Damage of ransomware ``NetWalker'' which scraped a total of 2.7 billion yen in just 5 months expanded

The ransomware `` NetWalker '', which was first detected in August 2019, surged in March 2020, and the total damage was about 25 million dollars in just 5 months from March 2020 to August 2020 ( Approximately 2.7 billion yen), IT security company McAfee reported.
Take a 'NetWalk' on the Wild Side | McAfee Blogs
NetWalker ransomware gang has made $25 million since March 2020 | ZDNet
https://www.zdnet.com/article/netwalker-ransomware-gang-has-made-25-million-since-march-2020/
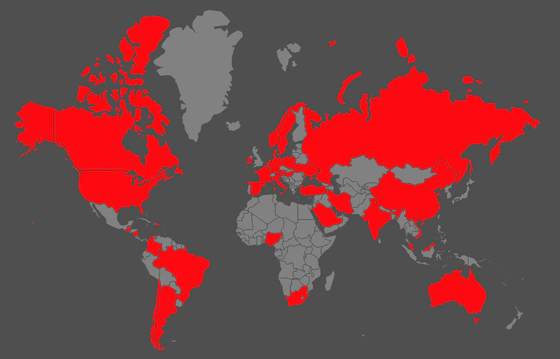
NetWalker is a ransomware that was first detected in August 2019. Although it was named 'Mailto' in the early versions, it is called 'NetWalker' after the end of 2019, and a variant appeared from the end of 2019 to the beginning of 2020. This variant has grown exponentially since March 2020, earning $25 million in just five months. Below is a list of the affected areas and you can see that NetWalker is prevalent in a wide area such as the Americas, Europe, Russia and Asia. The areas with the most damage are the United States and Western Europe.
The total amount of ransomware damage from October 2013 to March 2020 over 6 years, as calculated by the FBI, is as follows. The 1st place is 'Ryuk' which earned 61.26 million dollars (about 6.5 billion yen) in one year and eight months from February 2018 to October 2019. The second place was 'Crysis (Dharma)', which earned 24.48 million dollars (about 2.6 billion yen) over the three years from November 2016 to November 2019. Compared to these ransomware, NetWalker's '$25 million in 5 months' damage is pretty fast.
Per the FBI, Ryuk is, by far, today's most profitable ransomware gang in the last 6+ years
https://t.co/g3pJVxm0hj
RSA talk: https://t.co/Lo7vcz0MsM pic.twitter.com/OtMGBFAoUR — Catalin Cimpanu (@campuscodi) March 3, 2020
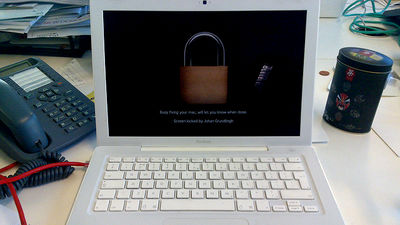
The initial version of NetWalker before March 2020 and the variants after March 2020 have changed the ransom demanding method. Before March 2020, the method was to send an email directly to the victim from a random email address to force the deposit. The following is an example of an email that NetWalker sent to a victim company before March 2020.
However, after March 2020, the variants changed to stop emailing and contact the victim through the
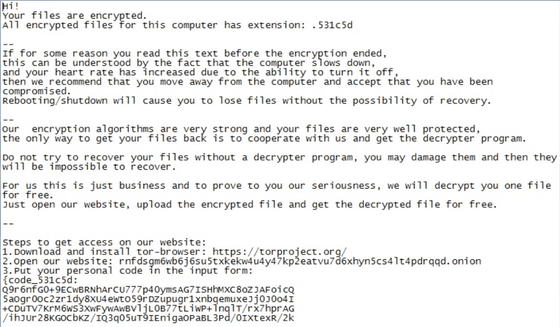
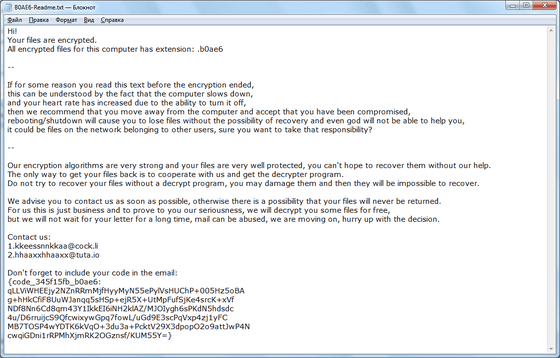
According to McAfee, the reason why the damage of NetWalker is increasing rapidly is due to the 'leak portal' that uploads the data stolen by hackers. If NetWalker breaks into your corporate network, NetWalker will first steal and encrypt sensitive data. After that, the hacker uploads the confidential data stolen by NetWalker to the leak portal using the 'timed disclosure function'. If the negotiation breaks down or you do not pay the specified amount within a certain time, it seems that the confidential file uploaded to the leak portal is disclosed. The leak portal looks like this.
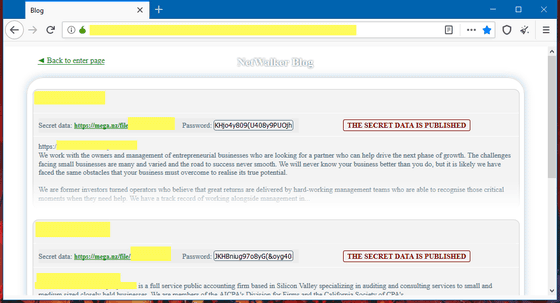
According to McAfee, the existence of this leak portal helps to raise the sense of crisis of victim companies that intellectual property and confidential data are leaked. In addition, the names of victims are often quoted in news stories, compromising 'branding power' of many companies, forcing many companies to pay ransom to NetWalker.
McAfee expects NetWalker damage to continue to increase after August 2020.
Related Posts:
in Security, Posted by darkhorse_log