It turns out that just turning on the iPhone's Bluetooth leaks phone numbers to nearby people

by
Dmitry Chastuhin, a member of security service company Hexway, announced in his blog post that a bug has been found that 'phone numbers may leak to people nearby if Bluetooth is turned on with an iPhone.'
GitHub-hexway / apple_bleee: Apple BLE research
https://github.com/hexway/apple_bleee
Everyone knows What Happens on Your iPhone – hexway
https://hexway.io/blog/apple-bleee/
iPhone Bluetooth traffic leaks phone numbers-in certain scenarios | ZDNet
https://www.zdnet.com/article/iphone-bluetooth-traffic-leaks-phone-numbers-in-certain-scenarios/
The defect found this time is caused by a network interface called Apple Wireless Direct Link (AWDL) for mutual communication between Apple products. When Bluetooth is turned on on the iPhone, AWDL sends various information to the surroundings via Bluetooth Low Energy (BLE), which is a Bluetooth communication standard.

by
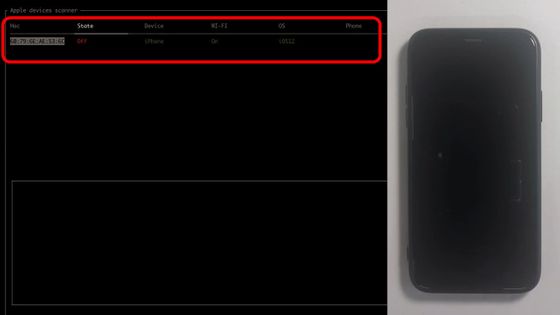
Such information includes smartphone status information, Wi-Fi status, OS version, etc., as well as hashed phone numbers.
According to Chastuhin, 'only the first 3 bytes of the hashed phone number will be sent, but that's enough to recover the phone number.' Because phone numbers are in a fairly rigid format, hacking phone numbers requires restoring data using a pre-built hash table , but Chastuhin creates and publishes a tool to automate that process. doing.
The following movie shows how Chastuhin actually uses his tool to extract information from the iPhone.
Apple devices sniffer-YouTube
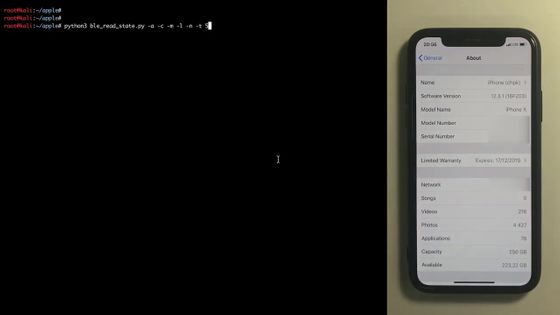
The left side of the screen shows the tool screen, and the right side shows the actual operation of iPhone X with iOS 12 installed.
With Bluetooth turned on ...
Press the power button to turn off the screen.
Then, the status of the iPhone was displayed on the screen of the tool displayed on the left.
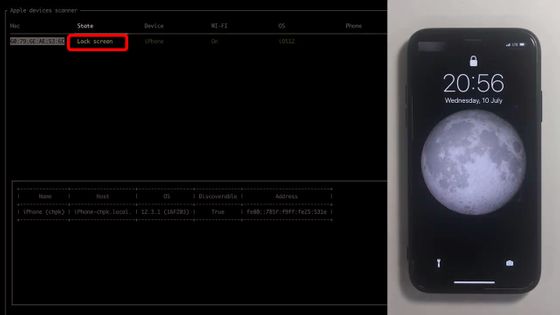
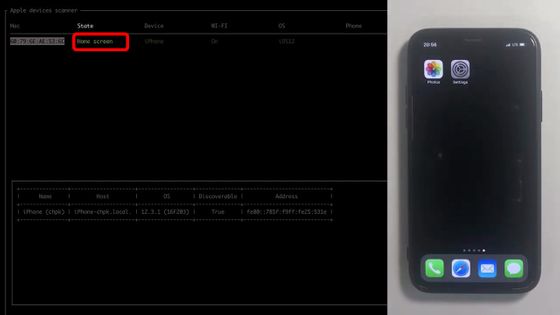
With the screen on, the status is now 'Lock Screen'.
The status changes to 'Home Screen' when you move to the home screen after unlocking.
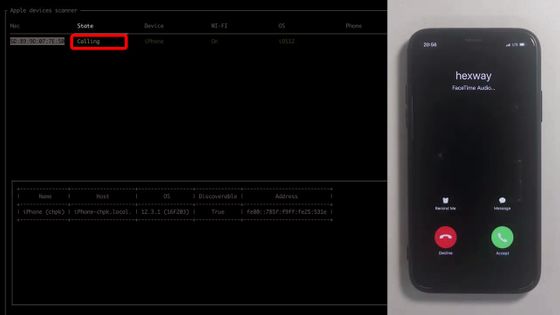
It was 'Calling' if you were on a call. You can see in real time what you are using the iPhone.
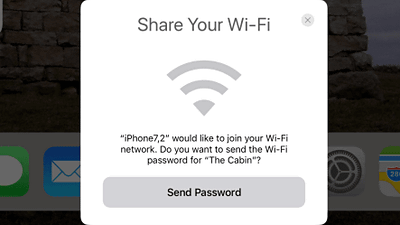
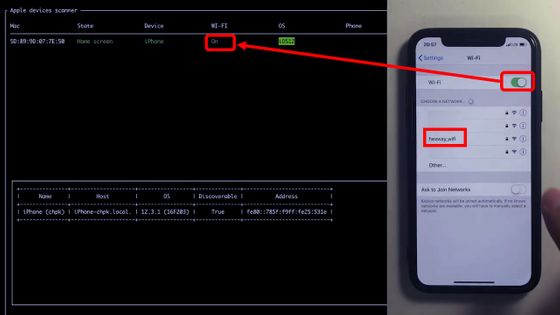
When you turn on Wi-Fi, the tool screen reflects it. Just tap the access point 'hexway_wifi' ...
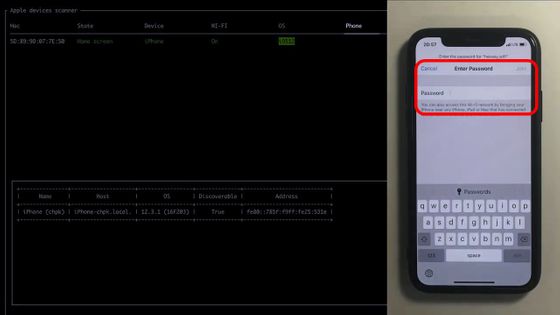
It returns to the home screen without entering a password or connecting to the access point.
Then, the name 'Dmitrij' appears in the information that has appeared in a large amount on the tool screen.
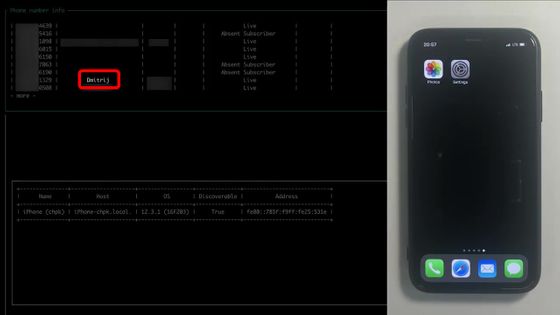
In a short time, the notification application of the iPhone receives notification ...
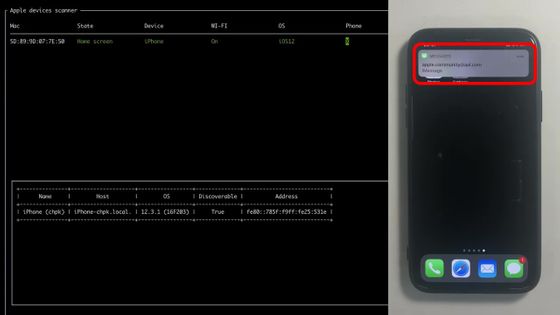
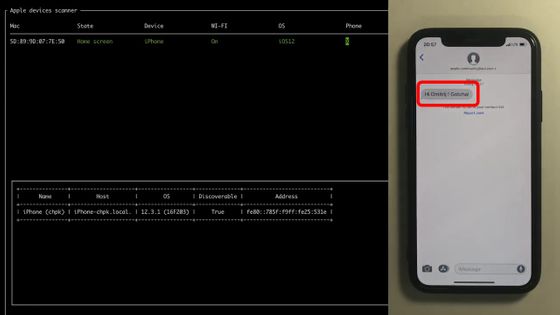
The message 'Hey Dmitrij, I found it!' Was displayed. This means that the contact has been leaked simply by trying to connect to the Wi-Fi access point.
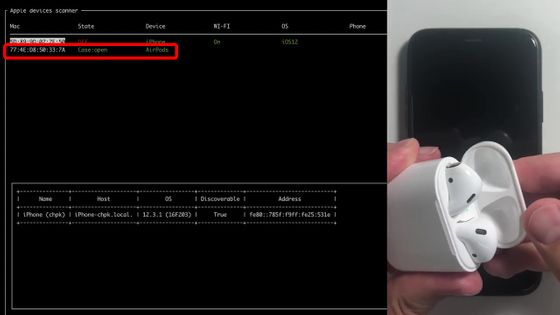
This bug is common to not only iPhone but also MacBook, Apple Watch and AirPods using AWDL. When the AirPods cover was actually opened, the AirPods status was displayed on the tool screen.
The defects found this time have been confirmed on all iOS 10.3.1 and later iOSs, including the next version OS 13 beta. Chastuhin said about this bug ' Vulnerable It's more of a feature that Apple's ecosystem has, rather than gender, 'he said, saying it was close to the spec.
The only solution that users can do is to 'turn off Bluetooth' at the moment of writing.
Related Posts: