CIA's unknown method "Cherry Blossom" rewriting the farm of the Wi-Fi router to make it a hacking tool is lightened from the document of Wikileaks

It is overwhelmingly rewritten the Wi-Fi router's firmware on the market, which is unmistakable, and the entire browsing status of the net is intercepted ... ... Such an amazing hacking system "Cherry BlossomIt was clarified from confidential documents released by Wikileaks that the American CIA (Central Intelligence Agency) was developing and using it.
Wikileaks Unveils 'Cherry Blossom' - Wireless Hacking System Used by CIA
https://thehackernews.com/2017/06/cia-wireless-router-hacking-tool.html
The CIA has lots of ways to hack your router - The Verge
https://www.theverge.com/2017/6/15/15812216/cherryblossom-cia-router-hack-surveillance-dlink-linksys-belkin
According to a document published by Wikileaks, Cherry Blossom is a tool developed by CIA, and it was operated to monitor the behavior of the person to be investigated. By rewriting the firmware of the router it makes it possible to intercept the entire contents of the communication via the router and in some cases even access to the site can even be redirected intentionally to another site.
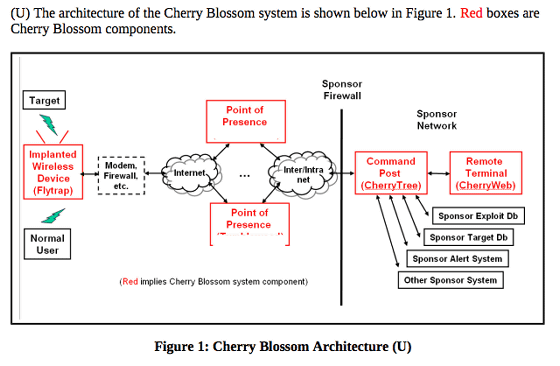
The outline is shown in the operation manual. The red part is the part involved with Cherry Blossom 's tool, Cherry Blossom accesses the survey' s Wi - Fi router from the place protected by the firewall, and performs modification to make it possible to monitor data sampling It seems to make it possible.
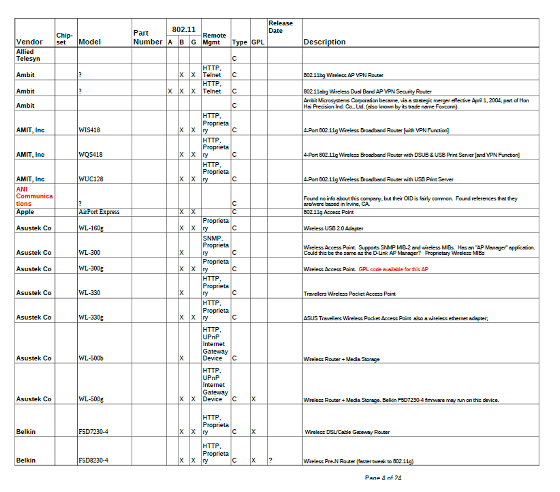
According to the manual, the Cherry Blossom has multiple versions exist, things that become the contents corresponding to each particular manufacturer or brand of the model.(PDF)List of Wi-Fi devicesAccording to the document, ASUS, Apple, Berkin and other models of familiar brands in Japan are included.
About operation method The manual states "In the case of typical operation, incorporate Cherry Blossom firmware into the surveyed wireless device by Claymore tool or operation in the supply chain". In other words, there are two ways to incorporate Cherry Blossom: a method using a tool called "Claymore tool" and "operation in supply chain" exist. There seems to be no description of what the Claymore tool is in the manual, but where the operation in the supply chain is concerned. It can also be understood that the operation is carried out somewhere in the supply chain, that is, from the factory shipping products to the end user, and that "cooperators" exist somewhere in the distribution channel It is also a content that gives a message.
From the published document, it is not clear how much Cherry Blossom is actually used, and it is unclear whether it is operated as of 2017 or not.
Documents released by Wikileaks can be referred to in detail from the following pages.
WikiLeaks - Vault 7: Projects
https://wikileaks.org/vault7/#Cherry%20Blossom
Related Posts: