail in your mailbox. In addition, if the exchanged private key is disclosed, anyone can use the private key to spoof the sender, so verification by DKIM with the old key pair becomes meaningless, Green explains. ..
For this reason, Green argued to Google, which runs a huge email service called Gmail, that 'the old private key should be published on the Internet.' Google exchanged DKIM private keys in 2016, so if you publish your pre-2016 DKIM private key, you can at least use DKIM to validate pre-2016 emails that remain in your Gmail mailbox. You will not be able to. It is also possible to neutralize attacks by such hackers, assuming that some hackers have stolen the private key and spoofed the sender. Past DKIM private keys are not important to Google, so even a little action can have a tremendous effect.

Inappropriate operation of DKIM has been embodied in a way that people can easily understand, called 'politician leaked email verification' for the past few years, but the possibility of being used for crimes cannot be denied. .. Mr. Green is said to have received the opinion that 'the verification function by DKIM is useful', but he insists that encryption software such as GnuPG should be used for permanent guarantee. Research into new cryptographic features that complement DKIM is also underway, but the results are still a long way off, and 'Google revealing past DKIM private keys' is clearly the best solution that can be implemented right now. Green says it's a plan.
Related Posts: