The world's largest drone maker DJI's app turned out to be able to collect user data and force installation of arbitrary apps

The Android version of the
DJI Android GO 4 application security analysis | Synacktiv
https://www.synacktiv.com/en/publications/dji-android-go-4-application-security-analysis.html
DJI Privacy Analysis Validation
https://blog.grimm-co.com/2020/07/dji-privacy-analysis-validation.html
Chinese-made drone app in Google Play spooks security researchers | Ars Technica
https://arstechnica.com/information-technology/2020/07/chinese-made-drone-app-in-google-play-spooks-security-researchers/
'DJI GO 4' is an application for operating DJI drones such as Mavic series , Spark and Phantom 4 , and managing the images shot by the drones. On July 12, 2020, security company Synacktiv reverse engineered 'DJI GO 4' and discovered that the Android version of 'DJI GO 4' was as obfuscated as malware. A suspicious analysis team investigated the source code and revealed that the Android version ``DJI GO 4'' had a function to collect user's personal information and a function to install and execute arbitrary code became.
According to Synacktiv, the latest version before 4.3.36 had a built-in 'Mob SDK' that collects user's personal information and sends it to Chinese analysis company MobTech . Mob SDK includes smartphone screen size and brightness, WLAN address, MAC address, BSS-ID , Bluetooth address, carrier name, IMEI , IMSI , SIM card terminal serial number, SD card information, OS language and kernel version, etc. A wide range of information is available, said Synacktiv. In addition, the crash report module 'Bugly' that was installed between versions 4.122 and 4.3.25 also collected IMEI, IMSI, terminal serial number of SIM card, Wi-Fi interface MAC address, SSAID, etc. explained.
In addition, the Android version 'DJI GO 4' has a specification that automatically restarts when you try to exit the application with a swipe. This specification allows the user to collect personal information in the background, even though they know the application has been closed. Information such as IMEI, IMSI, and terminal serial number of SIM card is not related to drone operation/video management, and it is outside the scope of DJI's privacy policy to collect this information, whether it is an intelligence agency or a malicious person. Synacktiv argued that this would lead to the act of personally identifying and eavesdropping on communications.
In addition, 'DJI GO 4' is equipped with an automatic update function via the 'Weibo SDK' developed by Chinese social media company Weibo, which allows you to download applications that have not been certified by Google. Explained Synacktiv. The update displayed in 'DJI GO 4' looks like the following, and DJI can rewrite the detailed description field arbitrarily, so it is possible to induce you to install another application pretending to be the update Synacktiv Says.
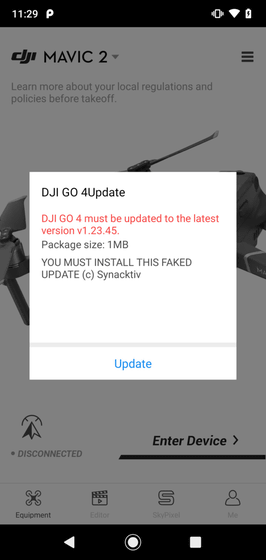
User permission is required to install the downloaded files.

Since 'DJI GO 4' requires authority to change contacts, microphones, cameras, location information, storage, network connections, etc., 'There is no evidence that this specification has been abused, but abuse is possible. 'Synacktiv argues. Security firm GRIMM validated Synacktiv's report and reported, 'We were able to validate Synacktiv's report.' I fully agreed with Synacktiv's report.
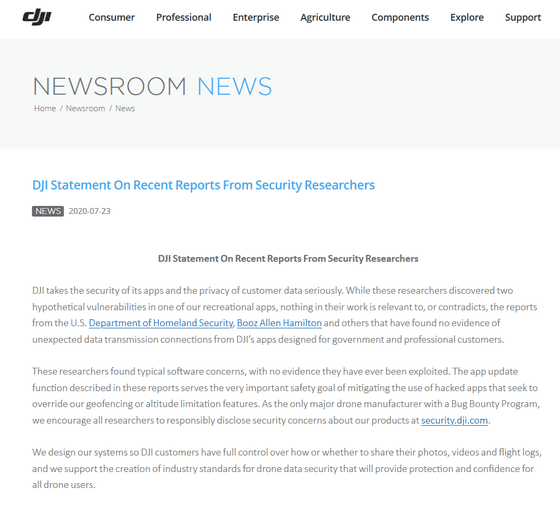
In response to a series of remarks, DJI said, 'We focus on app security and customer data privacy. We found some typical software concerns that have been exploited so far. No evidence exists. The MobTech and Bugly components mentioned in this report were removed in the past when a security flaw was identified, but there are no reports of exploitation.' 'Bug bounty As the only major drone manufacturer with programs, we encourage all researchers to responsibly disclose security concerns about our products at security.dji.com .'
DJI Statement On Recent Reports From Security Researchers
https://www.dji.com/newsroom/news/dji-statement-on-recent-reports-from-security-researchers
According to a survey by Synacktiv, obfuscation of applications and automatic update functions exist only in the Android version of 'DJI GO 4', not in the iOS version. Synacktiv called for not to use the application for confidential purposes, saying that Android version ``DJI GO 4'' has been downloaded more than 1 million times and that law enforcement agencies may also use DJI drones ..
According to Ars Technica, an IT news site that reported this case, Google is scrutinizing the report of Synacktiv.
Related Posts: