A method to hack Google and Amazon smart speakers with laser irradiation turned out, it can be executed even if it is more than 100 meters away

A method of hacking voice assistants such as Amazon Alexa, Google Assistant, Apple Siri, etc. installed in smart speakers and smartphones with 'Laser Light' was announced.
Light Commands | Laser-Based Audio Injection on Voice-Controllable Systems
Researchers hack Siri, Alexa, and Google Home by shining lasers at them | Ars Technica
https://arstechnica.com/information-technology/2019/11/researchers-hack-siri-alexa-and-google-home-by-shining-lasers-at-them/
Researchers from the University of Electro-Communications in Japan and the University of Michigan have discovered a new voice assistant hacking method called “ Light Commands ”. In Light Commands, it is possible to irradiate the microphone part of the device equipped with voice assistant with a low-power laser and execute various commands as well as voice instructions.
According to the research team, it is possible to unlock the door using Light Commands and to access the website, and if the laser can accurately irradiate the microphone part, it is a place more than tens of meters away It can be hacked from. It is also possible to run through the window glass.
You can see what hacking method Light Commands is by watching the following movie.
Light Commands Overview-YouTube
Light Commands is a hacking method that exploits the vulnerabilities of MEMS microphones that are widely used in devices equipped with voice assistants. MEMS is an acronym for Micro Elerctronics Mechanical System, which uses semiconductor micromachining technology, etc., instead of conventional machining technology, to place minute mechanical parts and electronic circuits on a substrate. By integrating, it is possible to manufacture ultra-small and highly functional devices. MEMS microphones are also used in devices equipped with Amazon Alexa, Google Assistant, and Siri.
The voice assistant performs various actions in response to the user's voice. Notify the weather forecast ...
Voice assistants make people's lives more convenient, such as unlocking doors.
On the other hand, the safety of voice assistants has always been a concern. However, voice assistants are basically placed in the house, and unless an intruder from outside can enter the house, the security risk is not so high.

The work of a microphone on a voice assistant-equipped device is to convert sound waves into electrical signals.
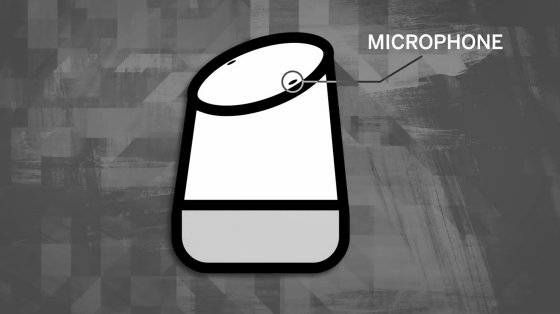
There is a small diaphragm inside the microphone, and an electric signal is transmitted when sound waves shake the diaphragm.

A malicious person may try to operate the voice assistant loudly from outside the house, but it is usually impossible to do so because it is blocked by window glass.

However, Light Commands is a hacking method that operates voice assistants using a physical loophole that “the laser beam can be used to shake the diaphragm of a MEMS microphone”.
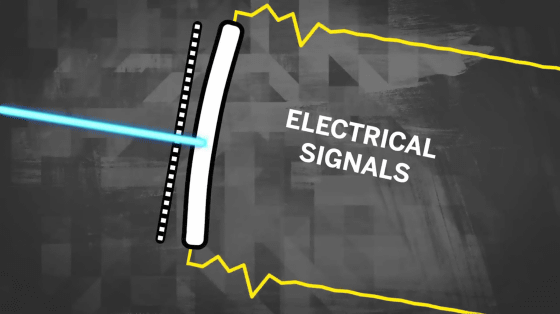
Therefore, you can operate the voice assistant from outside the house as long as the light is delivered.

Also, Light Commands can be executed with relatively inexpensive equipment, and sometimes attacks can be launched from another remote building.

The fundamental solution to prevent Light Commands requires a redesign of the microphone, which seems to require a large cost.

The research team is working with vendors such as Amazon, Google, Apple etc. to find ways to prevent Light Commands.

The research team has actually released a movie to set up Light Commands for the voice assistant.
The research team executes Light Commands with three laser pointers of $ 18 (about 2000 yen), a laser driver of $ 339 (about 37,000 yen), an audio amplifier of $ 27.99 (about 3000 yen) Developed equipment. The command transmitted through the laser can be finely adjusted by modulating the amplitude of the laser beam.

Sending the command 'OK Google, open the garage door' to the microphone part of Google Home by sending a laser ...

“OK, I ’m open,” Google Assistant replied.

The garage door has been opened despite the fact that no verbal instructions were sent.

The research team is also investigating how far away Light Commands can be run.
The research team installed a new telecommand lens of $ 199.95 (approx. 22,000 yen) on its own Light Commands execution device and improved it so that it can irradiate a laser at a single point even at long distances.

This time, the command 'OK Google, what time is it now?'

The target Google Home is located 110 meters away ...

It is fixed with the microphone part facing the laser side. After a short laser irradiation, the Light Commands command was recognized, and the Google Assistant replied, “It is 9:43.”

In addition, a movie that hacks with Light Commands through a window from a building several tens of meters away is also open to the public.
This time, a laser is emitted through the window from a building that looks like a tower on the right side of the screen. The position of the laser irradiation device is 43 meters high, the location where Google Home is installed is 15 meters high, the irradiation angle is 21.8 degrees, and the distance between buildings is 70 meters.
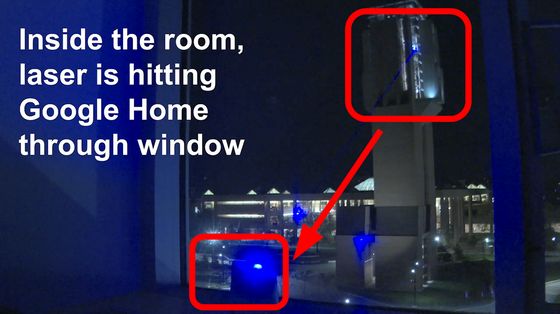
Laser irradiation using a telephoto lens.

Then Google Home reacts ...

The garage door has been opened.

The research team commented on the MEMS microphone, 'It reacts to light as if it were sound.' Regarding the reason why the diaphragm is shaken by light, the physical background is not fully understood at the time of writing the article.
The laser pointers used in the experiment ranged from those with only 5 mW laser output to those driven with 60 mW, but many voice assistants such as Google Assistant, Amazon Alexa, Apple's Siri responded to the light. It was. At the time of writing, it seems that Light Commands has never actually been used by malicious people, but Light Commands is an attack that can be performed in the real world, and device manufacturers have built new defenses The research team points out that it is necessary.
Related Posts:







