Reported that there was a vulnerability in the online conference tool Zoom that an attacker could access a private meeting in just a few minutes

With the pandemic of the new coronavirus infection (COVID-19), online video conferencing tool Zoom has received a lot of attention, but it has also been pointed out that Zoom has
Zoom Security Exploit-Cracking private meeting passwords-Tom Anthony
https://www.tomanthony.co.uk/blog/zoom-security-exploit-crack-private-meeting-passwords/
Zoom bug allowed attackers to crack private meeting passwords
https://www.bleepingcomputer.com/news/security/zoom-bug-allowed-attackers-to-crack-private-meeting-passwords/
On March 31, 2020, British Prime Minister Boris Johnson reported on Twitter that he is holding a cabinet meeting using Zoom. Since the image attached to this tweet showed a unique meeting ID, it was pointed out that 'many people may try to join the cabinet meeting.' However, Zoom has password protection by default, and even if you know the meeting ID, it was difficult to join the cabinet meeting.
This morning I chaired the first ever digital Cabinet.
— Boris Johnson #StayAlert (@BorisJohnson) March 31, 2020
Our message to the public is: stay at home, protect the NHS, save lives. #StayHomeSaveLives pic.twitter.com/pgeRc3FHIp
It seems that Anthony was one of the people who tried to break the password of the private Zoom meeting somehow, so I conducted a survey on Zoom's Web client for a while. As a result, it was discovered that a malicious person could brute force a password that may have been set by default, vulnerable to a private meeting.
As of March 2020, when Anthony investigated how to break into Zoom's private meetings, the default password set at Zoom meetings was a 6-digit number, with a maximum of 100 possible passwords. It seems that it was limited to ten thousand. An attacker could try brute force passwords to break into a private meeting, so Anthony decided to check if the meeting login flow was okay.
If you know the target meeting ID, you can access the login form from the link 'https://zoom.us/wc/join/MeetingID'. At the time Anthony conducted the survey, the login form allowed him to join the meeting by entering the meeting password and name.
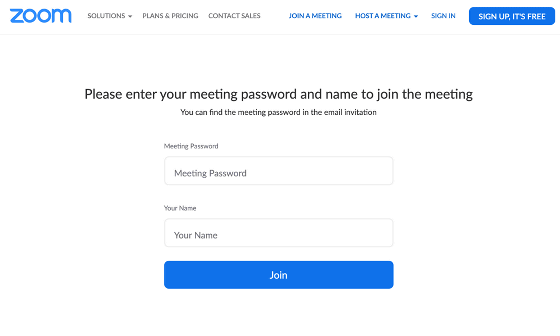
Behind this login flow, Zoom was taking steps to identify if the user attempting to log in agreed to the privacy policy. However, if you do not send the header for Cross Site Request Forgery (CSRF) countermeasures that are sent during the step, even users who do not agree to the privacy policy can log in.
Even more problematic was that there was no limit on the number of password attempts in the login flow. If a malicious person breaks the CSRF measures, you can use multiple machines in parallel to brute force candidate 1 million passwords and access private Zoom meetings in just a few minutes. Said Anthony.
Anthony reported to Zoom about this issue on April 1st, and Zoom's web client was suspended on April 2nd to fix the issue. At this time, 'when you access the Web client of Zoom, 403 Forbidden error will come out' a lot of Internet users and reporting has been, contrary Zoom is 'We are in maintenance mode the Web client,' said the statement Was issued.
During this fix period, Zoom will require users to log in when joining a meeting from a web client, and will make default passwords longer, including non-numeric characters. In addition, it seems that there is a limit on the number of password attempts, and after April 9, 2020, unauthorized login using this vulnerability is no longer possible.

Related Posts:
in Web Service, Security, Posted by log1h_ik