The possibility that a camouflage URL spoofing that can not be perceived by human eyes is used for phishing scams, measures at Firefox
Protocol that guarantees communication safety "HTTPSIf the notation of the URL adopted is correct, it is natural to recognize that it is a regular site, but the risk of phishing fraud which can not be seen from the URL notation of the browser is pointed out. This phishing scam uses a method evolving "homograph attack (homography attack)", it is a vulnerability inherent in the browser, it is impossible to see that human beings are fraudulent sites from screen display . As a reality problem, there is no countermeasure except "wait for the browser side response".
This Phishing Attack is Almost Impossible to Detect On Chrome, Firefox and Opera
http://thehackernews.com/2017/04/unicode-Punycode-phishing-attack.html
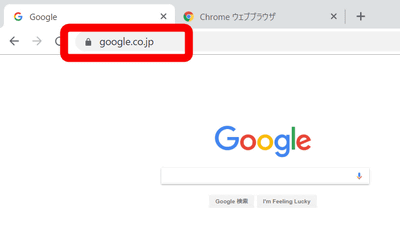
例えば、Appleの公式サイトのURLは「https://www.apple.com」で、HTTPSプロトコルが使われています。「https://」の後に続く「www.apple.com」の文字を見て「正規の」Apple公式サイトだと判断するはず。

しかし、以下のサイトはURLの表記上「https://www.apple.com」ですが、ホモグラフ攻撃によるフィッシングサイトの危険性を指摘するMohit Kumar氏が、攻撃の巧妙さを周知するために作成した特別なデモページです。
Hey there!
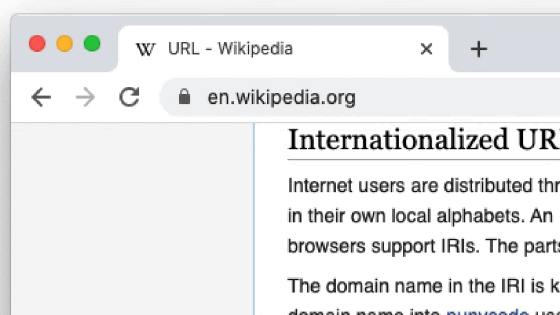
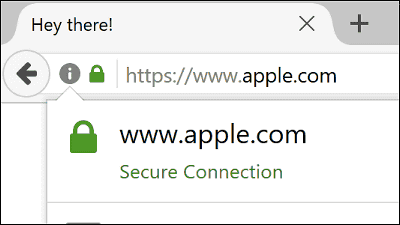
https://www.аррӏе.com/
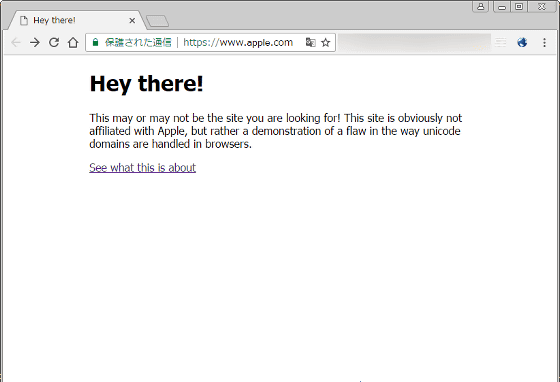
上記ページにアクセスすると、たしかにURLは「https://www.apple.com」。しかし、表示されるのはAppleの公式サイトではありません。
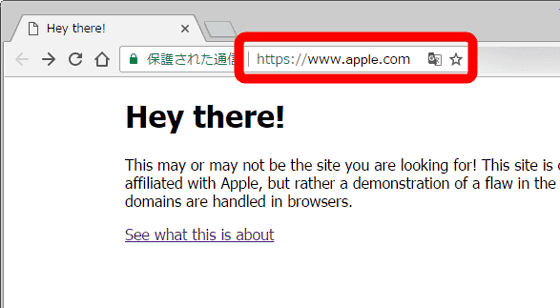
ブラウザ上のURLは同じ「https://www.apple.com」なのに、デモページ(上)とApple公式サイト(下)と異なるページが表示されるという、不思議な現象が起こっています。
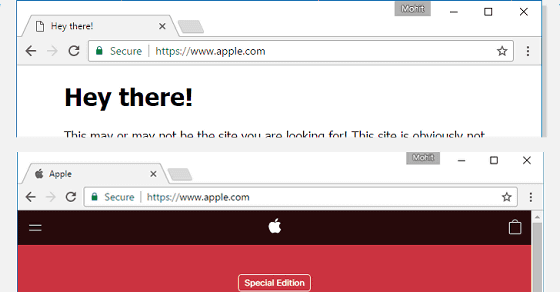
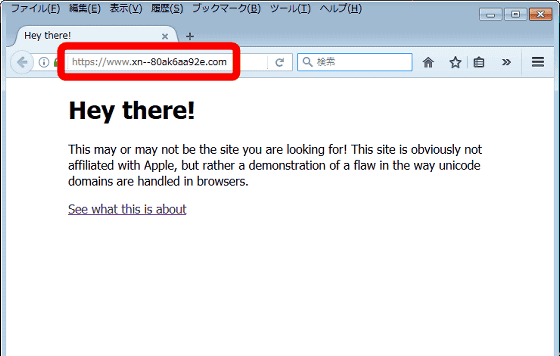
しかし、デモページのページ情報を表示すると、別のURL「https://www.xn--80ak6aa92e.com」との情報があります。
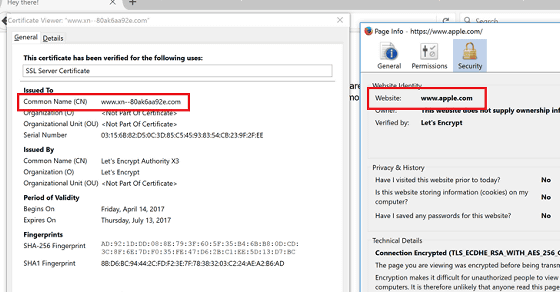
実は、先ほど「https://www.apple.com」と表示されていたデモページの真のURLは「https://www.xn--80ak6aa92e.com」。このURLがブラウザ上では「https://www.apple.com」と表示される、というのが問題のポイントです。
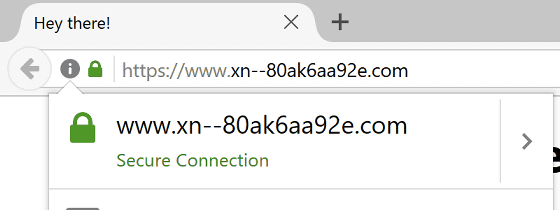
Kumar pointed out that the phishing technique is an evolutionary version of the homograph attack. About the homograph attack, it is explained clearly in the malware information office of the security software "ESET".
Can not distinguish between genuine and counterfeit homography Attack | Malware Information Office
https://eset-info.canon-its.jp/malware_info/special/detail/151001.html
Homographic attacks are also called "homomorphic attacks", and they appear to be correct URLs, but they are a camouflage that they are replaced with different letters so that characters (columns) are not known. For example, it is typical to use the alphabet "l" (lowercase letter of L) and "I" (capital of i) to distinguish it from each other. Even more sophisticated is the fraud technique of exploiting fake internationalized domain names. In the image below, the middle "o" (o) which looks like ".com" in the above domain name is the Greek letter "o" (omicron), the notation under the correct ".com" (dot com) Even if compared side by side it is too easy to distinguish.

Kumar pointed out that the evolutionary homography attack is based on a scheme for enabling strings written in Unicode to be used even in the restricted character code space in DNS "Punycode(Puniccord) "was misused. For example, the domain name "xn - s7y.co" using Punycode is converted to "short.co" in the browser.
To prevent homolog attacks on major browsers such as Google Chrome and Firefox, "Homography Protection" function which automatically converts Roman letters and confusing characters such as Cyrillic characters into ASCII characters is displayed. Unfortunately, in Chrome and Firefox's homograph protection, the protection function does not work well if all characters are replaced with Unicode characters in the same language. The demo page created by Kumar seems to disguise "xn-- 80ak6aa92e.com" as "apple.com" by using only Cyrillic Unicode characters to bypass homography protection.
URLs that are exploited for evolved homography attacks are indistinguishable from the browser display, so it is almost impossible to tell before the click if the link URL is attached before it is clicked. For this reason, the risk of being abused by phishing fraud is pointed out. Kumar has reported this vulnerability to Chrome and Firefox on January 20, 2017 and already has a countermeasure implemented in Chrome Canary 59 and will be fixed in the next "Google Chrome 58". However, in Chrome 57 and earlier there is no effective way to prevent evolutionary homography attacks.
In Firefox, by not turning on automatic conversion of Punycode without waiting for a fix update to appear, it is possible for users to take countermeasures so that distinguished sites can be distinguished.
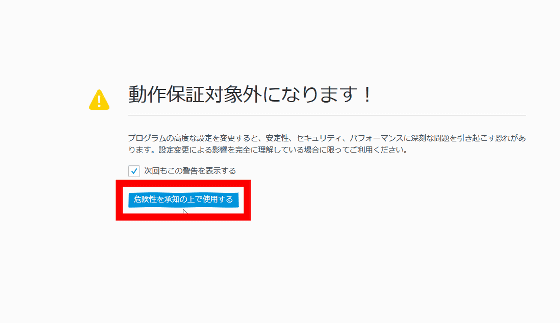
In the Firefox address bar enter "about: config".
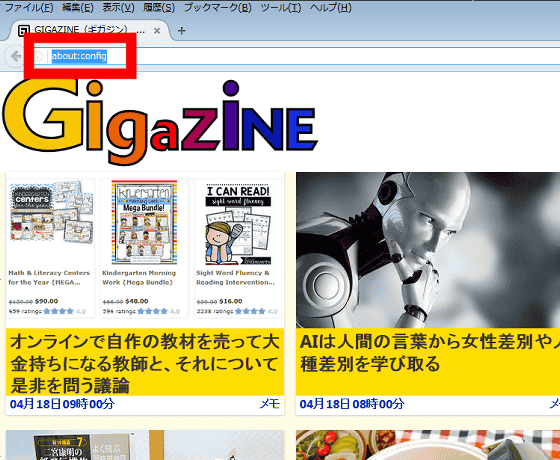
When a warning message is displayed, click "Use after understanding the danger".
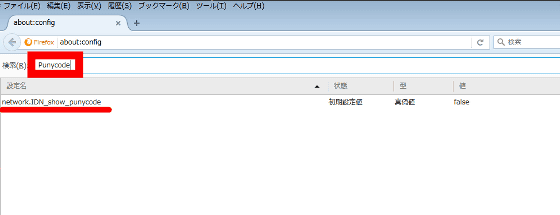
If you enter "Punycode" in the search bar, "network.IDN_show_punycode" will be displayed.
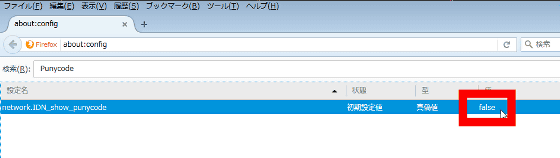
Double-click if "Value" is set to "false".
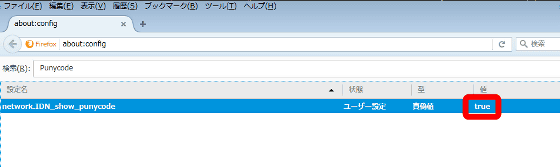
Change it to "true" OK.
After the change, Mr. Kumar createdDemo pageAccess it, OK if the address is "xn - 80ak6aa92e.com" OK. This will display the address of the disguised page that exploited Punycode as it is without being converted.
Related Posts:
in Software, Web Service, Security, Posted by darkhorse_log