How did a hacker steal credit card information using 'Google Analytics'?

Security company Kaspersky announced that a number of e-commerce sites may have stolen personal information, including credit card information, through hacking via
Web skimming with Google Analytics | Securelist
https://securelist.com/web-skimming-with-google-analytics/97414/
Google web tool used to steal credit cards online --how to protect yourself | Tom's Guide
https://www.tomsguide.com/news/credit-card-theft-google-analytics
Crooks abuse Google Analytics to conceal theft of payment card data | Ars Technica
https://arstechnica.com/information-technology/2020/06/google-analytics-trick-allows-crooks-to-hide-card-skimming/
Google Analytics is a free access analysis service provided by Google, and is mainly used by site owners to track the number and attributes of site visitors using their tracking ID. According to Kaspersky, attacks using Google Analytics fake domains such as 'google-ana t ytics.com', 'google-ana i yt l cs.com' and 'google-analytics. cm ' have been repeated. However, this time it was confirmed that an attack via genuine Google Analytics was confirmed.
Below is an example of code embedded in an e-commerce site for an attack. The Google Analytics domain name underlined and the description of the tracking ID 'UA-XXXX-Y' are correct, so at first glance it seems that there is no problem, but in reality this tracking ID is ' It is linked to 'Google Analytics account'.
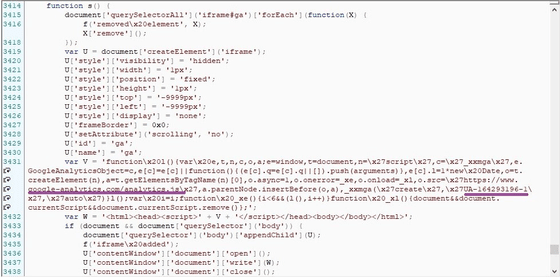
In addition, the malicious code embedded in the site by the attacker uses anti-debugging technology that 'does not collect data when the browser of the browser is in the developer mode'. People find it difficult to find problems, Kaspersky points out.
Kaspersky said in a report, ``The only thing an attacker has to do is create a Google Analytics account, receive a tracking ID, and insert the malicious code along with the tracking ID into the source code of the web page. After that, the attacked e-commerce site will collect data such as credit card information entered by the visitor and send it to your account.'
E-commerce sites targeted by this trick have been found in more than 20 countries all over the world, and most were from Europe and the Americas.

'Google Analytics is a very popular service and is unconditionally trusted,' Kaspersky said of the danger of this trick. We encourage owners of sites that use Google Analytics to take the following precautions:
· Keep all software up to date and never install web applications or CMS components from untrusted sources.
· Set strong passwords for all managed accounts.
-Set user privileges to the minimum required.
· Filtering user-entered data and query parameters to prevent third-party code intrusion.
-Especially for e-commerce sites, introduce a payment system that complies with PCI DSS , which is a security standard for protecting credit card transactions.
In addition, IT news site Ars Technica said, 'Most of the time, it is impossible for end users to detect theft of credit card information. However, most antivirus software can detect this type of attack. Most e-commerce sites also allow you to shop safely in developer mode, so it's a good idea to do so, though the best defense is to keep your credit card bills on a regular basis. And it will be a careful check.'

``Google Analytics is one of the most popular access analytics services in the world,'' says Victoria Vlasova, senior malware analyst at Kaspersky Lab. Therefore, malicious code containing a Google Analytics account is unobtrusive and is often overlooked. Site admins say that code from a third-party source is correct. Don't assume that it's okay if you have the source inside.'
Related Posts:
in Web Service, Security, Posted by log1l_ks