Damage caused by malware "VPNFilter" that intercepts traffic via Router / NAS and creates man-in-the-middle attacks is expanding

Routers andNetwork Attached StorageNew malware targeted at NAS (NAS) "VPN FilterThe presence of "is reported by Symantec of a security company. According to Symantec security researchers, VPN Filter can monitor network traffic via infected devices,Man-in-man attackIt is possible to set up a malicious code or insert malicious code.
VPN Filter: New Router Malware with Destructive Capabilities | Symantec Blogs
https://www.symantec.com/blogs/threat-intelligence/vpnfilter-iot-malware
Cisco's Talos Intelligence Group Blog: VPNFilter Update - VPNFilter exploits endpoints, targets new devices
https://blog.talosintelligence.com/2018/06/vpnfilter-update.html
VPNFilter malware infecting 500,000 devices is worse than we thought | Ars Technica
https://arstechnica.com/information-technology/2018/06/vpnfilter-malware-infecting-50000-devices-is-worse-than-we-thought/
Malware targeting routers and NAS "VPNFilter" was reported in May 2018 as malware infecting more than 500,000 in 54 countries.
Malware "VPNFilter" malware infecting more than 500,000 network devices in 54 countries, suspected that the state is involved in the creation - GIGAZINE
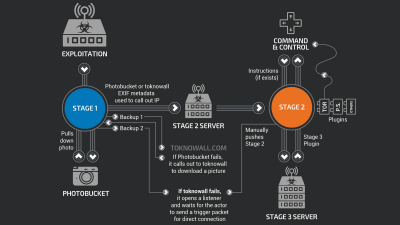
The investigation has gradually revealed the full picture of the attack,SCADAIt is being used to intercept the traffic of industrial control systems like such as infection and adding infection little by little with the infection, eventually intercepting the communication contents, making the infected terminal unusable It is clear that it is possible to do.
After infecting the firmware, VPN Filter adds a setting to run itself to crontab which executes a specific command at regular time intervals. This makes it possible to maintain malware activity even if the terminal is restarted. continue,C & C serverTo download modules for enabling collection of files, execution of commands, extraction of data, device management, etc. This allows you to overwrite a part of the firmware of the infected device and reboot it if it is instructed by an attacker so that it can go into an unusable state. In addition, he seems to be able to steal web site credentials, monitor Modbus's SCADA protocol, or use Tor to communicate with the outside.
The newly discovered "ssler" module can intercept all traffic passing through the device via port 80. In addition, since HTTPS request can be changed to HTTP request, it will interfere with encryption of communication contents and steal confidential information from traffic. You can also use the module "dstr" to remove any traces of VPN Filter from infected devices.

According to Cisco Talos, the activities of VPNFilter have increased since May 2018, and attackers said there are targets specifically targeting Ukraine. Unlike other malware that is a threat to IoT such as Mirai, VPNFilter is not malware that attempts to scan a vulnerable device to indiscriminately infect it.
Although most of the terminals that may be infected with VPN Filter are using the authentication information at the time of purchase as is, at the time of article creation, the abuse of the zero day vulnerability has not been confirmed.
The list of devices that may be infected by VPN Filter is as follows. Enterprise and small office routers such as ASUS, D - Link, Huawei, Linksys, MikroTik, Netgear, TP - Link, Ubiquiti, Upvel, ZTE etc, NAS etc are infected.
· Asus RT-AC 66U
· Asus RT-N10
· Asus RT-N10E
· Asus RT-N10U
· Asus RT-N 56U
· Asus RT-N66U
· D-Link DES-1210-08P
· D-Link DIR-300
· D-Link DIR-300A
· D-Link DSR-250N
· D-Link DSR-500N
· D-Link DSR-1000
· D-Link DSR-1000N
· Huawei HG 8245
· Linksys E 1200
· Linksys E2500
· Linksys E3000
· Linksys E3200
· Linksys E4200
· Linksys RV 082
· Linksys WRVS 4400N
· MikroTik CCR 1009
· MikroTik CCR 1016
· MikroTik CCR1036
· MikroTik CCR 1072
· MikroTik CRS 109
· MikroTik CRS 112
· MikroTik CRS 125
· MikroTik RB 411
· MikroTik RB 450
· MikroTik RB 750
· MikroTik RB 911
· MikroTik RB921
· MikroTik RB 941
· MikroTik RB 951
· MikroTik RB 952
· MikroTik RB 960
· MikroTik RB962
· MikroTik RB 1100
· MikroTik RB 1200
· MikroTik RB2011
· MikroTik RB 3011
· MikroTik RB Groove
· MikroTik RB Omnitik
· MikroTik STX 5
· Netgear DG 834
· Netgear DGN 1000
· Netgear DGN 2200
· Netgear DGN 3500
· Netgear FVS 318N
· Netgear MBRN 3000
· Netgear R6400
· Netgear R 7000
· Netgear R 8000
· Netgear WNR 1000
· Netgear WNR 2000
· Netgear WNR 2200
· Netgear WNR 4000
· Netgear WNDR 3700
· Netgear WNDR 4000
· Netgear WNDR 4300
· Netgear WNDR 4300-TN
· Netgear UTM 50
· QNAP TS 251
· QNAP TS439 Pro
· Other QNAP NAS terminals (those running QTS software)
· TP-Link R600 VPN
· TP-Link TL-WR 741ND
· TP-Link TL-WR 841 N
· Ubiquiti NSM 2
· Ubiquiti PBE M5
· Upvel terminal (model unknown)
· ZTE ZXHN H108N
Symantec recommends that users with terminals that are likely to be infected with VPN Filter be restarted, and if the terminal is infected, some functions are deleted by rebooting, disabling the terminal It will be able to prevent being done. However, as VPNFilter is not completely deleted even after rebooting, there is a danger of downloading additional modules again, so we recommend that you apply the latest patch and not use the authentication information at the time of purchase It is.
Related Posts: