What is the threat of SIM hijack where phone number is robbed?

Although it is a SIM card that is necessary for telephone and data communication with smartphones and others, there is an increasing trend of "SIM Hijack" in the United States where SIM cards are taken over. In addition to not being able to make calls and data communication on their own terminal if they are taken over from the SIM card, it is said that SNS two-factor authentication is abused and SNS accounts are taken over. What is hacker doing SIM hijacking aiming at, what is the reason for the reason is oversea media Motherboard .
The SIM Hijackers - Motherboard
https://motherboard.vice.com/en_us/article/vbqax3/hackers-sim-swapping-steal-phone-numbers-instagram-bitcoin
In September 2017, Rachel Ostrund living in Salt Lake City was exchanging messages with his sister. Then, a message saying "SIM card was updated" arrived from T-Mobile contracted by Rachel, and data communication could not be performed immediately after this. When her husband Adam told this phone story, I tried calling Rachel 's cell phone, I confirmed that the ringing sounded, but Rachel' s cell phone did not respond and no one answered the phone It is said that.
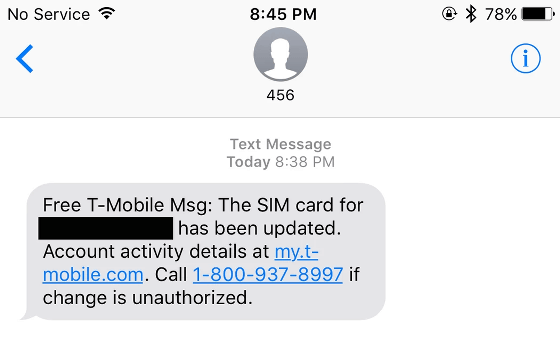
So, Adam once again called up Rachel 's number. Then I got a response with a strange voice "Rachel." Adam seemed surprised, but when asking, "You are not Rachel, what did you do?", There was only a reply from the other person saying "It is destroying your life" That's right. At this time hackers took over hackers accounts of many web services such as Instagram, Amazon, Netflix etc which Rachel 's phone number was already registered.
After the occurrence of this incident, the same kind of damage will be continued. And in about February 2018, about five months after Mr. Rachel's incident, T-Mobile came to send a warning message to the contractor about "the threat of SIM hijacking".
This SIM hijacking method is very easy, and if you prepare to some extent in advance, there is a characteristic that anyone can do it. First of all, I inform the support of the career and tell "I lost the ○○ (target) SIM card." After that, ask the hacker to have the phone addressed to the target transferred to the new SIM card number owned or to have the SIM card rewritten. Of course, you will be asked for identification from your career, but you can respond by checking the address and social security number of the target person in advance, so you can easily do SIM Hijacking.
The SIM card has the feature that it can not have the same SIM card on the cellular phone network. Since the last updated SIM card is treated as being correct, if it is updated to a third party, there is a problem that the phone number is deprived. Because phone numbers are often used for two-factor authentication of SNS and many web services, receiving SIM hijacking means that there is a possibility that the account of the service registering the telephone number is also hijacked It becomes high.
"Unfortunately many web services are not taking security measures assuming SIM hijacking," says Roel Schweenberg, who is in the security company's Celsus Advisory Group , saying that phone numbers are never safe, We assume that many web services used as the last key of authentication are not security-friendly.

It is also obvious that the aim of hackers doing SIM hijacking is not phone number. According to a hacker, SIM Hijack is going to hijack SNS accounts. SNS accounts that were taken over are traded on the back market, especially for IDs with a small number of characters and IDs with specific meanings, they are said to be traded at high prices. According to another hacker, "The" @ t "Instagram account has been traded for about $ 40,000 (about 4.52 million yen)". In the case of Mr. Rachel, since the Instagram account was "@ Rainbow", it is considered to have been hacked by a hacker as being a cool ID name.
Familiar with the crime of SIM card Recorded Future Mr. Andrei Barisebitchi of security researchers who serve in the "if you know even how to replace the SIM card, that would earn a lot of status quo is money" and said that, in the future We expect to increase the damage of SIM hijacking.
Related Posts: