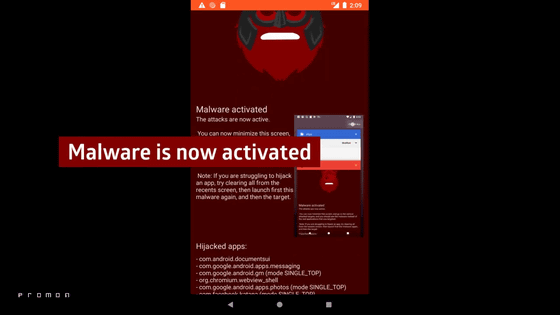
Android vulnerability `` Strand Hogg 2.0 '' that malicious applications can take over almost all applications

A vulnerability in Android discovered in 2019 that allows malicious applications to take pictures, read and send SMS, record phone calls, extract login information, etc. Similar to ` ` StrandHogg '', higher risk The vulnerability ' StrandHogg 2.0 ' was discovered by researchers at Norwegian security company
StrandHogg 2.0-The 'evil twin'
http://promon.co/strandhogg-2-0/
A movie showing the concept of what can be done with 'Strand Hogg 2.0' has been released by Promon.
StrandHogg 2.0-The 'evil twin'-Proof of Concept video-YouTube
Promon has prepared an app that uses StrandHogg 2.0 to attack, and five apps that are targeted.

The attacking app has no privileges.
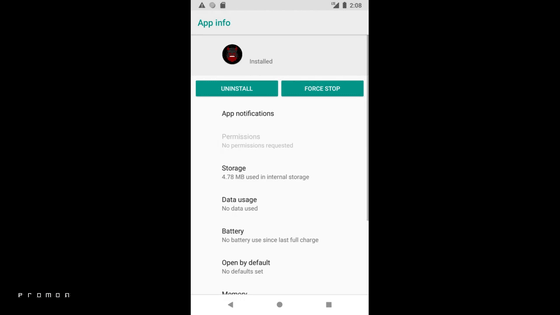
On the other hand, the five apps have been downloaded from Google Play and left untouched. The attacking application has not requested any permissions and has not granted permission.

Attacking apps can take over almost any app at the same time.
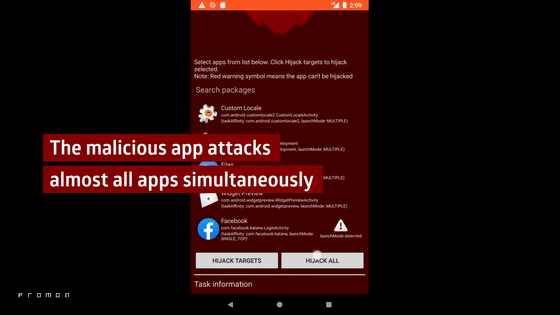
If this happens, even if you start the Facebook application ...

You will be taken over.
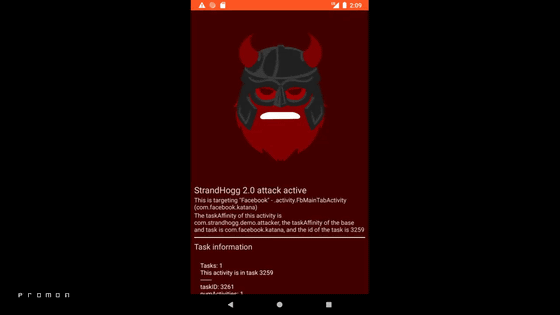
StrandHogg 2.0 has similar characteristics to the vulnerability found in 2019, StrandHogg, but StrandHogg can only attack one app at a time, while Attack
Although similar, the measures for 'Strand Hogg' are hardly applicable to 'Strand Hogg 2.0'.
It does not affect Android 10. In addition, Promon notified Google of the vulnerability as of December 2019, and Google assigned the vulnerability 'CVE-2020-0096' as the maximum severity 'urgent'. A patch has been released for Android 8.0 / 8.1 / 9 in May 2020.
Related Posts:
in Security, Posted by logc_nt