The malware "CrashOverRide" that caused the Ukraine's blackouts has the potential danger of confusing the power grid and can cause disasters worldwide

A security expert discovered that the cause of the blackout occurred in Ukraine is malware that causes transmission system to fail. Because this malware does not rely on specific communication equipment and it has extensibility, it is pointed out that there is a danger of causing confusion in the power grid around the world.
Dangerous Malware Discovered that Can Take Down Electric Power Grids
http://thehackernews.com/2017/06/electric-power-grid-malware.html
In December 2016, a blackout occurred in the northern part of Ukraine's capital city of Kiev for about 1 hour and 15 minutes, and tens of thousands of residents experienced a dark night. ESET, a security software based in Slovakia, and Dragos, an infrastructure security company in the United States, investigated the cause of Ukrainian blackouts,Industroyer"Or"CrashOverRideIt was revealed that malfunction called "transmission grid failure" occurred.
Hacking attacks on infrastructure equipment such as electricity transmission networks that greatly influence the lives of citizens originate in malware "Stuxnet" developed by the United States in 2009 to destroy nuclear facilities in Iran, but since the end of Stuxnet, Ukraine CrashOverRide that caused the blackout is the biggest threat, security researchers have said.
Unlike Stuxnet, CrashOverRide is a software vulnerability aimed at "Zero-day attackIt does not use the characteristic point. It is a feature of CrashOverRide that exploits four industrial communication protocols that are used globally in important infrastructure systems such as power infrastructure and power transmission control system, rather than exploiting software vulnerabilities. Malware first installs the four payload components to control the power switch and circuit breaker, and then becomes itself a backdoor to secure the communication circuit with the remote server and can receive instructions from the attacker I was to wait.
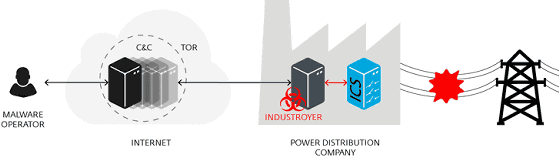
The control system of switches and circuit breakers used by electric utilities at substations was designed several decades ago, sneaking into this system, disconnecting power supply arbitrarily and concealing the occurrence of failures, CrashOverRide is designed to cause failure of power transmission system. In addition, CrashOverRide seems to have multiple functions that hide all traces and hide in the system so that they can stay long in the system and cause a failure, hiding all the traces after the attack. Security researchers at ESET point out that "Developers of CrashOverRide have considerable knowledge and a deep understanding of industrial control systems."
Security researchers at ESET and Dragos analyzed CrashOverRide and found that it was refined so that it could be attacked in a wider range rather than just for Ukrainian power outage. Since CrashOverRide includes interchangeable plug-in components, it is also possible to change the target power company or attack multiple electric power companies at the same time. Security researchers at ESET and Dragos said that "CrashOverRide is not dependent on a specific company or specific system, but considering the design of the transmission grid and network communication, and in some countries in Europe, the Middle East and Asia CrashOverRide is extensible and incorporates the DNP 3 (Distributed Network Protocol 3) protocol stack, so attacking the North American power grid with minor modifications It is also possible. "
Dragos security researcher believes that behind CrashOverRide, there is a hacker group "Sandworm" that caused a blackout in Russia in 2015. Security researchers have warned government authorities and power companies in each country about malware threats and advised to prevent malware attacks.
Related Posts: