It is discovered that 134 million data including personal information of Honda employees have been leaked in the cloud

by
Justin, who works at Cloudflare , discovered that the Elasticsearch database used internally by Honda Motor (Honda) is hosted without special certification.
Honda leaks database with employee computer data
https://rainbowtabl.es/2019/07/31/honda-motor-company-leak/
What Justin discovered is a database that Honda uses in its internal network. The data held in the database is 'Similar to Honda's internal equipment inventory,' Justin writes. The database contained information such as machine host name, MAC address, IP address, OS version, applied patches, and status of endpoint security software. Since Justin discovered the problem and contacted Honda, and the security team has already solved the problem, the database can not be accessed at the time of writing.
However, as of July 1, 2019, anyone could access the database. At first, there was no way to contact Honda, but when Justin asked for help on Twitter, he could get some help from some kind people, and on July 6, Honda's security team Succeeded in contacting you.
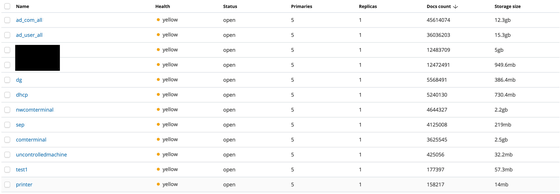
The database stores about 134 million items of data, and the amount of data is as large as 40 GB.
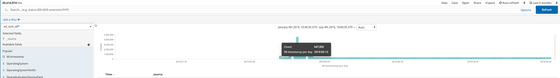
It is reported that the database contains data from March 13, 2019 to July 1.
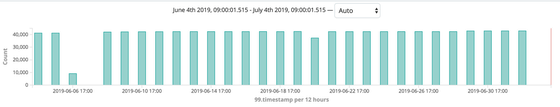
According to the date order of stored data, it is found that about 40,000 data are added to the database every day. Also, in mid-March 2019, the amount of data has been abnormally increased. The Elasticsearch database began to operate in March 2019 in that the data was only available from March 13, 2019, and the amount of data jumped up due to the initial data load, Justin Is guessing.
The database stores data on employees working in multiple locations including Japan, and it is said that data on employees in Japan is displayed as 'Empty string.' It corresponds to about 28.6% on the database.
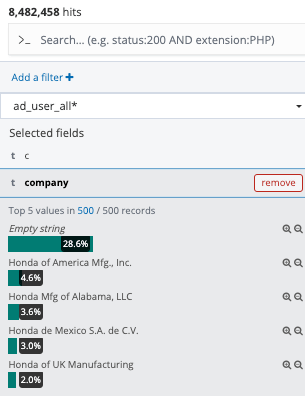
Justin released some of the data stored in the database with black-filled screen shots.
The data stored in the 'ad_com_all' index included employee name, host name, OS type, and OS version. About 300,000 data are updated per cycle on this index.
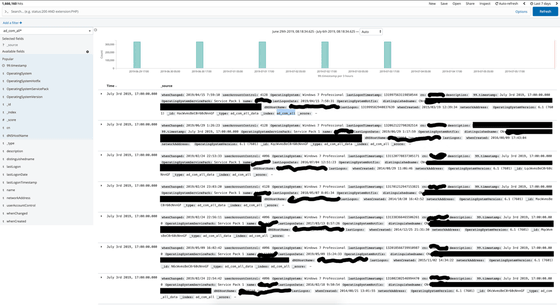
The index 'ad_user_all' includes employee email address, employee name, last login, employee number, account name, and mobile field. This index is also updated about 300,000 data per cycle.
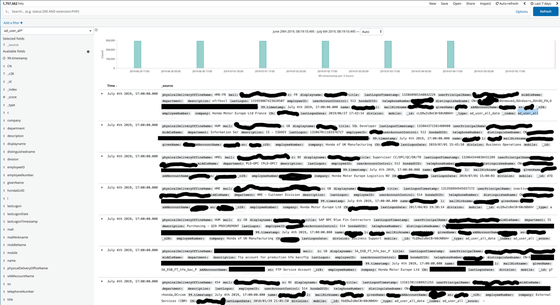
The index 'comterminal' relates to employee email, department, machine IP address, MAC address, host name, OS, machine type, endpoint security status, applied Windows product updates (KB) It seems that the information was included. About 40,000 data will be added in one update.
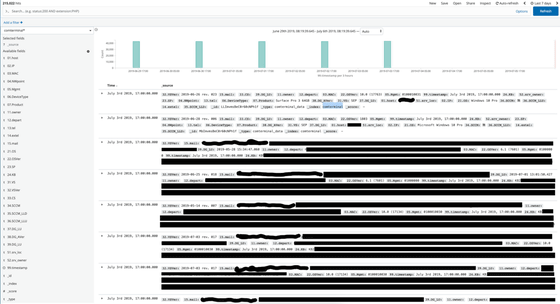
The index 'nwcomteminal_data' contains the machine's IP address, MAC address, host name and KB information.
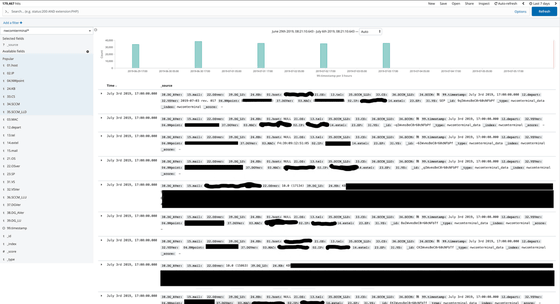
The index 'dhcp_data' contains the device's management tag and MAC address. It contains a user name that can be presumed to be the administrative staff.
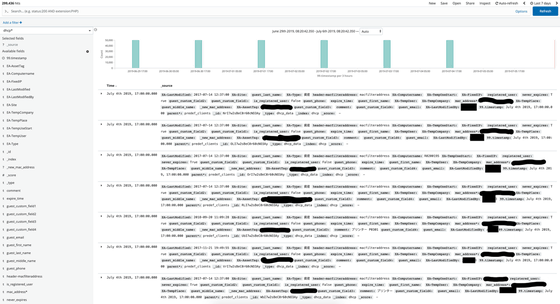
The index 'printer_data' contains the printer name and the internal IP address. Each update adds about 2500 data.
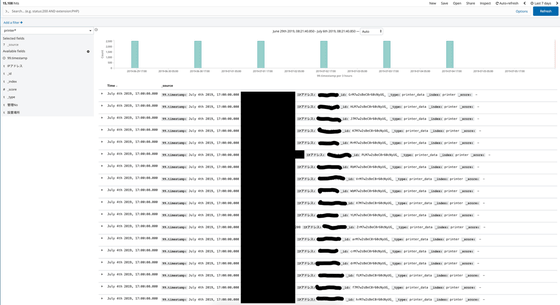
The information in the endpoint security table is mostly blacked out, for 'it's clear who the endpoint security vendor is,' Justin said. The table contains the employee's username and the endpoint security status of the terminal used by the employee. In addition, about 90,000 data will be added for each update.
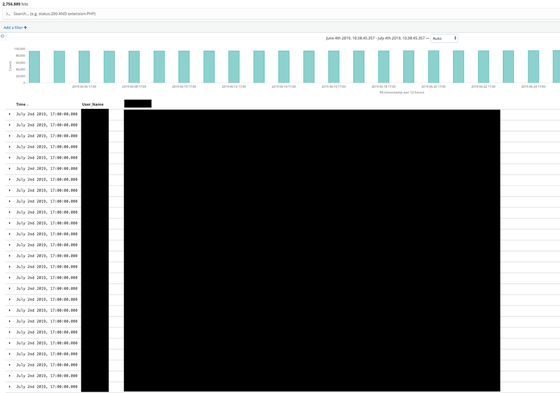
The index 'uncontrolledmachine' contains information that allows you to reasonably guess the host name and OS information of a machine not monitored by endpoint security software. Some usernames are included, and about 3000 data will be added in one update.
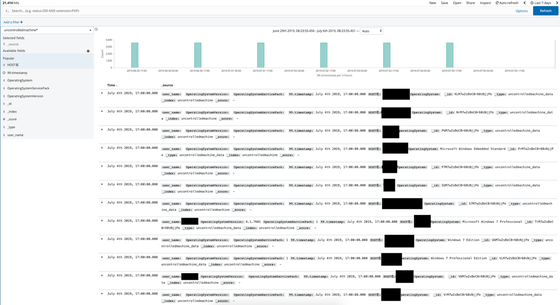
In addition, the database contains information about PCs used by Honda CEOs. You can browse here: Mail, Full Name, Department, MAC Address, Applied KB, OS, OS Version, Endpoint Security Status, IP Address, Terminal Type. Here you can check the CEO's name, last login date, employee ID, email, department, account name.
Honda says to Justin, “Thank you for pointing out the vulnerability. The security issue identified is a cloud-based external third party consisting of information related to our employees and computers. I was able to access a part of the data of the site. When I checked the access log of the system, the download of the data by the third party was not seen. There is no evidence that data has been leaked, and we will take appropriate action in accordance with relevant laws and regulations, and will continue to work on preventive security measures to prevent similar incidents in the future. '
Related Posts: