Today is the day of 'Windows Update' every month

This month, Windows Security Updates and bug fixes were updated monthly, and Windows Update was released. Let's update early. In 2017, the villainy ransomware '
May 2019 Security Update (Monthly)-Japan Security Team
https://blogs.technet.microsoft.com/jpsecurity/2019/05/15/201905-security-updates/
'Security Update Program for May 2019 (Monthly)' describes the security update program released this month. https://t.co/SMdoTkEZ8s
— Microsoft Security Team (@JSECTEAM) May 15, 2019
The ransomware 'WannaCry', which exploits the vulnerability of Windows, caused a great deal of confusion all over the world in 2017. Microsoft prepares for the possibility that attacks like WannaCry will come back again, and it is not only new OS such as Windows 8 and Windows 10 with the update of May 2019, Windows XP, Windows 7, Windows Server 2003, Windows Server 2008 R2, Windows We also patch the old OS such as Server 2008.
'This vulnerability does not require user interaction. In other words, it is a self-propagation exploitable vulnerability, and the malware that exploits this vulnerability is vulnerable. It may spread from computers to other vulnerable computers like WannaCry, which ramped up in 2017. '
Prevent a worm by updating Remote Desktop Services (CVE-2019-0708) – MSRC
https://blogs.technet.microsoft.com/msrc/2009/05/14/prevent-a-worm-by-updating-remote-desktop-services-cve-2019-0708/
Microsoft warns of major WannaCry-like Windows security exploit, releases XP patches-The Verge
https://www.theverge.com/2019/5/14/18623565/microsoft-windows-xp-remote-desktop-services-worm-security-patches
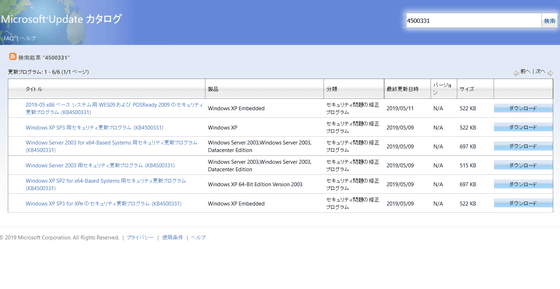
Although there is no evidence that this vulnerability has been exploited at this time, Microsoft says, but with the release of this patch, it is a matter of time for malicious hackers to reverse engineer the patch to create malware. You Although Windows 8 and Windows 10 are not affected by this vulnerability, there are still many computers using Windows 7 and the affected users need to take immediate action. In addition, Windows XP users need to manually download updates from the following Microsoft Update Catalog:
Microsoft Update Catalog
Other contents of Windows Update are as follows.
◆ Windows 10 v1903, v1809, v1803, v1709, v1703
Maximum severity:
emergency
The biggest impact:
Code is executed remotely
Related Knowledge Base or Support Web Pages:
Windows 10 v1903: 4497936
Windows 10 v1809: 4494441
Windows 10 v1803: 4499167
Windows 10 v1709: 4499179
Windows 10 v1703: 4499181
◆ Windows Server 2019, Windows Server 2016, Server Core installation s v2019, v2016, v1903, v1803
Maximum severity:
emergency
The biggest impact:
Code is executed remotely
Related Knowledge Base or Support Web Pages:
Windows Server 2019: 4494441
Windows Server 2016: 4494440
Windows Server v1903: 4497936
Windows Server v1803: 4499167
◆ Windows 8.1, Windows Server 2012 R2, Windows Server 2012, Windows 7, Windows Server 2008 R2, Windows Server 2008
Maximum severity:
emergency
The biggest impact:
Code is executed remotely
Related Knowledge Base or Support Web Pages:
Windows 8.1 and Windows Server 2012 R2 Monthly Rollup: 4499151
Windows 8.1 and Windows Server 2012 R2 Security Only: 4499165
Windows Server 2012 Monthly Rollup: 4499171
Windows Server 2012 Security only: 4499158
Windows 7 and Windows Server 2008 R2 Monthly Rollup: 4499164
Windows 7 and Windows Server 2008 R2 Security Only: 4499175
Windows Server 2008 Monthly Rollup: 4499149
Windows Server 2008 Security only: 4499180
◆ Internet Explorer
Maximum severity:
emergency
The biggest impact:
Code is executed remotely
Related Knowledge Base or Support Web Pages:
Internet Explorer Cumulative Update: 4498206
The Internet Explorer update is also included in the Windows update package above.
◆ Microsoft Office related software
Maximum severity:
emergency
The biggest impact:
Code is executed remotely
Related Knowledge Base or Support Web Pages:
Microsoft Office Knowledge Base Articles : 4462169 , 4464536 , 4464551 , 4464561 , 4464567
◆ Microsoft SharePoint related software
Maximum severity:
important
The biggest impact:
Code is executed remotely
Related Knowledge Base or Support Web Pages:
Microsoft SharePoint Server 2019: 4464556
SharePoint Enterprise Server 2016: 4464549
SharePoint Foundation 2013: 4464564
SharePoint Foundation 2010: 4464573
◆ Microsoft SQL Server
Maximum severity:
important
The biggest impact:
information leak
Related Knowledge Base or Support Web Pages:
Microsoft SQL Server 2017 for x64-based Systems (GDR): 4494351
Microsoft SQL Server 2017 for x64-based Systems (CU + GDR): 4494352
◆ Microsoft Dynamics 365
Maximum severity:
important
The biggest impact:
Security feature bypass
Related Knowledge Base or Support Web Pages:
Microsoft Dynamics 365 (On-Premise) Version 9.0: 4498363
Microsoft Dynamics 365 (On-Premise) Version 8.2: 4494412
Microsoft Dynamics CRM 2015 (On-Premise) Version 7.0 4499386
◆ Microsoft .NET Framework
Maximum severity:
important
The biggest impact:
Denial of service
Related Knowledge Base or Support Web Pages:
Knowledge related to the Framework .NET: 4499167 , 4494440 , 4495610 , 4495611 , 4495613 , 4495616 , 4495620 , 4498961 , 4498962 , 4498963 , 4498964 , 4499405 , 4499406 , 4499407 , 4499408 , 4499409 , 4499154 , 4499179 , 4499181
◆ .NET Core and ASP.NET Core
Maximum severity:
important
The biggest impact:
Denial of service
Related Knowledge Base or Support Web Pages:
.NET Core and ASP.NET Core: https://dotnet.microsoft.com/download/dotnet-core
◆ Microsoft Visual Studio
Maximum severity:
important
The biggest impact:
Elevation of privilege
Related Knowledge Base or Support Web Pages:
Contents of the update for Visual Studio: http://aka.ms/vs/16/release/latest and https://aka.ms/vs/14/release/4489639
◆ Azure DevOps Server, Team Foundation Server, Nuget
Maximum severity:
important
The biggest impact:
information leak
Related Knowledge Base or Support Web Pages:
Azure DevOps Server, Team Foundation Server, Nuget: For links and more information, see Security Update Guide. https://aka.ms/securityupdates
◆ ChakraCore
Maximum severity:
emergency
The biggest impact:
Code is executed remotely
Related Knowledge Base or Support Web Pages:
ChakraCore is a core part of Chakra, a high-performance JavaScript engine that enhances Microsoft Edge and Windows applications written in HTML / CSS / JS. For more information, visit https://github.com/Microsoft/ChakraCore/wiki . For more information, see Security Update Guide: https://aka.ms/securityupdates
◆ Adobe Flash Player
Maximum severity:
emergency
The biggest impact:
Code is executed remotely
Related Knowledge Base or Support Web Pages:
Knowledge Base Article for Adobe Flash Player on Affected Versions of Windows: 4497932
Security Advisory for Adobe Flash Player: ADV190012
Note that the actual number of updates varies depending on the combination of installed software. If you want to check the details, you can search from the Security Update Guide . If you include May 15 in the date range, you can capture the release notes and details of this month's security update.
Windows Update is published every second Tuesday in US time, and the next update is scheduled to be available on Wednesday, June 12, 2019 Japanese time.
Related Posts: