Chrome Web Store rules are revised, so that users can use Chrome extensions more securely

by geralt
A major advantage of Google's web browser " Google Chrome " is that you can install rich extensions to make browsing more convenient from the Chrome Web Store . Google announced a new rule for such Chrome Web Store and reveals a policy of "making users more secure to use Chrome extensions".
Chromium Blog: Trustworthy Chrome Extensions, by default
https://blog.chromium.org/2018/10/trustworthy-chrome-extensions-by-default.html
Google to no longer allow Chrome extensions that use obfuscated code | ZDNet
https://www.zdnet.com/article/google-to-no-longer-allow-chrome-extensions-that-use-obfuscated-code/
With Chrome extensions, users can take advantage of very useful features, and as of the year of 2018 when Chrome was released in 2008, there are indeed more than 180,000 extensions I will. According to Google, more than half of users using desktop Chrome are using some Chrome extensions. On the other hand, there is a problem that poorly secure extensions and malicious extensions that are dangerous to users are secretly missing in the Chrome Web Store.
Google said, "It is important that Chrome extensions allow users to use various extensions to meet their needs, developers to develop and provide rich extensions, but more importantly, The function is safe, it is that it protects the user's privacy and it is reliable. "It states that the extended function needs to have high transparency about its function and data access authority . So Google has established a new rule on the extensions that will be published in the Chrome Web Store.

◆ 1: Prohibition of extended function using obfuscated code
Obfuscated code is a code that is processed in a way that human beings can not intentionally understand the procedures and structures of internal actions. This is different from compressed code for performance improvement, it is hard to judge externally what kind of procedure is being done even if you look at the source.
According to Google, 70% of extra malicious Chrome extensions that Google already removes from the Chrome Web Store are using obfuscated code. Google plans to remove the extension using the obfuscated code from the Chrome Web Store as "there is no performance benefit in using obfuscated code". For the Chrome extension that already uses the obfuscated code already released, we will set up a grace period for code modification until January 1, 2019, but if the obfuscation code remains after the deadline, It is said to be deleted from the web store.

by marissa anderson
◆ 2: New extension review process
From 1st October 2018, we will begin a new review process for the extensions to be registered in the Chrome Web Store. In the new review process, we will impose "additional compliance review" on the extensions that require substantial authority for browsers.
Some advanced functions require authority beyond the range necessary for the function currently being provided as "There is a possibility that it may be necessary when new functions are added in the future". However, we believe that it is preferable to "narrowly expanded extensions" rather than extensions that require more authority than necessary.
In addition, Google insists that if the extension uses code provided by the remote host , developers can replace the code they provide at run time. It seems that "extensive monitoring" will be performed on the extension function that executes the code of the remote host, as malicious code can be provided after going through the extension review.

by Christiaan Colen
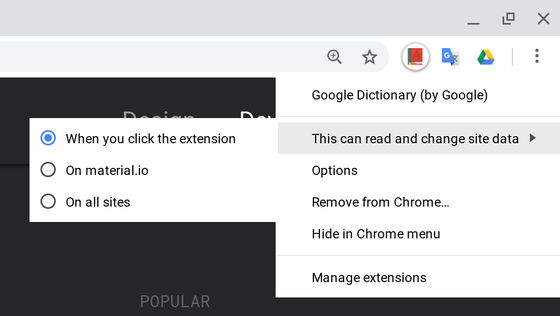
◆ 3: Approve extension feature permission on a site basis
In "Chrome 70" planned to be released in October 2018, Google will be able to set such that the website to which the extension is applied is restricted to specific websites only. This setting states that the extension has a purpose to prevent dangerous actions on highly confidential sites such as login page to bank's online account, wallet of encryption currency, inbox of e-mail, etc.
Also, in Chrome 70, it is possible to make settings such as "Allow application of extended functions only when clicked". In other words, it seems possible to restrict the extended function to start operation only when you click on a specific icon or option page after opening the web page.
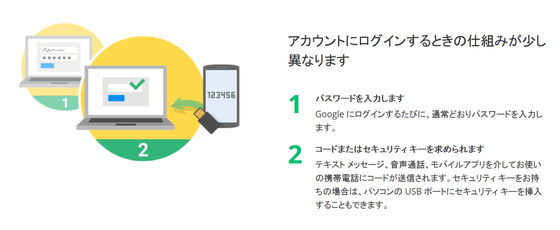
◆ 4: Two-step verification process for developers
The fourth rule is not intended for users who use extensions, but rules for developers of extensions. In order to counter phishing scams rampant on the Internet, Google decided to require all developers of extension to request 2-step verification at account login.
This prevents a malicious third party from hacking the developer's account and inserting malicious code into the extension provided by the developer. By enhancing the protection of the developer account with 2-step verification, we are stating that we will keep the extension and reliability against Chrome.
Google Chrome will continue to seek more powerful security, privacy protection and performance guarantee for Chrome extensions.
Related Posts:
in Software, Web Service, Security, Posted by log1h_ik