Ransomware developer threatens to create `` blog that publishes data of companies who did not pay ransom ''

by
In recent years, ransomware that infects computers, restricts access to systems, and uses data as a shield to demand a ransom has been rampant worldwide. A new ransomware discovered in August 2019 ` ` Nemty '' is apparently threatening to ` ` publish data stolen from victim's computer on blog unless paying ransom '' became.
Nemty Ransomware to Start Leaking Non-Paying Victim's Data
https://www.bleepingcomputer.com/news/security/nemty-ransomware-to-start-leaking-non-paying-victims-data/
Nemty ransomware makers may be latest to adopt data leak strategy
https://www.scmagazine.com/home/security-news/ransomware/nemty-ransomware-makers-may-be-latest-to-adopt-data-leak-strategy/
Initially, ransomware was rampant around Russia, but damage has spread worldwide. In the United States, ransomware targeted at dental clinics encrypted more than 400 medical institutions at once, and Lake City , Florida was forced to pay a ransom of 54 million yen .
A local government in the United States that paid a ransom of 54 million yen for ransomware damage fired one IT manager in the city-gigazine

by TheDigitalArtist
According to computer help site BleepingComputer , ransomware , which initially appeared as 'restricted access to infected PC systems', has changed slightly in recent years. For example, ransomware such as Maze and Sodinokibi steal files from computers before encrypting them and demanding a ransom in exchange for 'data leakage.'
This tactic is primarily geared towards businesses, which seem to make it easier for companies to pay ransoms by risk and ransoms, such as the dangers of being breached by data breaches, fines, brand image degradation, and contract abandonment.

by
Nemty, which spreads mainly in China and South Korea, also uses a technique similar to new ransomware such as Maze and Sodinokibi, and demands a ransom for shielding against data leaks. To facilitate contact with victims, Nemty developers display an 'affiliate panel' for victims, through which they can send news feeds about their plans and ransomware bug fixes. It seems to be sending. The following image is an image of Nemty's affiliate panel obtained by BleepingComputer. If you look closely, you can see that there is a plan to create a blog that leaks data if you do not pay the ransom.
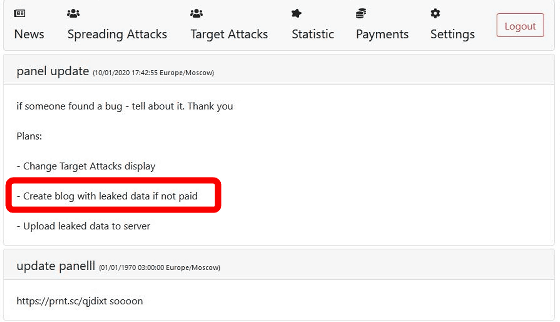
IT media SC Magazine points out that Nemty threatens to publish files from victims, thereby increasing ransom pressure on companies seeking to protect customer data.
Nemty's attack targets the entire corporate network and encrypts all devices in the network at once. BleepingComputer argued that ransomware attacks that suggest the disclosure of data should be considered 'data breaches', as this type of attack could lead to the disclosure of user personal information and trade secrets.
Related Posts:
in Software, Web Service, Security, Posted by log1h_ik







