Technology to unleash the 'pattern' of unlocking by acoustic tracking using the speaker & microphone of smartphone appeared

Attack methods aiming at smartphones, which are treasures of personal information, are being developed one after another. The side channel attack " SonarSnoop " newly devised by researchers seems to be able to specify the "pattern" operation to release the lock screen by using the speaker & microphone of the smartphone.
[1808.10250] SonarSnoop: Active Acoustic Side-Channel Attacks
https://arxiv.org/abs/1808.10250
Researchers Used Sonar Signal From a Smartphone Speaker to Steal Unlock Passwords - Motherboard
https://motherboard.vice.com/en_us/article/kzyd4m/researchers-used-sonar-signal-from-a-smartphone-speaker-to-steal-unlock-passwords
Dr. Jeff Yang's research team at the University of Lancaster announced a research on the side channel attack called "SonarSnoop". With SonarSnoop, you can steal "pattern" that tracks user's finger movement and releases the lock screen by using the smartphone's speaker and microphone.
Technical idea is to use object recognition using sound. By issuing an echo of a certain frequency, we can recognize the position, size and motion of the object from the reflected wave, but researchers succeeded in tracking the movements of the user's fingers using this acoustic technology It is.

Specific attack situations are as follows.
First, it infects the target user's terminal with malicious software that launches SonarSnoop attack. Terminals infected with malware will emit sound signals from speakers, collect reflected sounds from surrounding objects, and scan the situation. After that, it detects the movement of the finger when the user unlocks, reads the pattern from the movement, and takes the full access path to the smartphone.
In addition, since the microphone & speaker of the smartphone is used, the accuracy of SonarSnoop is not so high. However, it seems that it is possible to see the correct answer out of several patterns. According to a survey, there are 400 thousand alternative patterns, but the patterns that users actually use are limited, and that there are 20% who set one of the following 12 patterns I know that. Therefore, in this research, I examined the accuracy of SonarSnoop by asking a subject to perform unlock operation by one of the following 12 patterns.
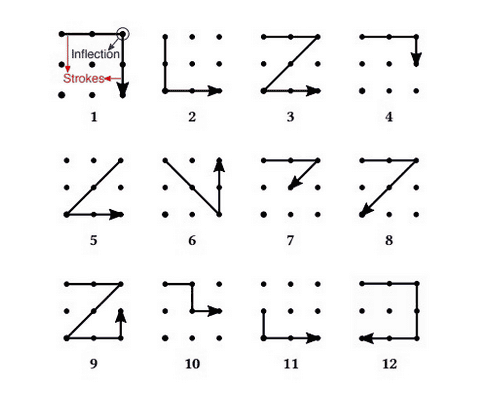
In the experiments, 10 subjects performed 5 pattern operations of the above 12 types using a relatively old Android terminal called Samsung's Galaxy S4 released in 2013, and movement was read by SonarSnoop . As a result, SonarSnoop was able to find patterns on an average of 3.6 trials. I succeeded in reducing the labor of the task of identifying one out of 12 patterns by 70%. Although the old Android terminal is used in the experiment, the attack itself is also possible on the iPhone. Penn Chen, a graduate student who participated in the research if it is a terminal equipped with a speaker and a microphone, can track with SonarSnoop, says.
Of course, the SonarSnoop attack developed in this research does not immediately become a real threat in terms of accuracy. However, as long as there is a need to exploit smartphones, which is a treasure house of personal information, cyber attacks trying to access information by making full use of technology are surely developed more and more, and incorporating ecological certification etc. It seems that the user never made it self-defense.
Related Posts:







