Vulnerability `` StrandHogg '' that malware takes over smartphone on Android is discovered, theft damage is already from some bank accounts

An Android vulnerability “ StrandHogg ” was discovered by security researchers. By exploiting this vulnerability, malicious apps can take photos, read and send SMS messages, record phone calls, extract bank account information and login credentials, and more.
StrandHogg: Serious Android vulnerability leaves most apps vulnerable to attacks.
Vulnerability in fully patched Android phones under active attack by bank thieves | Ars Technica
https://arstechnica.com/information-technology/2019/12/vulnerability-in-fully-patched-android-phones-under-active-attack-by-bank-thieves/
According to the research team of security company Promon , the vulnerabilities in question exist in a control setting called ' TaskAffinity ' to enable multitasking on Android. Malicious apps exploit this specification and set the TaskAffinity of one or more activities to match the package name of a trusted third-party app.
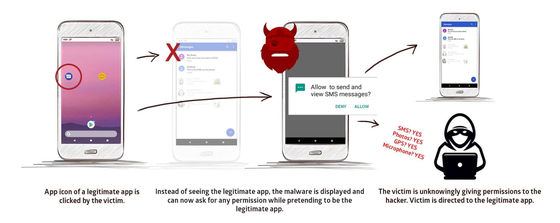
Then,
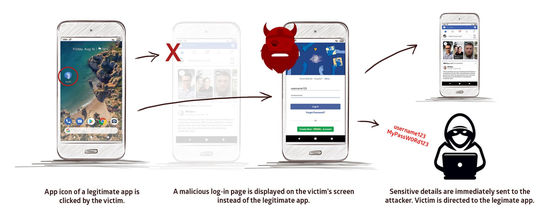
According to Promon's research team, Strandhogg was able to identify the fact that a security company in Eastern Europe reported that `` There are cases where money is withdrawn from customer accounts at multiple banks in the Czech Republic '' It was a chance. In addition, the research team says that it named StrandHogg from the Viking tactics because the app exploited the vulnerability and took over the smartphone to take money.
The team researched malware that exploited StrandHogg and announced that over 500 popular apps were all at risk and all versions of Android were affected. Also, 36 apps that actually exploited the vulnerability were identified. However, it seems that none of the apps found are handled on Google Play.
As a sign that the app is trying to exploit the vulnerability, the research team has raised the following alerts:
-An application or service that is already logged in requests login.
-A pop-up requesting permission for something without including the app name is displayed.
・ You will be asked for permission that you don't need.
・ Typographical errors are seen in the user interface of the app.
• Nothing happens when you tap a button or link on the app's user interface.
-The Android 'Back' button does not work as expected.
Related Posts:
in Software, Smartphone, Security, Posted by log1i_yk