'RAMBleed attack' is discovered that steals data using memory vulnerability
A team of cybersecurity researchers is able to read important memory data from other processes running on the same hardware as a malicious program installed on the latest system on June 11, 2019. We clarified the details of the new
RAMBleed
https://rambleed.com/
RAMBleed: Reading Bits in Memory Without Accessing Them
(PDF file) https://rambleed.com/docs/20190603-rambleed-web.pdf
RAMBleed Attack-Flip Bits to Steal Sensitive Data from Computer Memory
https://www.manageengine.com/products/desktop-central/gdpr-comics.html
DRAM is a type of memory in which small capacitors are placed vertically and horizontally and electrically connected, and it is a mechanism that stores electric charge in the capacitors to store information. However, in DRAM, electrical interference occurs by repeatedly reading a specific memory address, and the charge bit of the adjacent row address is inverted or unreadable. Sex exists. The Rowhammer attack is a cyber attack that takes advantage of this DRAM vulnerability and rewrites the contents of the cell to gain authority.
'Rowhammer attack' similar cyber attack that can take authority by continuous access to storage such as SSD is possible-GIGAZINE

The RAMBleed attack discovered by research teams at the University of Michigan , Graz University of Technology and the University of Adelaide also applies DRAM vulnerabilities in the same way as the Rowhammer attack. However, unlike the Rowhammer attack that 'rewrites the contents of the cell and takes authority', the feature that 'it is possible to read information in protected memory belonging to other programs and users' is a major feature of the RAMBleed attack. That's it.
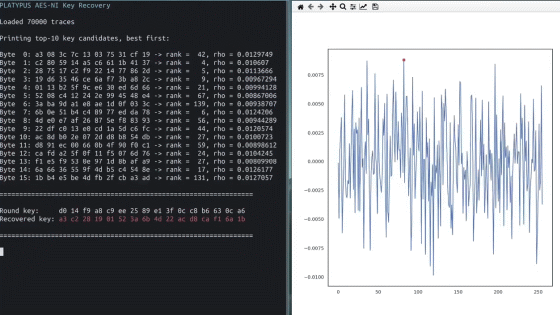
The research team states that 'an attacker who is a non-privileged user can guess the value of the adjacent row address by observing bit reversal caused by electrical interference in his memory.' In fact, the research team has reportedly launched an attack against OpenSSH 7.9 running on a Linux machine and succeeded in obtaining the RSA cryptographic secret key from sshd at the ROOT level.
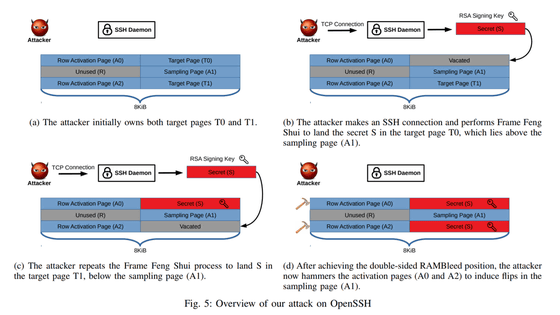
The research team said that the current standards for DRAM, DDR3 and DDR4, are both vulnerable to RAMBleed attacks. In addition, unlike Rowhammer attacks that aim to rewrite, RAMBleed attacks that read by guess do not require permanent bit inversion, so it is argued that ECC memory protection is also less effective. However, according to the research team, upgrading memory to DDR4 products with Target Row Refresh (TRR) reduced risk.
Related Posts: