`` Vulnerability that account can be taken over just by looking at GIF image '' is found in Microsoft Teams of group chat tool

Due to the epidemic of the new coronavirus infection (COVID-19), many companies have introduced telecommuting, and demand for video conferencing and group chat tools such as
Beware of the GIF: Account Takeover Vulnerability in Microsoft Teams | CyberArk
https://www.cyberark.com/threat-research-blog/beware-of-the-gif-account-takeover-vulnerability-in-microsoft-teams/
Microsoft Teams Vulnerability Exposed Organizations to Attacks | SecurityWeek.Com
Microsoft Teams is an enterprise communication and collaboration platform that includes chat, video conferencing, file storage and app integration features. In the COVID-19 pandemic, tools that facilitate team collaboration while working from home have become very useful for companies.
So researchers at CyberArk said they've dug deeper into the security of Microsoft Teams, which many companies and organizations are implementing. Each time a user opens Microsoft Teams, a new access token is generated and the client uses one of the generated access tokens to allow the user to see the image. Researchers have found a very interesting issue in the way Microsoft Teams passes access tokens to image resources.
Researcher said that 'a malicious attacker sends a GIF image created by a special method to any other party in Microsoft Teams, and if the other party opens the GIF image, the access token will be sent to the attacker' Vulnerability I have found sex. The attacker who obtained the access token can take over the victim's account through the API interface of Microsoft Teams, read messages exchanged with Microsoft Teams, send messages to other users, create groups, group You can add or remove users to or change the permissions of groups. It seems that the same attack can be done not only by GIF images but also by clicking on the sent link.
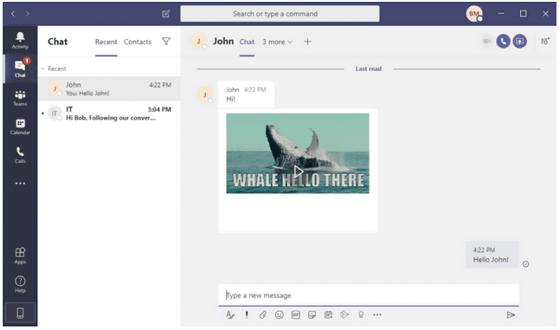
The array of attacks can be automated, using the first compromised account to spread malicious GIF images to all group members, potentially revealing an attacker that can hijack the entire organization. With this, it is also possible to obtain highly confidential information such as highly confidential data, important passwords, meeting and calendar data, business plans.
Researchers at CyberArk said, 'More complicatedly, this vulnerability could be used to send' false information 'to other employees. Account takeover can result in financial damage, confusion, and direct data loss. '
In an interview with SecurityWeek, a security website, CyberArk researchers describe multiple attack scenarios that exploit vulnerabilities in Microsoft Teams. Possible scenarios are: Require your organization's IT team to reset passwords on certain systems and hijack systems other than Microsoft Teams. ”Take over your organization's executive accounts and contact the CEO to secure confidential financial information. There is a possibility that damage is not limited to information on Microsoft Teams, such as `` obtaining information '' `` obtaining a meeting schedule between executives and tricking you to use it at the next meeting to install software loaded with malware '' There is.

As a prerequisite for the vulnerability discovered this time, it seems that the access token is sent to a specific subdomain, so the attacker must somehow hijack the subdomain in advance. Also, the access token acquired by the attacker is valid for 1 hour, and it is necessary to browse a new GIF image in order to continue taking over the account.
Already, Microsoft's security team has worked with researchers at CyberArk to prevent specific subdomains from being sent with access tokens from being misused. A Microsoft spokesperson told SecurityWeek: 'We worked on this issue and worked with CyberArk researchers on the principle of

by Mike Mozart
Related Posts:
in Software, Web Service, Security, Posted by log1h_ik