Abuse of application privilege to record key input · Password stealing · Application installation with malware etc You can do whatever you want You can vulnerable "Cloak and Dagger" is hard to solve with Android design problem

By combining legitimate authority required for Android application, you can copy all the input information of the software keyboard, steal the contacts up, steal the contacts, install the unauthorized application in God mode giving all the privileges We are all weakly weak Sex was discovered. This vulnerability problem is "Cloak and DaggerA researcher at the Georgia Institute of Technology discovered that "This vulnerability is attributable to Android's design philosophy by Google and it is difficult to block the hole".
Cloak and Dagger: From Two Permissions to Complete Control of the UI Feedback Loop
(PDF file)http://cs.ucsb.edu/~yanick/publications/2017_oakland_cloakanddagger.pdf
Combination of features produces new Android vulnerability - ScienceDaily
https://www.sciencedaily.com/releases/2017/05/170523083601.htm
Cloak and Dagger is an attack that exploits the authority "draw on top (SYSTEM_ALERT_WINDOW)" "a11y (BIND_ACCESSIBILITY_SERVICE)" alone or in combination with the authority granted to the Android application, and these authorities explicitly request permission Because it is used, the user is not notified.
Cloak and Dagger explains the concrete hacking method that an attacker can do with a movie, and it is supposed to make it snake.
· Invisible grid attack
You can check how the contents entered by the key are going to go through in the following movie.
Cloak & amp; Dagger: Invisible Grid Attack - YouTube
The key idea is "blindfold" ... ...

Invisible grid generation in "screen overlay".

By combining these, you can read "What did you key in?"
If you put a check in "Make Attack Visible" of the verification application made to make the contents of attacks easy to understand ......
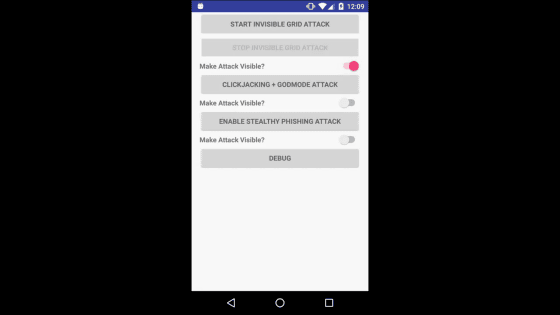
In the lower half of the screen, a grid hidden by the overlay was displayed.
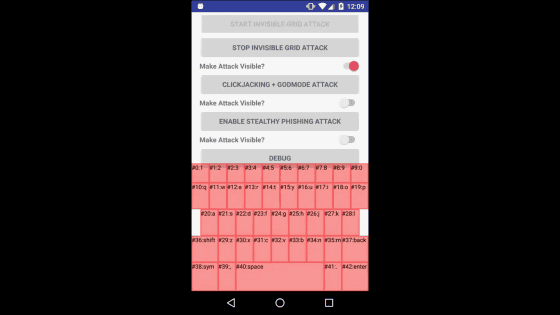
The grid is also hidden on the home screen.

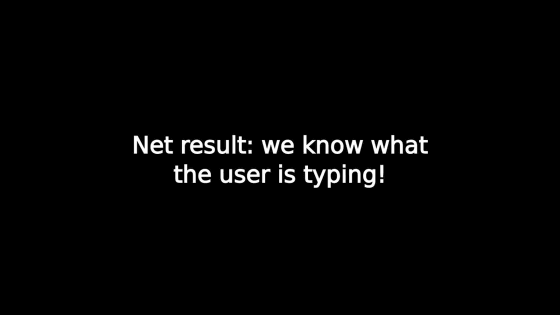
The grid that corresponds to the software keyboard perfectly is tapped each time the key taps, and it is reading the input contents. Users will notice that they are being attacked.
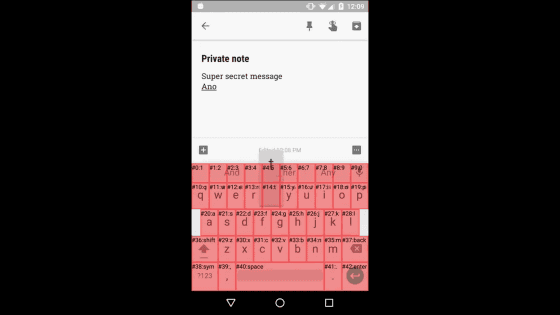
Secret password stealing attack
If you exploit overlay and a11y (accessibility), you can also steal passwords.
Cloak & amp; Dagger: Stealthy Phishing Attack - YouTube
Facebook app login screen.
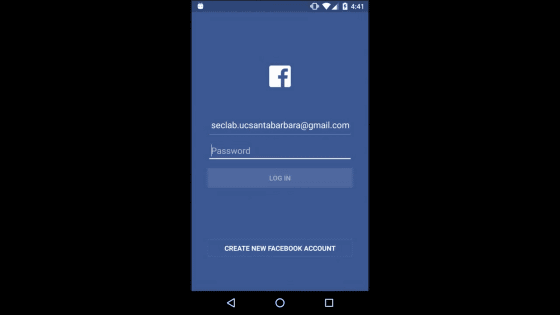
Enter your password.
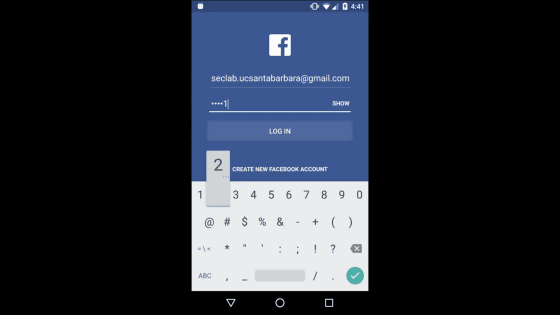
Successfully logged in.
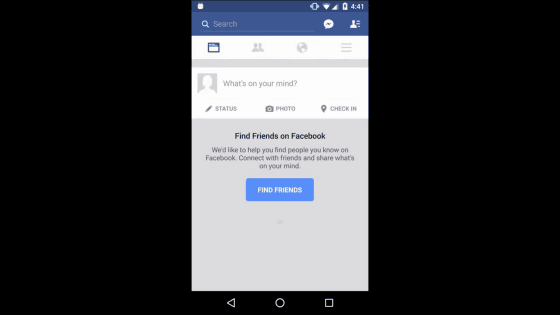
According to this operation, the password has already been stolen.
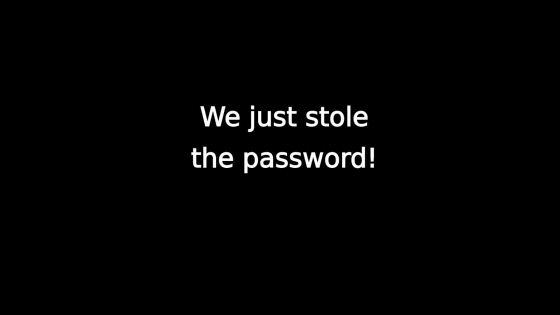
It seems that keyloggers hidden by overlay were prepared in this form.
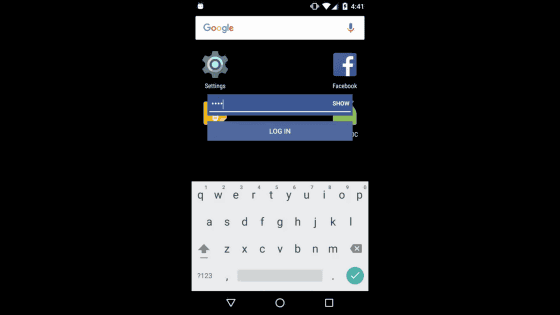
· Unauthorized installation of malicious application
You can install malicious apps without permission by exploiting "draw on top" and "a11y" authority in combination.
Cloak & amp; Dagger: Clickjacking + Silent God-mode App Install - YouTube
The first thing to do is to enable "a11y".

I will run an application made for experiment called "C & D POC".

There seems to be a tutorial at the first start. Tap "START TUTORIAL".
The droid seems to guide you. Tap "NEXT".
I was ready to see the movie, so tap "OK".
The movie has started.

At this point a11y is said to be validated.
The movie is over ......
The tutorial is over.
Explaining what happened during the tutorial is as follows.

The act of tapping to start the tutorial was simultaneously activating accessibility.
"NEXT" "OK" Each button has different work hidden ... ...

The application will be installed without permission.
Each work that advances automatically behind the movie playback.
All access permission is also set to "ON".
Finally erase the history ... ....
Return to the home screen ......
Installation of the unauthorized application is completed. Users will never notice even if they install apps containing lots of malware without permission.
Research teams such as Yanick Fratantonio and colleagues at the University of California at Santa Barbara at the University of California at Santa Barbara, who discovered Cloak and Dagger, Yanick Fratantonio and colleagues during the summer interns tested the application using the Cloak and Dagger method with 20 subjects, There was no one who found out that it was done. It seems to be said that it is very difficult to notice attacks once you install and use malicious apps.
In Cloak and Dagger, a function "BIND_ACCESSIBILITY_SERVICE" (a 11 y) for supporting audio-visual disabled people by inputting a user name and a password with a voice command or allowing output to a screen reader, and a chat application or a map application It is an attack technique that exploits one or both of the two privileges "SYSTEM_ALERT_WINDOW" (draw on top) to make it possible to draw on the screen used in. When attacking in combination, "SYSTEM_ALERT_WINDOW" serves as Cloak and "BIND_ACCESSIBILITY_SERVICE" functions as a Dagger, so it is named "Cloak and Dagger" (mantle and dagger).
According to researchers, by exploiting "draw on top" "a11y" authority, possible attacks are as follows.
◆ "draw on top"
· Inviting a click with the context hidden
· Invisible grid attack
◆ "a11y"
· Keystroke record
· Read security PIN
· Unlock with PIN input + Execute attack on off screen
· Stolen 2-step authentication tokens (including tokens such as SMS and Google Authenticator)
· Web search
◆ "draw on top" combined with "a11y"
· Silent installation of Google application & activation of all permissions
· Password stealing (users can only recognize logging in)
More details can be found on the following pages.
Cloak and Dagger: From Two Permissions to Complete Control of the UI Feedback Loop
http://cloak-and-dagger.org/
The trouble of Cloak and Dagger's attack is that it is difficult to find out that authority is being exploited by users. In the design of Google's Android application, "draw on top" is automatically allowed if the application was downloaded from the official Google Play Store, so "a11y" is activated without being noticed by the user It is said that there is a danger that it will be done. According to researchers' survey, about 10% of the top 5,000 applications frequently installed in the Google Play store have overlay function, so many applications are distributed with a11y turned on is.
Researchers at Georgia Institute of Technology have notified Google about "Cloak and Dagger", but because it is an attack exploiting Google's application design, it is considered very difficult to block vulnerabilities. What you can do with the user side is to check the authority required by the application, even if it is downloaded from the Google Play store. Fratantonio said "App developers should pay close attention to the possibility that relationships and functions will interact, based on the fact that vulnerabilities may be created by combining authority." It is.
Related Posts: