Apple's face authentication Face ID can be broken simply by sticking tape on glasses, researchers point out `` Achilles tendon for biometric authentication ''

by
When Apple's face authentication “ Face ID ” was released, it was reported that there were cases where it could break through if it was a brother or twin other than the person himself. The latest research results on such a face recognition system were announced, and the vulnerability of the authentication process that exists in biometric authentication was announced. If this is abused, it seems that it will be possible to break through face authentication like Face ID.
Researchers Bypass Apple FaceID Using Biometrics 'Achilles Heel' | Threatpost
https://threatpost.com/researchers-bypass-apple-faceid-using-biometrics-achilles-heel/147109/
Tencent researchers announced that during the event to share the latest security related information Black Hat USA 2019 , it is possible to access the terminal through Face ID just by wearing glasses modified on the face It was. Normally, Face ID cannot be unlocked unless you are looking at the screen, and even if you turn off the screen gaze recognition function , you cannot unlock it.
However, according to the method announced by researchers, it is possible to break through Face ID by putting black and white tape on the lens part of the glasses and putting it on the owner of the iPhone who wants to access it.
Remodeled glasses `` X-Glasses '' developed by researchers to break through Face ID
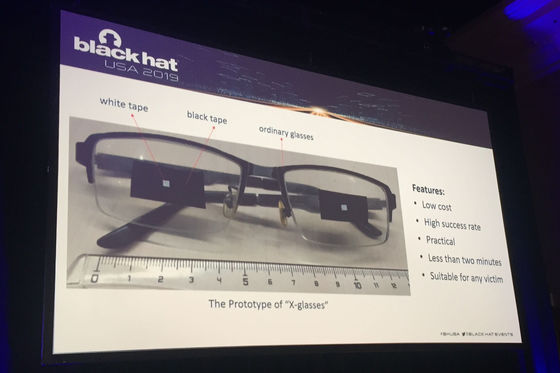
According to researchers, this attack uses one of the functions used in biometric authentication called “liveness detection”. “Activity detection” is a part of the biometric authentication process to distinguish between real and fake humans, and it works by detecting background noise, distorted responses, and out of focus.
A researcher who announced an attack method that can break through Face ID said, `` The biometric data captured by the camera (at the time of authentication) is set (in advance) by leaking biometric authentication data and strengthening fraud ability using artificial intelligence (AI) 'Activity detection' to measure whether or not a person has become an Achilles tendon in the security aspect of biometric authentication, 'he said.
Traditionally, the focus has been on generating fake data to avoid biometrics such as fingerprint and face authentication. For example , forgery of fingerprints to break through fingerprint authentication and forgery of masks to break through face authentication apply to the generation of fake data. However, researchers focused on developing a method to unknowingly break through authentication using the victim's face, and then focused on activity detection.

“There is a challenge with this method,” said Zhuo Ma of Tenhu Security, one of the researchers who devised a way to break through face recognition. However, it is necessary to avoid awakening sleeping targets. “In general, it was very difficult to counterfeit 3D systems, so we needed a more successful and less costly way,” explains the shortcomings and advantages of X-Glasses.
The research focused on how activity detection scans the user's eyes. Focusing on the fact that activity detection abstracts eyes, the research team discovered that human eyes (black tape) and irises (white tape) can be expressed with black tape and white tape. Therefore, by sticking the tape to the glasses, we have found that activity detection mistakes the tape as eyes. According to researchers, Face ID doesn't extract 3D information in the eye area for users wearing glasses, explaining that it is a mechanism that misidentifies tape as eyes.
By using X-Glasses, it is possible to break through Face ID of a sleeping user, so if you use a mobile payment application etc., you will be able to send money illegally.
Although the methods presented by the researchers clearly have major drawbacks, it is clear that they have highlighted the security risks of biometric authentication. Researchers are proposing to manufacturers that provide biometric authentication functions to detect video and audio synthetically.
Related Posts:






