The existence of the API for Office 365 that Microsoft kept confidential becomes clear
By self thy
Office 365 is widely used in business applications because it can collaborate on Word and Excel files regardless of location or device, and can check email with Outlook. However, due to the account being hijacked, confidential information may be deprived, so Office 365 was convenient but there was a high possibility of security damage being high. According to Sherry Davidoff, CEO of security company LMG Security , it may be possible to mitigate the threat by using the API which was disclosed on June 18, 2018.
Exposing the Secret Office 365 Forensics Tool | LMG Security: LMG Security
https://lmgsecurity.com/exposing-the-secret-office-365-forensics-tool/
The API whose existence was revealed this time is the Activities API of Office 365. By using this API it became possible to examine the details of processing done in Office 365 mailbox in detail. With this tool, Davidoff says, "This is big news" because it enabled you to examine what was operated in the last 6 months without enabling the audit log function.
Mr. Davidoff explained about the benefits of the Activities API as "Especially contracting with lawyers and contracting audit logs to record detailed data at Office 365 will be very effective for harsh enterprises" , It explains that it is very useful for small companies without budget.

The Activities API had existed before, but Microsoft kept the existence of the API secret. Davidoff explains why this API was revealed.
In the past, hackers around the world have taken Office 365 's email account "some way" to deprive corporate confidential information and employee personal information. Of course, companies that noticed the intrusion of hackers will investigate "what hackers saw and what took away". Here, if it is clarified that there is no data leakage fact in the survey of the log etc., there is no duty of public disclosure, there is no damage to the company.
However, in the case of Office 365, since the log function is not enabled by default, the work history done in the mailbox is not left. For this reason, companies that are unable to prove that there is no damage, even if the company has not suffered any damage after hacker invasion, are obliged to announce that there was a data leak. Naturally, companies that announced data leakage received a great deal of damage including penalties associated with fines, data leakage, and declining corporate image.
One day, Mr. Davidoff received a question from a manager of a legal affair of a large corporation "There seems to be a secret tool of Office 365". Mr. Davidoff who did not know anything about the secret tool at the time, he later became interested by listening to the rumor that "Microsoft programmers are using secret tools after changing to law firm" .

Mr. Davidoff had the opportunity to meet with Microsoft's IT team in-house, so that under the condition that "conversation is not recorded", the existence of a secret tool for multiple people including Office 365 developer through two people I confirmed. However, all of them answered "I do not know" and the men also testified that they did not seem to be lying. Even so, Mr. Davidoff consulted with a lawyer "I know the existence of the tool", and in fact I get the information that the tools are being used at five law offices. Mr. Davidoff further investigated and finally found out the existence of the Activities API on June 8, 2018.
CROWDSTRIKE has released a blog post on the Activities API and a Python module for log search on June 18th after 10 days. LMG Security team led by Mr. Davidoff also introduced the released Python module and decided to verify the ability of Activities API in test environment.
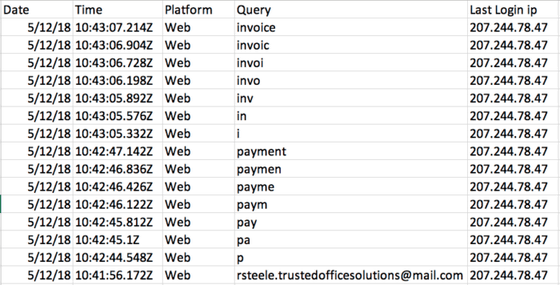
Then, search history in Office 365 mailbox searched with "invoice" or "payment" keywords ... ...
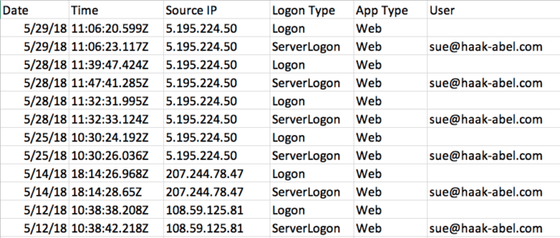
Mr. Davidoff confirmed that the login history and the information of the connection source IP address etc are displayed, and it seems that he was convinced that "It is a useful tool".
Davidoff said, "The Activities API is only known to some Microsoft people and some law firms, and those who do not know the existence of this API need a high-priced service It is necessary to sign a contract. "It is pointed out that receiving a log offering service to prevent the threat of hacking has a tough situation in companies with low budget. So he said "LMG Security will actively disclose the existence of this tool," he also announced that LMG Security has released a wrapper tool using CROWDSTRIKE's Python module on GitHub It is.
Related Posts:
in Web Service, Security, Posted by darkhorse_log







