Is it really bad to increase security by 'hiding the system'?

'
Security by Obscurity is Underrated – Utku Sen --Blog – computer security, programming
https://utkusen.com/blog/security-by-obscurity-is-underrated.html
'Security by concealment', which attempts to increase security by hiding vulnerable systems from attackers, is a security measure that is ineffective in modern times because there is no way to prevent attacks once the system structure leaks to the outside. It has been with. It is believed that the reason why many open source software can guarantee security is that it does not rely on concealment security.
However, Şen points out that 'security by concealment' is not necessarily evil. According to the security community ' OWASP ', the risk of cyber attacks can be calculated by the formula ' risk = opportunity x impact '. Risk can be mitigated if either the 'impact', which is the magnitude of damage caused by an attack, or the 'opportunity', which indicates the possibility of being attacked, can be reduced. To reduce the chances of the two elements in the formula, the security mechanism must be built in layers so that if an attacker passes the first security, it will be caught in the other security.
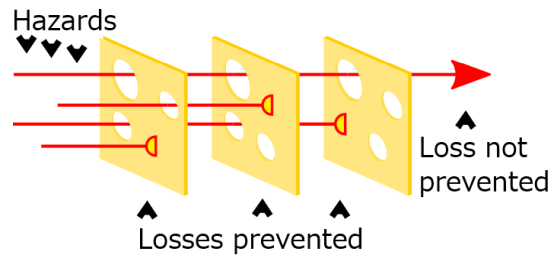
Şen argues that concealment security is useful as one of the layered security mechanisms. For example, if you are using 'root user with password of' 123456 'through default port 22' for SSH connection to the server, the server is very likely to be
In fact, when Mr. Şen conducted a questionnaire on Twitter, 'Do you scan all ports when you check whether the port of the attacked server is open by port scan?', About half of the respondents said 'Default port' It only scans ', and you can see that changing the port can reduce the chances of being attacked by about half.
I'm trying to prove a point for my new article. I need your answers for the question below. (Please be honest)
— Utku Şen (@utkusen) September 7, 2020
-When you do a port scan with nmap to find open ports on the target, are you specify a custom port range to scan all 65,535 ports? (With -p0-65535 parameter)
In addition to the SSH example, hiding the software structure by obfuscating the code or using random variables is effective against attacks. Şen also points out that concealment security is used not only in cybersecurity but also in the real world, as in the case of dozens of dummy cars being prepared for the president's move.

'Hiding security isn't enough on its own, but it acts as a layer of security that can reduce risk at no cost,' said Şen.
Related Posts:







