What is two-step authentication that replaces password authentication and its future?
by Brian Ronald
On July 4th, 2019 (Thursday) at the
In the past, personal identification in the network has been carried out using an ID and password, but this method has the problem that if the password is leaked, it can be easily accessed by anyone other than the person. Therefore, two-step authentication is being adopted in which not only the ID and password but also an authentication code that only the user can know is used. The security company's Trail of Bits explains the future of such an authentication system.
Getting 2FA Right in 2019 | Trail of Bits Blog
https://blog.trailofbits.com/2019/06/20/getting-2fa-right-in-2019/
The authentication system is already in the stage of discussing 'what kind of authentication method to use' instead of 'password authentication or two-step authentication'. The Trail of Bits claims that it is important to authenticate 'user or user specific information' in 2-step authentication, and not to input information that the user knows. Also, the second method is not a substitute for the first step that uses an ID and password, it is merely a proof of identity.
So far, three main methods have been used for two-step certification. One method is to send a randomly generated authentication code to the user's registered telephone number using a short message service (SMS). The second method is to send an authentication code to the email address registered by the user. These two methods are secure at first glance, as the code is only sent to the device and user-specific email account associated with the phone number, but SMS and email can easily be intercepted by others. Because of this, it can not be said that this is a secure authentication method.
The third method is to use an algorithm called Time-based One-time Password (TOTP). The TOTP, which is a shared key cryptosystem (symmetric key cryptosystem), does not directly exchange the authentication code, but shares a secret key with the server and client using a QR code etc., and uses the secret key and time to authenticate the code. It is a way of generating. Therefore, it is safer than using email or SMS.
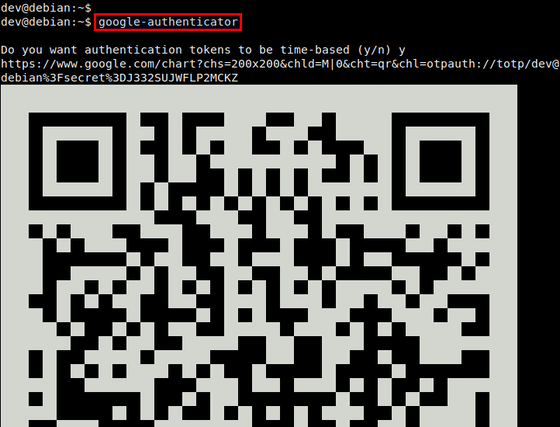
by Linux Screenshots
However, only the private key and the generator are shared by TOTP, and the authentication system adopting TOTP does not have the concept of individually recognizing terminals. If the secret key leaks out, a verification code can be generated, and access is possible regardless of the device, so 'the first secret key transmission / reception must be done with full privacy protection. There is a problem of
In particular, as general users do not understand 2-step authentication and its system, they tend to ignore security too much for convenience, the Trail of Bits points out, and the following actions are 2-step authentication It warns that it is the cause of not working well or causing metamorphosis.
• Keep a screenshot of the TOTP private key QR code and save it.
Load one secret key into multiple TOTP applications.
Use a TOTP application that can output the secret key in text format.
Save the recovery code for 2-step authentication bypass in a text file on the desktop.
-Ignore the 2-step verification completely and keep using only the recovery code.
・ We try to use old ID and old key as it is.
The focus is on FIDO, which was advocated for the next generation of online authentication technology standards in 2012. FIDO has two settings: Universal Authentication Framework (UAF), which is a standard that uses biometrics such as iris and fingerprint, and Universal 2nd Factor (U2F), which is a two-factor authentication standard. Furthermore, in November 2015, the specification called FIDO 2.0, which integrates the UAF and U2F, was released.
At the core of FIDO 2.0, 'WebAuthn', which Trail of Bits evaluates to be more secure than TOTP, is. By using WebAuthn, which is a JavaScript API of FIDO 2.0, it is possible to perform authentication based on FIDO even on a web browser. For example, previous web services only required authentication with an ID and password. However, with the spread of WebAuthn, not only two-step authentication becomes commonplace, but fingerprints and irises alone can be used to log in to web services.
Passwordless Login Method 'WebAuthn' Becomes Web Standard-GIGAZINE

Many TOTP applications are free and can be used on various platforms. On the other hand, WebAuthn is not yet available in a relatively new standard. According to Traile of Bits, Google and Apple are working on WebAuthn as a two-step authentication for mobile devices. If the implementation of WebAuthn by Google and Apple is realized and spread, it is expected that the online authentication system will accelerate the flow of replacing FIDO 2.0 from conventional password authentication and passwordless login will become commonplace.
Related Posts:
in Security, Posted by log1i_yk






