Approximately 800 million e-mail addresses and associated personal information leaked out, the e-mail verification service of the spill source goes offline with haste

by ribkhan
Security researchers Bob Diachenko and Vinny Troia discovered that more than 800 million email messages, including more than 700 million unique email addresses, were left unprotected on MongoDB .
800+ Million Emails Leaked Online by Email Verification Service - Security Discovery
https://securitydiscovery.com/800-million-emails-leaked-online-by-email-verification-service/
The 150 gigabyte database published on MongoDB was classified into four collections. In particular, the collection named "mailEmailDatabase" contains three folders named "Emailrecords", "emailWithPhone", "businessLeads", and Emailrecords: 789,171,891 cases, emailWithPhone 4.156 million cases, businessLeads 6.21 million 7358 pieces of information existed.
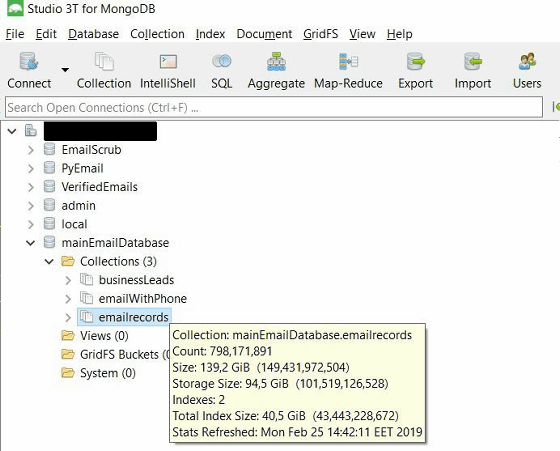
Emailrecords included personal information such as zip code, phone number, address, sex, user IP, birthday, in addition to the mail address.
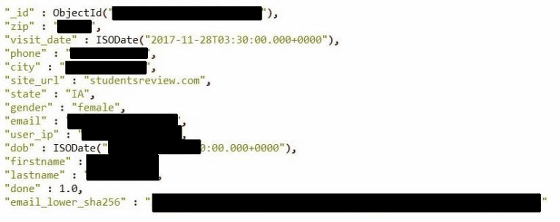
In addition, there were many records that included information such as home loans, interest rates, Facebook and Instagram linked to e-mail address, account of LinkedIn, characteristics of credit information (average, above average etc.). And in another collection there was information used for business promotion such as company name · annual sales · company's website · fax number and company identification code such as "SIC" "NAIC". On the other hand, social security numbers, credit card numbers, etc. were not included.
Although we surprised the researchers in that the number of data that flowed out was enormous, it also differs from the usual information leakage also in that it included corporate profits and employee data called business intelligence data It was. It is believed that this is because the source of information leakage was the email verification service "Verifications.io". Verifications.io said it was offline that day that Diachenko mailed the data leak to customer support.
Not being widely known, "E-mail verification service" which checks whether e-mail address is valid plays a very important role in marketing. Marketing companies and companies want to reliably deliver spam mails. However, many of the marketing companies have customers' email address list, but I do not know if their email address is valid. Therefore, we will consign to external service like Verifications.io that sending mail to the mail address in the list to distinguish between 'properly arriving address' and 'bouncing address'. Mr. Troia pretends that "It is not confirmed", but I think that the vast amount of data that flowed out is due to the inclusion of all customer data from Verifications.io.
Even if a malicious attacker wants to hack a company, even if you have acquired a large number of highly-qualified email addresses and passwords, logging into a system or service using that single account It is very laborious and time consuming. However, if you upload this list of mail addresses to a service like Verifications.io, Verifications.io sends a confirmation email to the user, and by looking at which email address is bounced back, You can check the "effective address to". This allows a malicious attacker to obtain the "effective address" of the target company.
Verifications.io's reply to Mr. Diachenko's mail is very fast and it is said that the contents of "you discovered data are public and there is no client data" was explained by e-mail. Has been closed and there is no reason for the service being taken offline, "says Diachenko. Since the database included contents such as user list, access to the FTP server and credential information for uploading / downloading the list, "Diaghenko sees that the leaked information is not public data" .
Related Posts:
in Security, Posted by darkhorse_log