There are already machines that can try 100 billion passwords per second, how to keep passwords secure?

In recent years, password leaks have been occurring one after another, and the risk of password brute force is increasing due to improvements in computer performance. Researchers at
A computer can guess more than 100,000,000,000 passwords per second. Still think yours is secure?
https://theconversation.com/a-computer-can-guess-more-than-100-000-000-000-passwords-per-second-still-think-yours-is-secure-144418
◆ Is the longer the password, the more secure it is?
Passwords began to be used in the IT field in the 1960s, but nowadays passwords are used everywhere in our lives, from PIN codes entered at ATMs to login to websites. Until relatively recently, passwords were generally 'words and phrases of 6 to 8 characters', but in recent years the minimum number of characters in passwords has tended to increase. This is to increase the 'password entropy'.
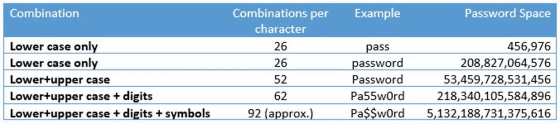
Password entropy is a measure of the 'predictability' of a password. For example, in the table below, from the top, '4 character password using only lower alphabet', '8 character password using only lower alphabet', '8 character password using only lower and upper alphabet', 'alphabet' The number of candidate character strings for each of '8-character password using lower and upper letters and numbers' and '8-letter password using lower and upper letters, numbers and symbols' is listed. You can see that as the number of password characters and the number of characters that can be used increases, the number of candidate passwords increases and it becomes difficult to predict.
However, researchers point out that it is not possible to simply think that it is safe to lengthen the password string. 'The problem with relying on password complexity is that computers can perform repetitive tasks, including password guessing, very efficiently,' the researchers said, even if passwords are complex. However, there is still a risk that the password will be
According to 2019 records , computers were able to test passwords at speeds of over 100 billion per second, allowing criminals to easily launch brute force attacks using their computers. In addition, with modern cloud-based computing, it only takes 12 minutes to break through an 8-character password, and the cost is only $ 25. Passwords are used to access sensitive data and critical systems, motivating criminals to aggressively attempt brute force attacks.
I did some math.
— TechByTom (@techbytom) February 14, 2019
Using AWS p.3 instances to calculate cost, and assuming the attacker has $ 25:
Your 8 character password will probably be cracked in 12 minutes or less.
◆ How are passwords stored?
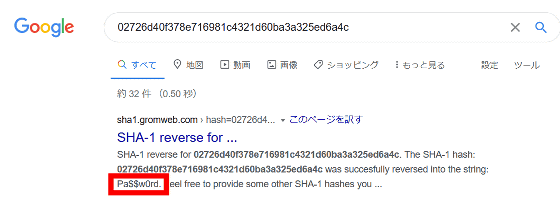
Generally, passwords are converted (hashed) to another value using a mathematical algorithm called a hash function and stored, and the hashed value cannot be restored to the original password. For example, if the password ' Pa $$ w0rd ' is hashed with the hash function SHA-1 , it will be ' 02726d40f378e716981c4321d60ba3a325ed6a4c '. When the user logs in, the password entered is also hashed and matched against the stored value.
However, there are websites that post passwords corresponding to the values hashed by a specific hash function, and searching for '02726d40f378e716981c4321d60ba3a325ed6a4c' above reveals the corresponding password 'Pa $$ w0rd'. I will do it.
In addition, the online market that sells passwords is also gaining popularity from criminals, and in some cases it is sold as a set with an e-mail address and user name. If the password itself is leaked, the length of the password does not matter.
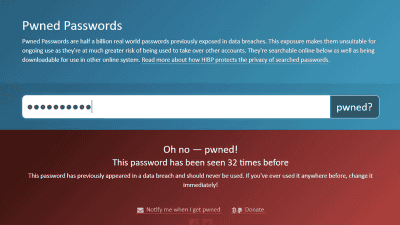
Web services that check whether your password has been leaked include 'Pwned Passwords', which allows you to check whether your password is dangerous in the past leaked data for free.
'Pwned Passwords', a service that allows you to check whether your password is dangerous in the past leaked data for free --GIGAZINE
◆ How to maintain security?
However, it has been pointed out that people are not serious about password security. Despite numerous news reports of password leaks and hacking damage, analysis of over a billion credentials reveals that the most used password is '123456'. I will.
The most used password revealed by analyzing more than 1 billion credentials is '123456' --GIGAZINE

Researchers point out that the reason for this is that 'I can't remember passwords that are too complicated' and 'The number of passwords required is increasing.' Nowadays, many websites and services have to be logged in in our daily lives, and survey results show that each person has an average of 70 to 80 passwords. It is difficult to set and remember such passwords one by one.
To solve this problem, researchers have suggested using the ability to store passwords in browsers and using password managers. Password managers are useful for long and complex passwords because you can manage the passwords required by multiple websites with a single master password.
In recent years, instead of relying solely on a single password, there is a growing movement to adopt two-step authentication that combines elements other than passwords. By using two-step authentication, security can be improved because there are more cases where even if the password is leaked, it will not cause fatal damage.
What is the future of two-step authentication that replaces password authentication? --GIGAZINE
by Brian Ronald
Related Posts:
in Web Service, Security, Posted by log1h_ik