Anonymous interview with teenage high school student who hacked 150,000 printers

ByBonnie Natko
A teenage hacker named "Stackoverflowin" created a printer hacking tool and caused a fuss that only 150,000 printers print ascii art in just a few hours. IT media · Motherboard contacts this hacker through anonymous messaging application "Ricochet" and hears stories about the history of hacking and the security of IoT equipment in recent years.
This Teen Hacked 150,000 Printers to Show How the Internet of Things Is Shit - Motherboard
https://motherboard.vice.com/en_us/article/this-teen-hacked-150000-printers-to-show-how-the-internet-of-things-is-shit
Motherboard:
As to why you did hacking,To warn about security flawsI told you it was. How do you do hacking and how do you think end users can protect themselves?
Stackoverflowin:
ILPD(515),IPPWe sent a print job to the printer via protocol (port 631), port 9100. In addition to this, we also used "RCE" (a vulnerability that allows hackers to execute arbitrary code remotely on the target computer) that can be used for Xerox web control. IPostScriptI was able to create my favorite print job using.
To be honest, people need to disconnect the printer from the public Internet unless it is necessary. And if you need the Internet, you should whitelist IPs / IP subnets (approve specific IP addresses and block all others) or access the local network via VPN.
I'm honestly just impressed with these printer hacks more than anything. Thanks for entertaining me during my double shift@ LmaostackPic.twitter.com/EzFXmqmDeo
Faith Kennedy (@ faithers99)February 4, 2017
Motherboard:
And did you automate the request to send to the printer?
Stackoverflowin:
That's right. I wrote a simple program in C language.
Motherboard:
On the printed paper I wrote that although it was not, "Your printer is part of a botnet". Why did you make such a message?
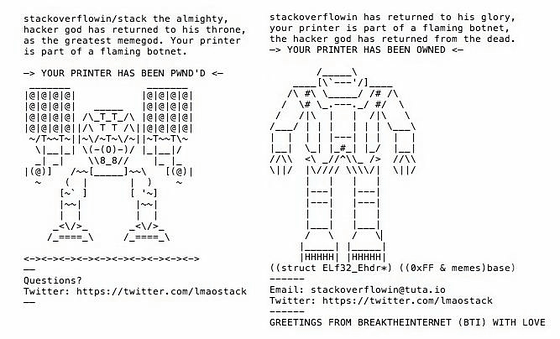
Stackoverflowin:
I thought that it was appropriate to raise people's interest in IoT security with content that first came into my mind.
Motherboard:
Was there something printed on the paper "President Putin uses complex infrastructure of BTI (break the internet)"?
Stackoverflowin:
"BTI" is a group my friends were doing in several people, mainly writing jokes that twisted security researchers. From there it was influenced and wrote in a whim, and the person who read would simply think "Russia (lol)".
@ LmaostackUm why are u hacking my printer at workPic.twitter.com/OpocSpRutm
- Summer Gale Fuss (@summer_fuss)February 4, 2017
Motherboard:
Why was the target a printer? Ruhr University Bochum just releasedA paper pointing out the vulnerability of printersOr was there something else interested, or simply because you were interested in the problem of IoT?
Stackoverflowin:
That is exactly the case, I had been looking into printers a couple of months ago and I also read a few articles. Actually, I was wondering if I could clean up the confusion of the IoT area around 2015, I also had unauthorized access to the IoT bot aiming for major fingerprint authentication.
IoT malware "MiraiWhen it came out, interestingly, nobody was aware that the problem occurred. Everyone was infected when the threat information circulated, but since many people have become a little interested in IoT security, I think that it was good as a result. However, IoT devices targeted by Mirai do not know whether people were warning effective when thinking about IoT. I thought that aiming at printers and DVDs would be more concerned about IoT security issues.
Password too high to trigger DDoS attack "Mirai" that hijacked 500,000 IoT devices 60 pieces - GIGAZINE

Motherboard:
I see. It might be that milk will go bad if you target a smart refrigerator.
Stackoverflowin:
There is a good chance that such a bad thing happens like that. Most of the devices chosen for attacks are made by Chinese development makers. This is not racial discrimination nor anything, but their code is shocking and IoT devices have multiple backdoors.
Motherboard:
Please tell me the day of hacking. I imagine this scene. It's Saturday, as you lean against the desk, she is drinking coffee seems bored. Did you decide to hack in such a case?
Stackoverflowin:
To tell the truth, I did not think that things would be so big. I was drowning when I learned that I had hacked 158,000 printers. As you say, sit on a SaturdayYoung LeanWhile listening to it, I had two sugar and was drinking coffee. Certainly on that day to improve the programming skill of the Linux kernelsandboxI think that I was tinkering until I got bored.
Motherboard:
You write the name "Michael Jensch" on the printed paper, and in the Twitter account written on the paper, I call him a "23-year old German researcher". But, in another media you talk as a British high school student?
Stackoverflowin:
The name I wrote on paper is about friends sometimes interacting. I am a high school student from the UK and I'm sure there is no mistake. I am angry high school student who messed up my future with computer science.
Motherboard:
Nobody knows you, so I have no choice but to doubt what you say.
Stackoverflowin:
No problem. I am just a high school student who can not get the results I expected at school. I think that I will probably live by doing something like this from now on.
Motherboard:
Do you think what is the reason why you can not get the results you want? What happens if the teacher knows this fuss?
Stackoverflowin:
I guess it's obsessed with programming. If you are writing code for 14 hours a day, your grades will be useless. There is just a problem, no one knows that I have a programming skill.
Motherboard:
What is your ideal occupation in the future?
Stackoverflowin:
I would like to work independently, if possible, or start up something. It is ideal for software development and security like system engineer or security consultant.
Motherboard:
Do you think dreams will come true if you go on to university?
Stackoverflowin:
I do not have the method other than going to a department I do not want to go because I do not have the necessary grades. Although it is a university for the time being, it is far from what I want to do. I wish I had a place to learn skills like programming at my age. In France, "42.fr" or "Epitech InternationalThere is nothing in England though there is.
A school free of charge, absence of a teacher, a school that nurtures students' ability to think by talking with each other "42" - GIGAZINE

Motherboard:
Is there a computer science program in England?
Stackoverflowin:
Not to say, if at all it is terrible. For example, in high school there are classes named "computer science" occasionally, but no one will be able to write programs, and everyone has no motivation in the first place. Basically "Just how quickly can you copy the contents of the book", Hackasson, conference,Capture the FlagActivities like something like that are not done at school.
Motherboard:
well understood. The experience of not being able to comprehend with anyone despite curiosity and desire to challenge is not uncommon among hackers. First of all, what if you start thinking what you think in your mind?
Stackoverflowin:
I do not know about other people. Since no one is interested, we do not talk about programming as friends. I had talked to the teacher about computing, but it was the same reaction with my friends.
Motherboard:
For example?
Stackoverflowin:
I reported a vulnerability at school responsibly, but I did not make it. I talked about how the system containing the student's private information was exposed and dangerous, but I was told the teacher "Do not harass me". This is just an example, but it is all this.
Motherboard:
If you find a way to satisfy your curiosity like this time, do you think you would send an illegal request to the printer again?
Stackoverflowin:
No, I do not feel motivated anymore, but I do not know if it is better to do. I think that this will be the last because it will be a human nature problem. It was an illegal way, but since I found that I can gather attention, I would like to grow with this in mind in the future. I would like to tell other high school student hackers that it would be better to get together with someone who has the same idea. Even if it is a niche idea, gathering the same kind of people is the best growth method. However, please be careful not to make up. It is easy to do, but I will gather some people's hate. And I will never get good results, so please do not be casual. The tricky thing involves leaving the equipment connected to the Internet, although it is not necessary.
Related Posts: